DeFi Rekt Report October 2025: $38.6 Million Lost Across 9 Exploits
October 2025 saw a total of $38.63 million lost across nine distinct security incidents in both centralized and decentralized platforms.
We spent 2 years on creating the Largest Crypto Hacks Database with more than 3,160 hacks being added and manually verified by our on-chain researchers and solidity engineers. Our on-chain investigations have been mentioned by Forbes, Bloomberg, Wall Street Journal, and Blockworks.
We thought that we had already seen every type of Rug Pull and Scam possible.
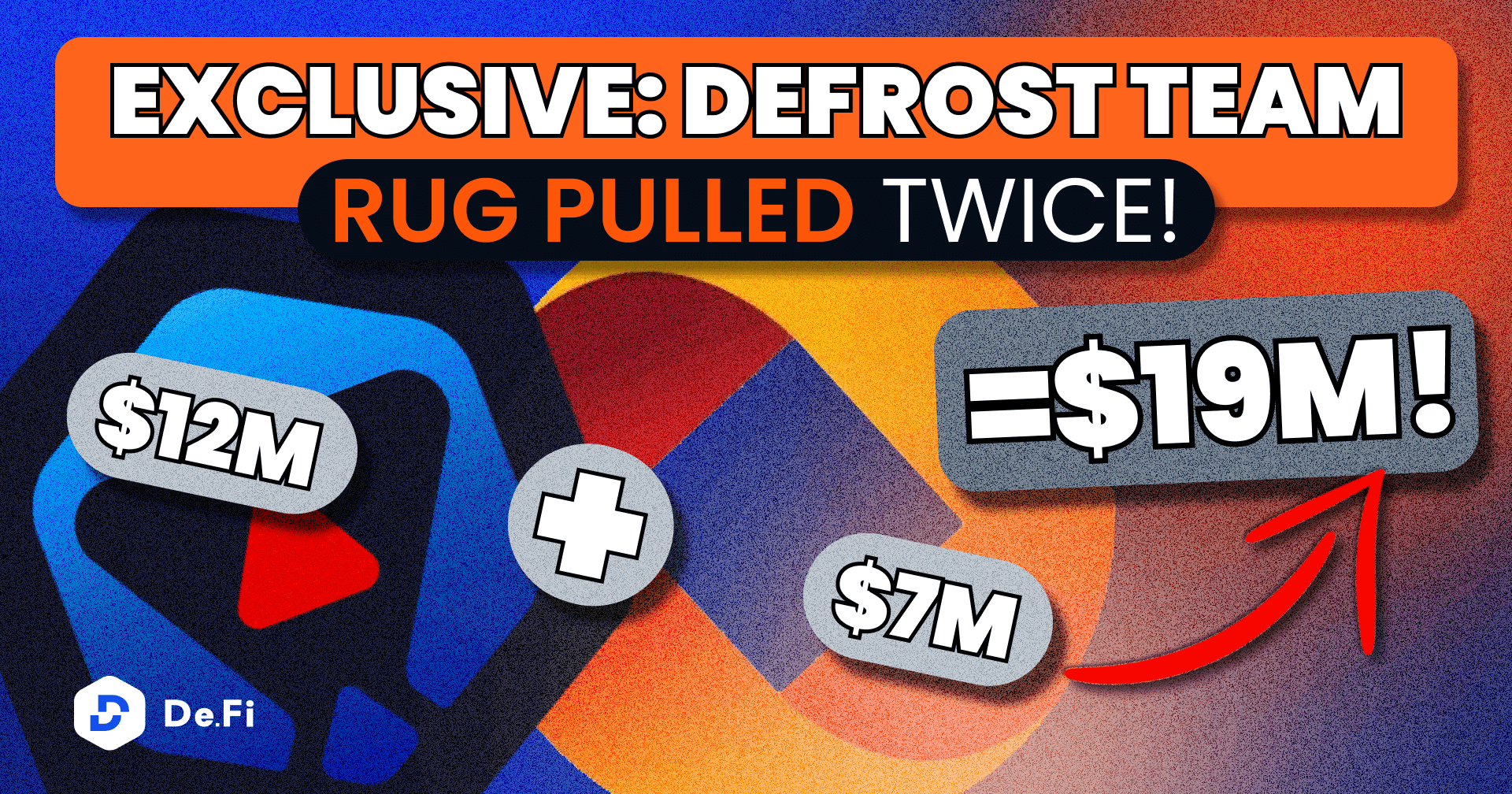
But then Defrost Finance happened. And decided to make a little Christmas gift for its Community — rug pull them for $12M.
