What is Permit2? - Contract Guide + How to Revoke
A smart contract originally conceived by Uniswap, Permit2 manages the approval of token transfers via gasless signatures.
The first quarter of 2024 has concluded with an upswing in crypto market sentiment, marking another significant period for the decentralized finance (DeFi) ecosystem, both in terms of growth and the challenges it faces. DeFi continues to evolve rapidly, but with this pace of development comes an increase in the sophistication and frequency of attacks against the ecosystem. This report, compiled from data in the De.Fi REKT database, aims to more closely examine the key incidents that impacted the DeFi ecosystem over the past three months.
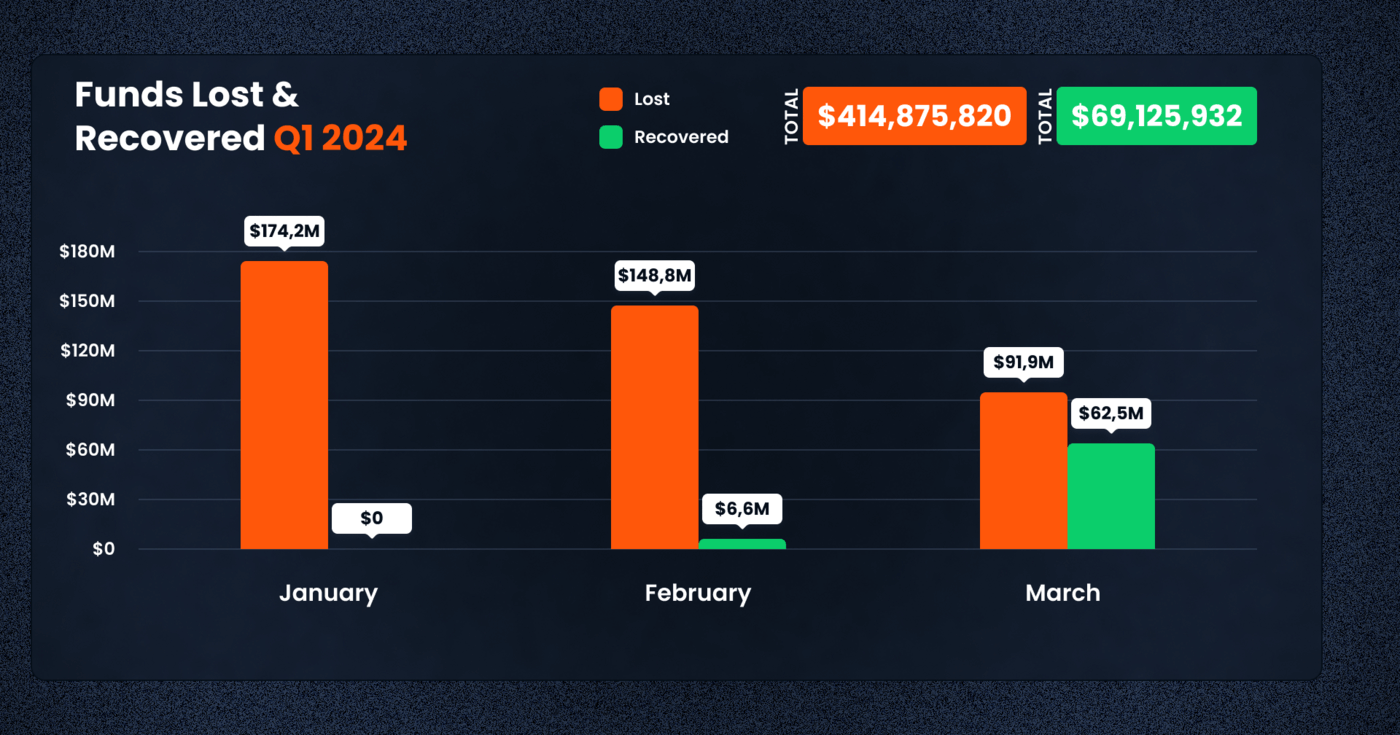
During Q1 2024, the decentralized finance (DeFi) landscape encountered substantial challenges, with total losses amounting to $414,875,820 across a range of exploits and security incidents. This represents an 8% increase in financial losses compared to Q1 2023, where the sector witnessed $372,124,849 in lost funds. However, the first quarter of 2024 also highlighted a considerable uptick in recovery efforts, with $69,125,932 being successfully reclaimed by victims and platforms. This significant recovery effort marks a substantial improvement over Q1 2023, where only $1,486,726 was recovered, illustrating the DeFi community’s increased effectiveness in counteracting malicious activities and bolstering the ecosystem’s overall security and resilience.
