DeFi Rekt Report October 2025: $38.6 Million Lost Across 9 Exploits
October 2025 saw a total of $38.63 million lost across nine distinct security incidents in both centralized and decentralized platforms.
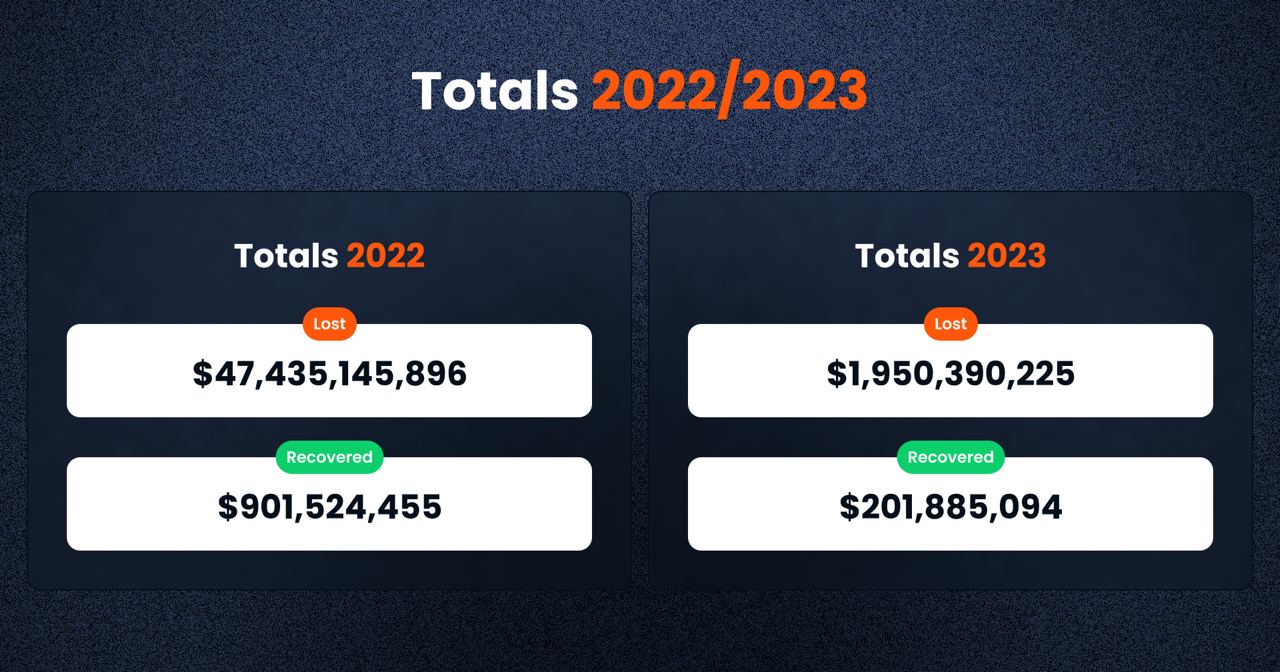
In 2023, the DeFi industry saw some substantial losses, culminating in a total loss of approximately $1.95 billion over the year. This amount, though dispersed across various incidents, underscores the persistent vulnerabilities and challenges within the DeFi ecosystem. In our annual analysis, we look into these incidents, shedding light on key trends, the distribution of losses across different blockchain networks, and the diverse types of exploits that continue to threaten the security and stability of the DeFi sector.
In a year that continued to challenge the resilience and security of the decentralized finance (DeFi) and crypto sectors, 2023 stood as a testament to both the ongoing vulnerabilities and the strides made in addressing them, even as interest in the space was relatively muted by the ongoing bear market in the first half of the year.
The year 2023, in its entirety, witnessed significant amounts lost in the Web3 space. While the total losses in 2023 amounted to a still-large figure of close to $2 billion, it marked a decrease from the losses incurred in 2022, which saw north of $47 billion being lost.