The way they have done this might be the most sneaky way to rug pull users that DeFi has ever seen.
On December 24th, the World has seen the following tweet by Defrost Finance:
](https://de.fi/blog/wp-content/uploads/2023/06/0Atir5m31uRtt_iES.png)
Defrost claimed that their V2 smart contract was exploited, and that attacker used a flash loan to withdraw funds.
However, the V1 contracts had been hacked as well resulting in the $12M loss. The oracle address in the protocol’s collateral vaults was replaced with a malicious one. That triggered liquidations of collateralized user funds.
0x3cd5854fe3a13707b7882d8290d3cae793a7751a — the Address that called setOracleAddress() was added as the Origin address by deployment of the DefrostFactory address:
](https://de.fi/blog/wp-content/uploads/2023/06/1ytjDWDsBwSATQqmJJgDEfA.png)
The creator of the multisig wallet, which has to approve the oracle replacement function before it executes, is the same address that requested the oracle replacements:
](https://de.fi/blog/wp-content/uploads/2023/06/1ak_AhE0fYaJkrGQvDhArWg.png)
This is an application for signing the oracle replacement by the multisig:
](https://de.fi/blog/wp-content/uploads/2023/06/1VeBR_QvEvWIKrAYDmgYrnw.png)
Addresses that were signing oracle replacements in the protocol’s vaults are:
This is one of the oracle replacement transactions:
](https://de.fi/blog/wp-content/uploads/2023/06/0t3AC4w5-0qS_rFg6.png)
Exactly 1 month before rug pulling its users using the oracle vulnerability, Defrost Finance has insured themselves with 2 Crypto Insurance Providers: **Insurace and [Degis Insurance](https://mobile.twitter.com/projectdegis)** … against “Oracle Failure”.
What a coincidence! 🤦♂️
](https://de.fi/blog/wp-content/uploads/2023/06/0Ji0c2HgCc6S53vOS.png)
](https://de.fi/blog/wp-content/uploads/2023/06/0IODPpnl-_IMPVCq1.png)
So, back to DeFrost. Just as we did previously with Bundles, YFFS, PancakeBunny, Deus, and Alpha Homora cases – we are writing this article to inform the Community about the concerns we have about this project. As a premise, we would directly say that it seems like they are hiding.
But let’s start from the beginning.
Since 2020, we at De.Fi, have performed more than 60+ Security Audits, in each among other things we also analyze the functions / hints if the project retains the ability of scamming its investors including
1 year ago, De.Fi released a 120-page audit on Defrost Finance — **click here to see the full pdf file.** On page 33rg, we’ve stated the following:
“The Origin EOAs can replace the Oracle address. Collateral asset prices in the vaults of Defrost Finance depend on oracle contracts. In case the new oracle is insecure and can cause a sharp and unpredictable change in the price of an asset, this can lead to liquidation of user collaterals.”
](https://de.fi/blog/wp-content/uploads/2023/06/0vdCx5MUxqEq-eYFp.png)
We described the exact smart contract vulnerability that Defrost Finance used to manipulate with fake oracle and rug pull its users. And warned people about it. Accordingly, it was indicated by **Coindesk**, where the journal has featured our Audit and the warning about the crucial vulnerability that we stated in it:
](https://de.fi/blog/wp-content/uploads/2023/06/0ZXrIgiX8noG30D49.png)
Apart from this exact vulnerability that was used to rug pull users, we’ve found 151 issues, 13 of which were Critical and High Risk. Those who read our Audit and withdrew funds from Defrost had saved their funds.
](https://de.fi/blog/wp-content/uploads/2023/06/0b_FIIdjarIxPR0wz.png)
We have got in touch with Defrost Finance team 2 times:
After the PeckShield’s and our investigations that we’ve **posted on Twitter**, it was clear for the Defrost Finance team that they’ve got caught, and now there is no way for them to simply launder the funds and live in peace in the Bahamas.
That’s how they started to think of ways of returning funds back to the users.