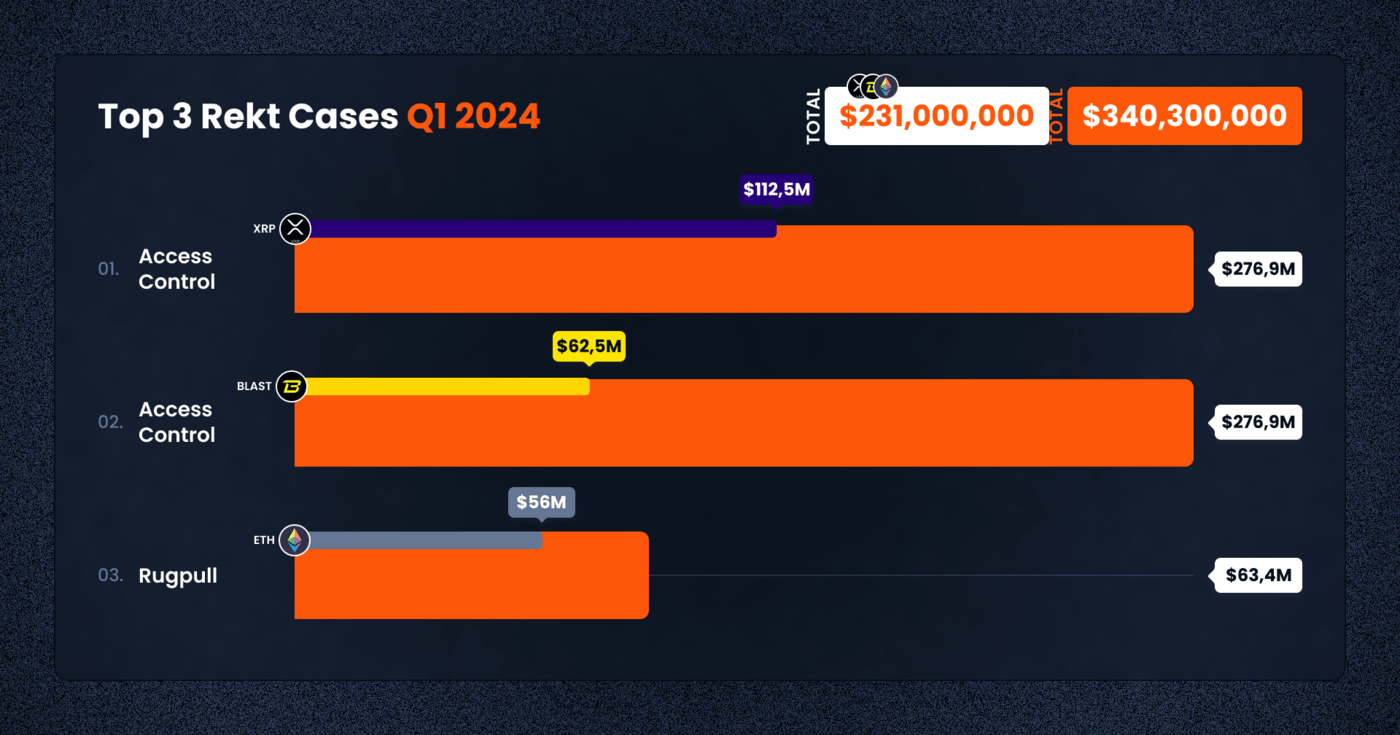
The quarter was not without its high-profile incidents, with substantial losses reported across several projects and platforms. The Chris Larsen EOA case was the most significant, with a massive loss of $112,500,000, illustrating the vulnerabilities that even individual high-net-worth accounts face. Munchables and BitForex followed, with losses of $62,500,000 and $56,000,000 respectively, highlighting critical security issues in token projects and exchange platforms.