This reduction can be attributed to a combination of improved security protocols, heightened community awareness, lower activity in the space as a whole. However, it is crucial to note that despite these improvements, the losses remained high, indicating a continuous battle against security breaches and fraudulent activities, bull or bear market.
Alongside the lower losses in 2023, the amount of funds recovered in 2023 was also correspondingly lower at $201.8 million, as compared to 2022’s figure of $901.5 million. That being said, in percentage terms, a higher percentage of losses in 2023 was recovered as compared to in 2022 (~10% vs ~2%), indicating greater effectiveness in recouping losses from exploits and hacks.
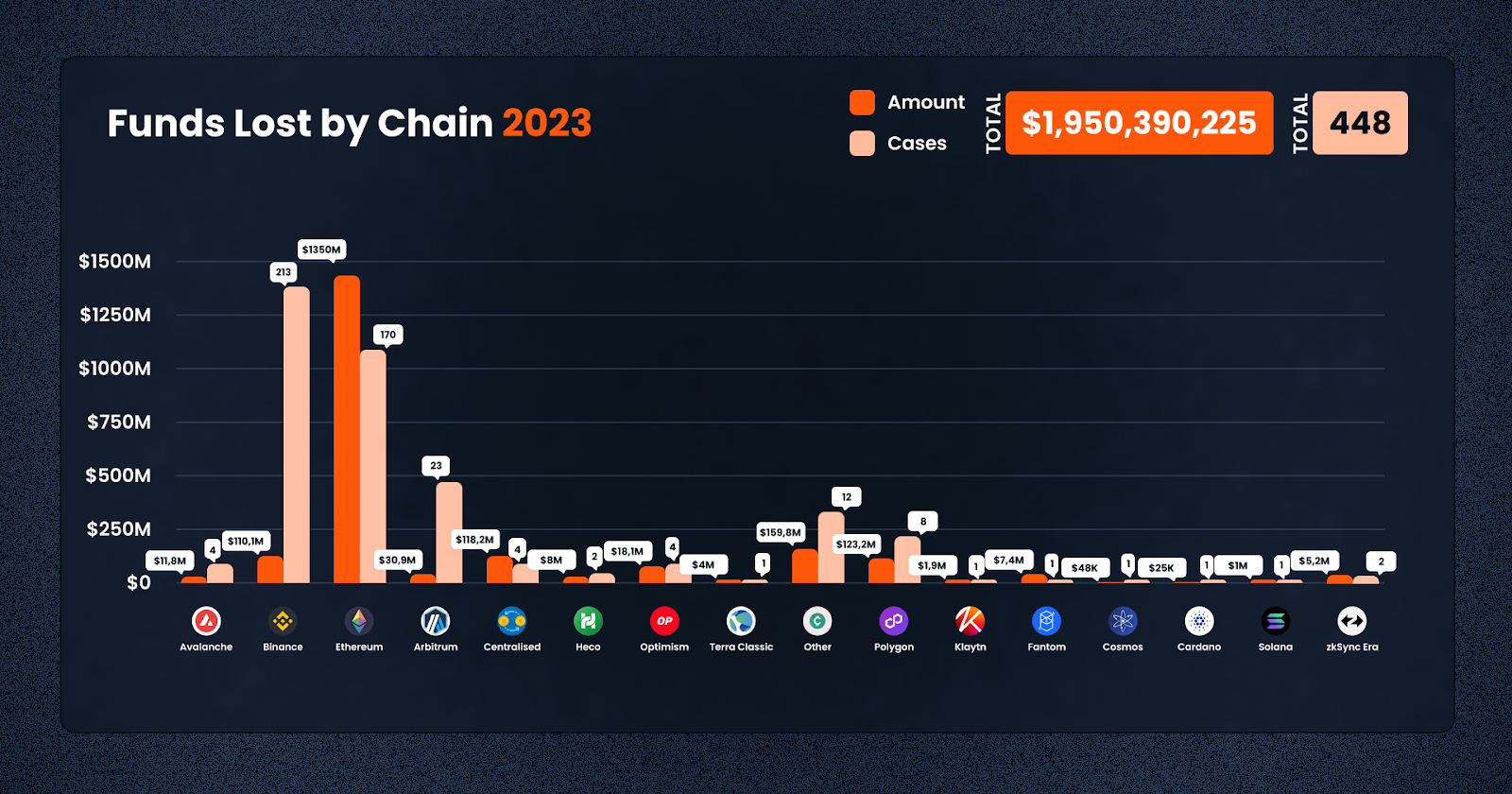
In 2023, the DeFi and crypto sectors experienced a wide distribution of losses across various blockchain networks, each differing in the total amount lost and the number of incidents. The detailed data from the year provides a clearer understanding of the specific challenges faced by each chain.