On the next day after the exploit, they proposed a “hacker” a 20% reward for returning the “stolen” funds:
](https://de.fi/blog/wp-content/uploads/2023/06/0VbxQ-5C00STMdv7c.png)
And on the next day, the “hacker” has returned all the stolen $12M:
](https://de.fi/blog/wp-content/uploads/2023/06/0MtVTz07jXTKtLaB.png)
Following the bounty hacking standard it’s IMPOSSIBLE to get a resolution so fast. The dealing process in the bounty program is much longer.️
](https://de.fi/blog/wp-content/uploads/2023/06/0HUdyqTOVo3T-lsdc.png)
However, the Developers Behind the Defrost Finance had a more successful RUG PULL in their Career.
The Developers of Defrost Finance are the same people as the Developers of Phoenix Finance (FinNexus), whose smart contract’s private key has “leaked”, which has resulted in a $7M loss in 2021. Following our research, considering all the inputs, there is a high chance that it was a rug pull, and the private key didn’t just “leak”.
)](https://de.fi/blog/wp-content/uploads/2023/06/1avDqb_GiJJTovJsRP8MazA.png)
The connection between Phoenix Finance (FinNexus) and Defrost Finance can be found on Defrost’s GitHub:
](https://de.fi/blog/wp-content/uploads/2023/06/1TLGm8RlzNbWSc2AnHE3unw.png)
As pointed by a Twitter User — after the FinNexus got exploited, they forked $FNX to the Phoenix Finance $PHX, and used part of the rugged money to fund the growth of Defrost Finance, to rug pull it again:
](https://de.fi/blog/wp-content/uploads/2023/06/0HjW_KvlqIFRlVz7y.png)
In this article we provided all the data needed to prove the rug pull fact behind the Defrost Finance’s $12M scam, showing the connection between Defrost Finance and Phoenix Finance (the project rug pulled in 2021).
Today, our research got featured on CoinTelegraph: https://cointelegraph.com/news/defrost-finance-breaks-silence-on-exit-scam-accusations-denies-rug-pull
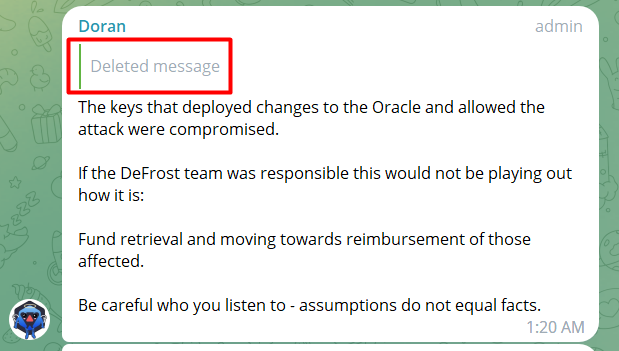
After this, we got in touch with Defrost Team asking them to KYC again. Unfortunately, no reply has come from its founders.
What Defrost Finance started doing instead is just banning everyone sending the link to this article in chat. And liying about the “private key getting compromised” — nonsense.
We, at De.Fi, have been fighting DeFi Scams for years, as our main goal is for DeFi to become a safer and a more convenient place for a retail investor. We believe that only by being safe and fully trustless, DeFi can be mass adopted and we can finally go Bankless!
That’s why we’ve written the Amazon’s Bestseller: **“The Wall Street Era is Over” — the most comprehensive guide on Web3, and how to save your crypto funds.**
](https://de.fi/blog/wp-content/uploads/2023/06/0OCO1mHmlr79jnCYx.png)
Have comments or opinions? Let us know!
Check out other articles from the Saga series:
October 2025 saw a total of $38.63 million lost across nine distinct security incidents in both centralized and decentralized platforms.
The third quarter of 2025 marked yet another turbulent period for the DeFi and wider crypto ecosystem, with $434,124,000 lost to exploits, scams, and security failures across both centralized and decentralized platforms.
June 2025 witnessed another alarming month for Web3 security, with a total of $114,768,000 lost during 11 separate attacks
May 2025 saw both DeFi and CeFi security once again under attack, with $275,953,000 lost across just 8 recorded incidents
April 2025 witnessed a large escalation in exploit volume and value, with a massive $5,919,684,000 being stolen in 10 confirmed events.
Q1 2025 marked one of the worst quarters in blockchain exploit history, with total recorded losses topping $2,052,584,700 across 37 incidents
© De.Fi. All rights reserved.