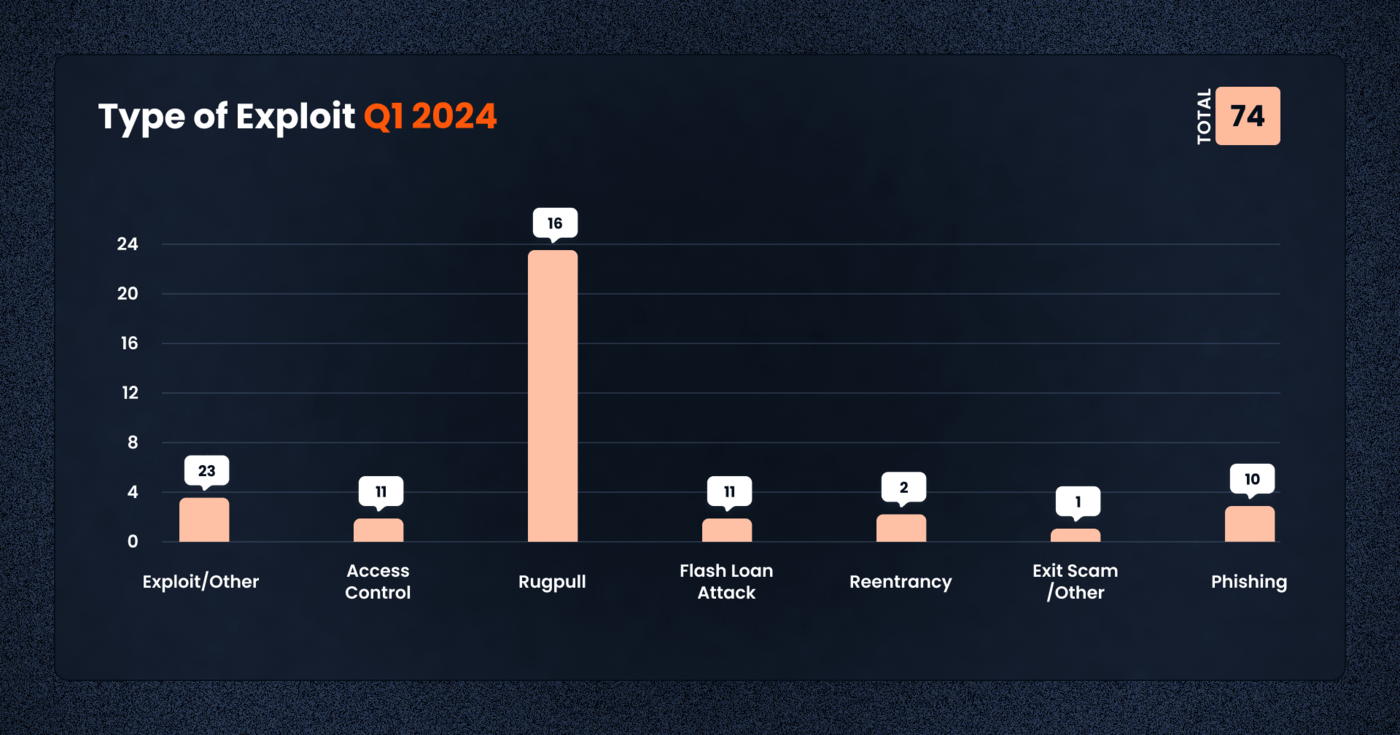
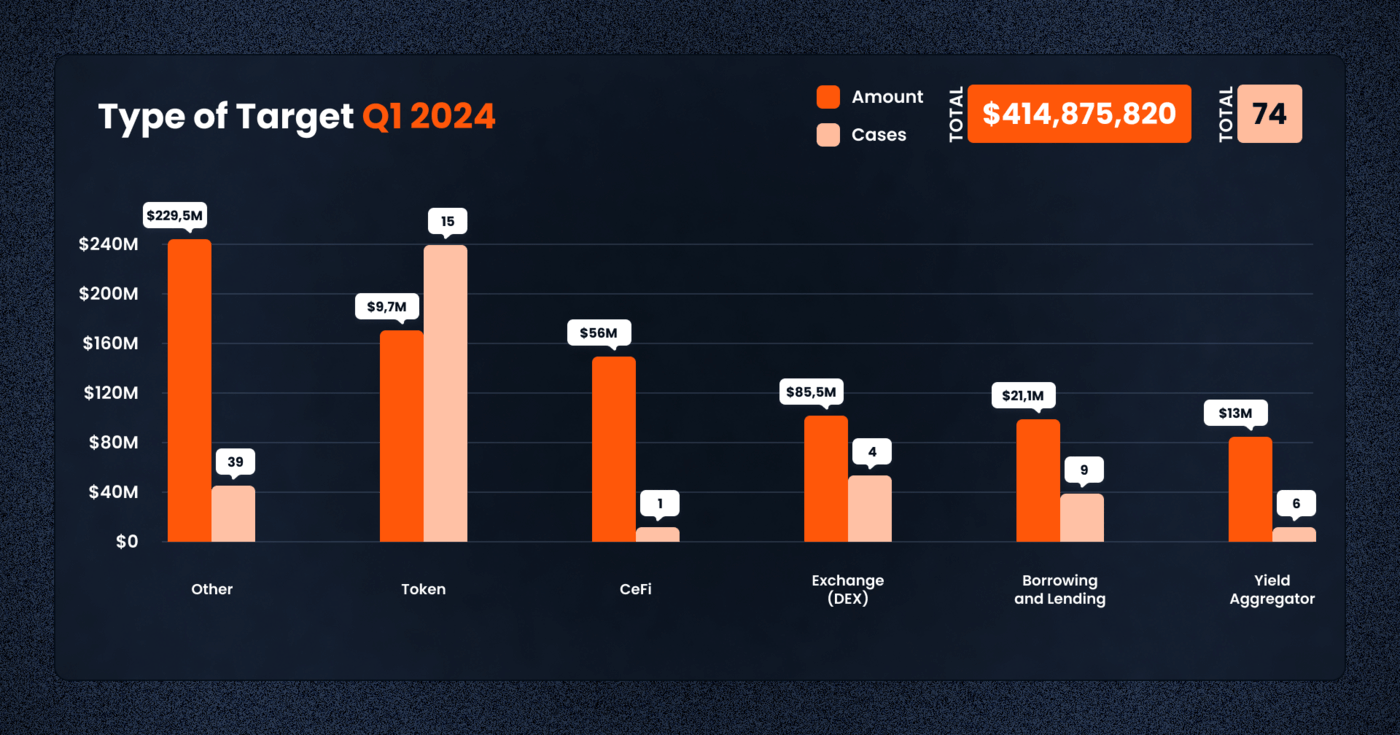
The trend of exploits in Q1 2024 reveals a diverse array of attack vectors and targets. Access control issues continued to be a prevalent concern, leading to significant losses across 11 cases totaling over $175,000,000. This underscores the ongoing need for robust access management and permissions regimes to prevent unauthorized access.
Rug pulls, a form of deceit or exit scam where developers or insiders withdraw a project’s liquidity to make off with users’ funds, maintained their presence as a significant threat within the DeFi ecosystem, with 16 reported cases. These rug pulls not only result in direct financial losses for investors but also severely undermine trust in the burgeoning DeFi space. The tactic exploits the decentralized and often anonymous nature of blockchain projects, making it difficult for affected users to seek recourse.
Similarly, flash loan attacks, involving the exploitation of DeFi lending protocols to manipulate asset prices for profit, were executed in 11 instances. These attacks leverage the unique capabilities of DeFi for uncollateralized loans, allowing attackers to borrow, manipulate market prices through large trades, and then profit off these artificially induced price movements, all within a single transaction block. This type of exploit highlights the innovative but risky functions at the heart of DeFi’s liquidity and lending protocols, as well as the challenge developers face to fortify their platforms against such attack vectors.