Ethereum, the most prominent network in DeFi, suffered the most significant losses. The total amount lost on Ethereum was approximately $1.35 billion, spread across 170 cases. This high figure reflects Ethereum’s status as the leading platform in terms of total value locked and its appeal to malicious actors due to its extensive ecosystem and high-profile projects.
Binance Smart Chain (BSC) also faced substantial losses, taking the crown for the highest frequency of exploits this year, with about $110.12 million lost in 213 incidents. Despite being known for its high throughput and low transaction fees, BSC’s growing popularity has made it a target for various exploits, demonstrating the scale of challenges in ensuring security on high-activity networks.
In contrast, smaller or emerging networks like Solana and zkSync Era faced fewer incidents, but still notable losses. Solana had a loss of $1 million in a single case, while zkSync Era saw losses amounting to $5.2 million across two incidents.
Furthermore, losses on centralized platforms were significant, totaling approximately $118.21 million across 4 cases. This figure underscores the fact that centralized exchanges and platforms are also vulnerable to attacks and contribute substantially to the overall loss figures in the crypto and DeFi space.
Overall, the total losses across all chains in 2023 amounted to $1.95 billion over 448 cases – this means that on average, there is more than 1 case every day. This data not only illustrates the scale of the problem across different blockchain networks but also highlights the need for continued advancements in security measures and protocols to protect assets in the ever-evolving DeFi and crypto landscape.
In November 2023, the DeFi space witnessed a variety of exploit types.
Access Control Vulnerabilities
A key issue in November 2023 was the exploitation of Access Control mechanisms. Five incidents of this nature resulted in an overwhelming loss of $280,675,344. These events highlight the crucial need for more stringent access controls and thorough security audits in DeFi protocols. The high-value losses in these cases underscore the devastating impact that lapses in access control can have on the entire ecosystem.
Rugpulls
Rugpulls continued to be a common tactic employed by malicious actors, with five instances causing a loss of $423,003. This type of exploit remains a significant concern, particularly in newer or less vetted projects. It underscores the ongoing need for rigorous due diligence and investor education. Platforms like De.Fi Scanner play a critical role in identifying potential risks associated with emerging tokens before investors commit their funds.
Phishing and Flash Loan Attacks
The DeFi space also saw phishing attacks and flash loan exploits. A single phishing incident led to a loss of $768,000, reinforcing the necessity for heightened awareness and preventative measures against such deceptive practices. Additionally, two flash loan attacks, a relatively newer exploit method in DeFi, resulted in losses totaling $2,181,126. These incidents highlight the risky nature of DeFi tools.