An analysis of the attacks by chain shows that Ethereum (ETH) and Binance Smart Chain (BSC) were among the most affected, with 30 and 15 cases respectively, reflecting their prominent roles in the DeFi ecosystem.
In terms of categories, borrowing and lending platforms, along with decentralized exchanges (DEXs), were particularly impacted, losing $21,124,522 and $85,489,732 respectively. These figures not only point to the critical roles these platforms play in the DeFi ecosystem but also to their attractiveness as targets for malicious actors seeking to exploit their complex interactions and deep liquidity pools.
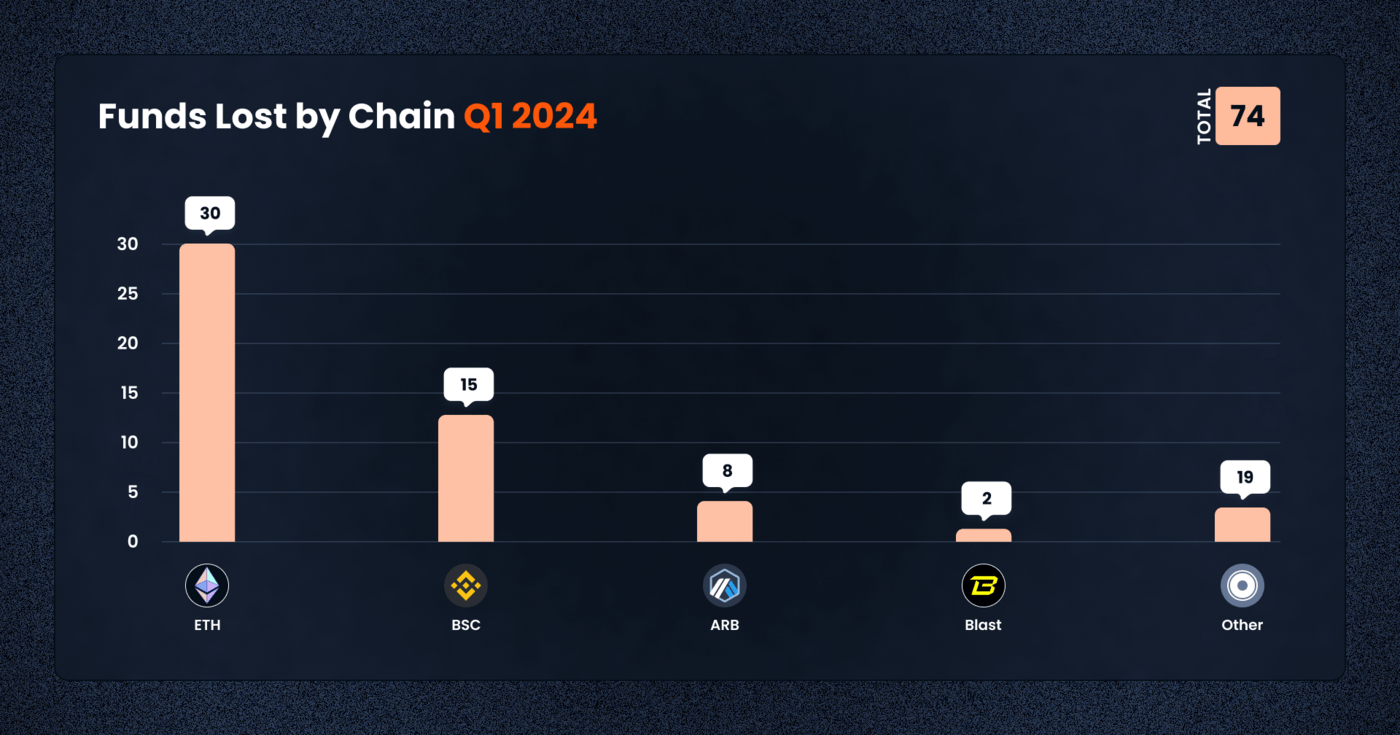
The first quarter of 2024 brought to light the vulnerabilities across various blockchain networks, with a total of $414,875,820 lost in exploits across different chains. Below is a breakdown of the losses by chain for Q1 2024:
1. Ethereum (ETH): Continuing to bear the brunt, Ethereum saw the most frequent losses, with 30 incidents occurring. This significant figure emphasizes Ethereum’s pivotal role in the DeFi sector, attracting malicious entities due to its vast array of DeFi projects and large user base.
2. Binance Smart Chain (BSC): BSC was not spared, suffering losses across 15 cases. Known for its user-friendly approach and low transaction fees as an Ethereum alternative, BSC’s popularity also makes it a prime target for exploits, highlighting the need for increased security measures on the platform.
3. Arbitrum: As a layer 2 scaling solution for Ethereum, Arbitrum experienced losses from 8 incidents, illustrating that even networks designed to enhance scalability and efficiency are susceptible to security breaches.
4. Blast: A relatively newer chain, Blast has skyrocketed to become one of the largest DeFi ecosystems by total value locked (TVL). Blast encountered losses totaling $62,500,000 from just 2 cases. This disproportionate figure indicates that emerging chains, despite their smaller size and reach, can also face significant security challenges.
5. Other Chains: With 15 cases across various other chains, this category encapsulates the widespread nature of DeFi exploits beyond the mainstream networks. It highlights the universal threat faced by the entire blockchain ecosystem, regardless of size or reputation.
The diversity of chains affected in Q1 2024 reflects the expansive reach of DeFi and the corresponding spectrum of risk across the ecosystem. From established networks like Ethereum and BSC to newer entities like Blast and layer 2 solutions like Arbitrum, the data from this quarter serves as a prominent reminder of the ongoing battle against DeFi exploits.
In Q1 2024, the DeFi ecosystem demonstrated a significant improvement in the recovery of stolen funds, with over $69 million successfully reclaimed, marking a contrast to the $1.4 million recovered in Q1 2023. This notable increase reflects the advancements and concerted efforts in the field of asset recovery within the blockchain community. Key factors contributing to this success include enhanced detection and response procedures and community collaboration in on-chain tracing of funds.
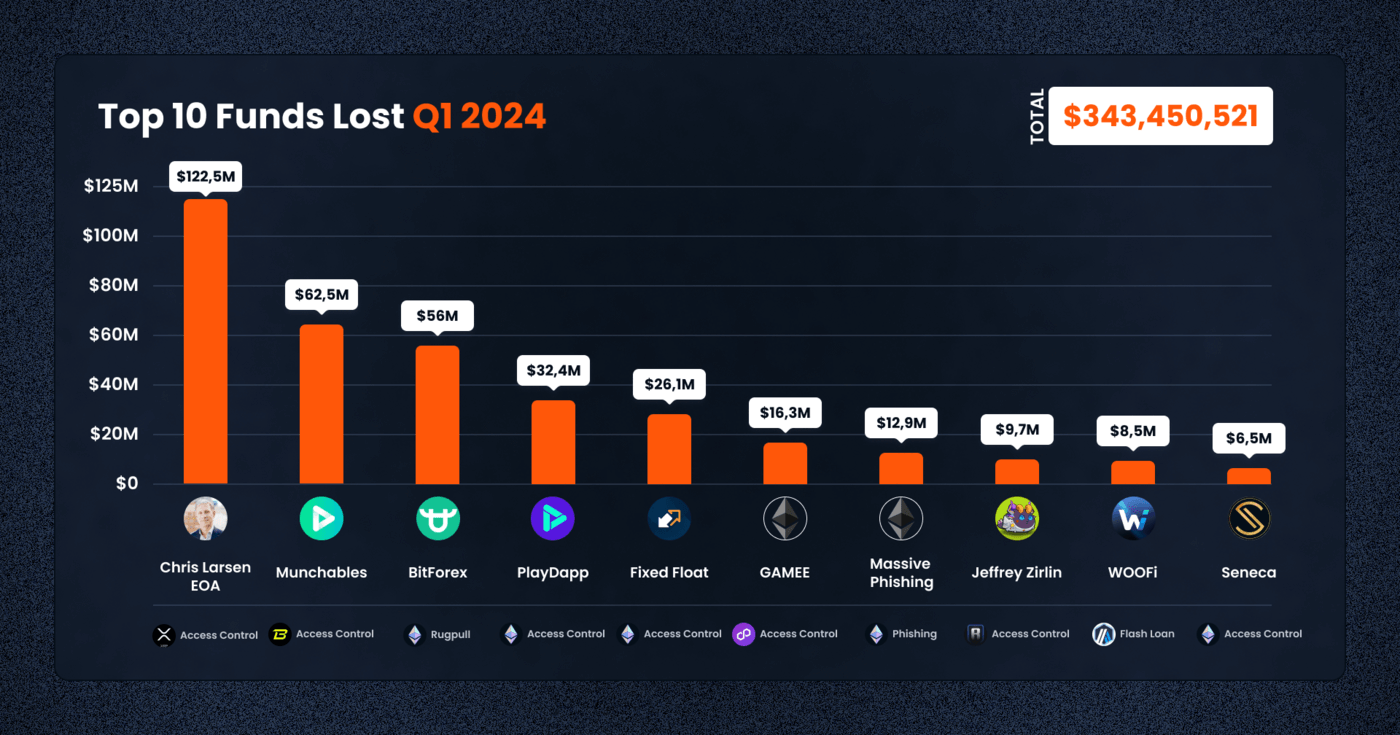
1. Chris Larsen EOA – $112,500,000
On January 30, 2024, Ripple’s co-founder Chris Larsen experienced a significant loss when his personal account on the Ripple chain was compromised, leading to the theft of 213 million XRP tokens. The stolen funds, valued at approximately $112.5 million, were laundered through several exchanges, including Kraken, KuCoin, Gate, Binance, MEXC, FixedFloat, Whitebit, Huobi, EXMO, and others. The incident was first noticed by blockchain detective zachxbt, prompting Larsen to clarify that the stolen funds were from his personal wallets, not Ripple’s project wallets.
2. Munchables – $62,500,000
The Munchables protocol suffered a significant breach on March 27, 2024, resulting in the draining of 17.4K ETH, equivalent to $62.5 million. The exploit was executed by directly calling a function on the contract and withdrawing Ether. The nature of the exploit, between a potential rug pull and an access control vulnerability, remains unclear due to unverified source code. Remarkably, all funds were returned shortly after to a protocol-associated multi-signature wallet, raising questions about the attacker’s motives and the protocol’s security practices.
3. BitForex – $56,000,000
BitForex, a cryptocurrency exchange, conducted an exit scam in late February 2024, with suspicious outflows amounting to approximately $56 million across multiple blockchains. Attempts to access the platform were blocked, and the exchange ceased all withdrawal processes, leaving users in turmoil. The stolen assets were traced to multiple BitForex hot wallets across Ethereum, Bitcoin, and TRON networks.
4. PlayDapp – $32,350,000
PlayDapp, an Ethereum-based play-to-earn game, was hit by an exploit due to compromised private keys between February 9-12, 2024. The attackers unauthorizedly minted and then stole 1.79 billion PLA tokens, translating to a financial loss of around $32,350,000. The attacker managed to add a new minter for the PLA Token, minting and converting a portion of the tokens into USD. The funds were dispersed across the Polygon chain, Binance exchange, and retained in the scammer’s addresses.
5. Fixed Float – $26,130,157
The FixedFloat cryptocurrency exchange was exploited on February 16, 2024, leading to the theft of 409.304 BTC and 1,728.48 ETH, cumulatively valued at about $26,130,157 USD. The stolen Bitcoin and Ethereum were distributed among multiple addresses, highlighting the vulnerability of exchange platforms to targeted attacks. The incident remains under investigation, with limited details provided by FixedFloat.
6. GAMEE – $16,352,814
Animoca Brands’ GAMEE token on the Polygon chain faced a dire situation on January 22, 2024, when a compromise involving unauthorized GitLab access and a deployer key resulted in the transfer of 600 million GMEE tokens. The attacker exploited the recoverERC721s() function, transferring 600 million GMEE tokens and swapping them for MATIC. A portion of these tokens was bridged to Ethereum and deposited into Tornado Cash.
7. Phishing – $12,917,550
A coordinated phishing attack on January 23, 2024, led to the theft of $12,917,552 in assets, including ETH, SUPER, and aEthWETH, from several victims across both Binance Smart Chain and Ethereum. The attackers deployed malicious contracts on the Binance Smart Chain and Ethereum, tricking users into executing transactions that drained their assets.
8. Jeffrey Zirlin – $9,700,000
Jeffrey Zirlin, known as “Jihoz” and co-founder of Axie Infinity, reported the compromise of two personal wallet addresses on February 23, 2024. The attacker managed to transfer assets to Ronin WETH and then to the Ethereum mainnet, utilizing the Axie Infinity:Ronin Bridge, culminating in losses around $9,700,000. This incident highlights the critical importance of securing private keys to prevent unauthorized access.
9. WOOFi – $8,500,000
WOOFi Swap on the Arbitrum network was targeted in a sophisticated exploit involving flash loans and price manipulation on March 5, 2024, resulting in approximately $8.5 million in losses.
The attacker leveraged flash loans to exploit the sPMM algorithm of WooPPV2 contract, manipulating prices and extracting significant value. The attack was contained within 13 minutes, but not before substantial losses were incurred. The exploit exemplifies the vulnerabilities associated with flash loans and the need for DeFi platforms to fortify their defenses against such innovative attack vectors.
10. Seneca – $6,500,000
Seneca Protocol was exploited on February 28, 2024, due to a smart contract vulnerability on both Ethereum and Arbitrum. The exploit involved arbitrary external calls within the protocol’s contracts, allowing attackers to drain assets by manipulating the performOperations function. Despite the sophisticated nature of the attack, a large portion of the stolen funds was recovered, totaling $5,300,000.
Closing Thoughts
With a resurgence in interest in the crypto space, it is not surprising that we also saw losses increase year-on-year in Q1 2024. However, it also showcased the Web3 community’s capability to recover a significant portion of the lost funds, amounting to over $69 million. This recovery effort not only demonstrates the effectiveness of post-incident response strategies but also highlights the importance of collaborative efforts within the community to mitigate the impacts of such exploits.
The diverse nature of the attacks observed, from access control breaches to phishing and flash loan attacks, reiterates the need for continuous improvement in security practices. It is imperative for projects within the DeFi ecosystem to prioritize security audits, employ rigorous access control measures, and foster user education. One such tool that allows anyone to carry out a quick security audit and assess the safety of a particular smart contract is the De.Fi Scanner, a tool that has already prevented a multi-million sum from being lost to malicious actors. Here at De.Fi, we are continuing to enhance our Web3 antivirus suite, with exciting updates to come. After all, as the sector continues to mature, so too must the strategies employed to protect it, ensuring that DeFi can realize its full potential without compromising on the security and trust of its users.
A smart contract originally conceived by Uniswap, Permit2 manages the approval of token transfers via gasless signatures.
On that front, DeFi wallets are in high demand and Rabby Wallet is an option that's quickly gaining mindshare. But the fact of the matter is, Rabby is only one in a sea of wallet providers. Users must carefully weigh their options to know whether or not it's the right choice.
During Q2 of 2024, we noticed a significant increase in crypto losses caused by hacks and scams - the total was $430,118,000, which is much higher than what we observed during this period last year (a loss of $204,308,280).
In the rapidly expanding universe of web3 and decentralized finance (DeFi), selecting a reliable and secure wallet is crucial. Rainbow Wallet has emerged as a popular choice, especially for those new to the crypto world.
In this blog, we'll walk through what Gnosis token approvals are and how you can audit + revoke them using the free De.Fi Shield tool.
During Q1 2024 ... total losses amounting to $414,875,820 across a range of exploits and security incidents.
© De.Fi. All rights reserved.