Key Attack Vectors
Common Exploits in the DeFi and Crypto Space in 2023
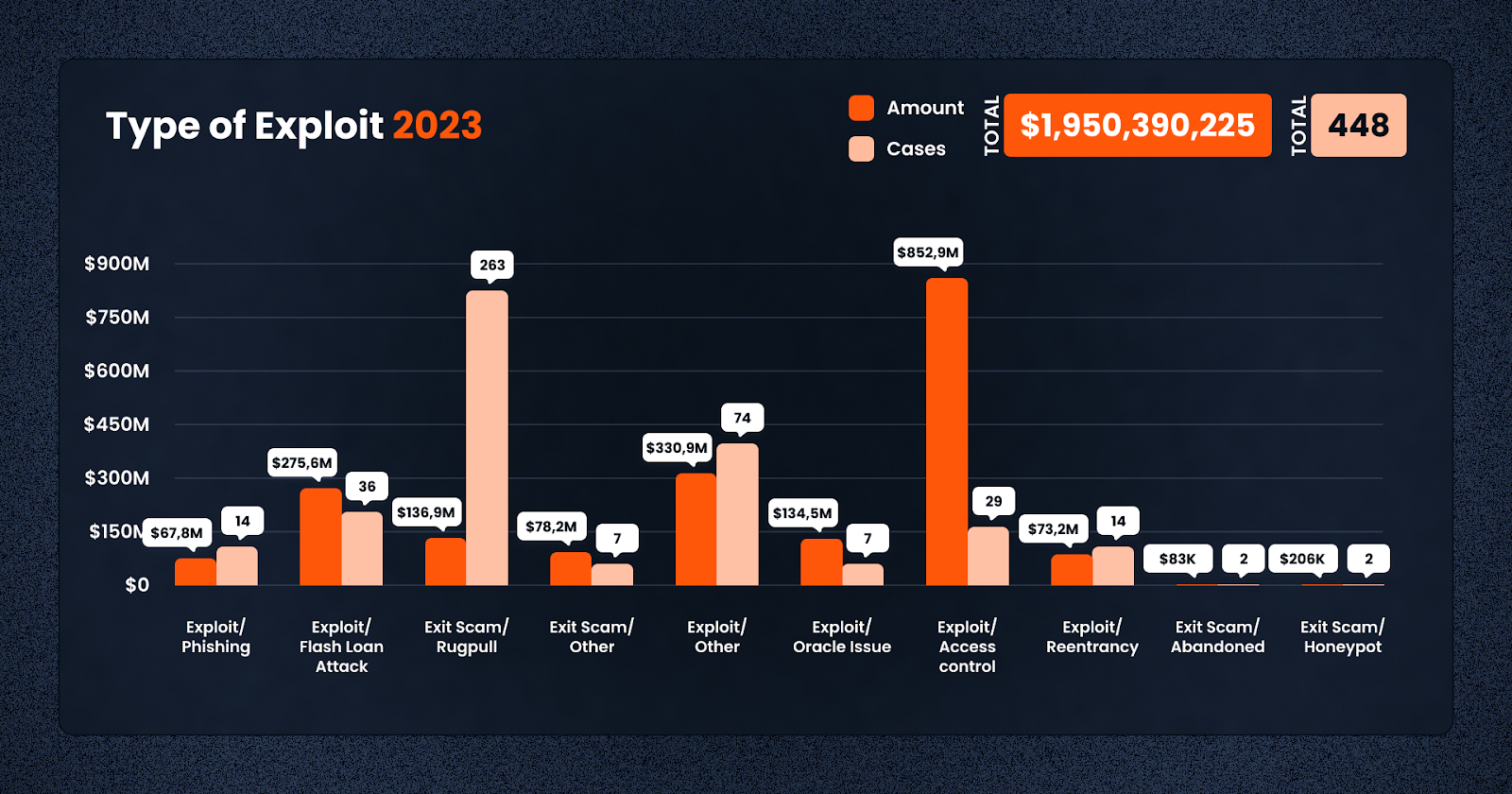
Exploits in 2023 came in many shapes and sizes, each presenting unique challenges and contributing to the overall losses in the industry. Understanding these common exploits is crucial in developing more robust security measures and enhancing the resilience of the ecosystem. Let’s have a look at each type of exploit, and how much was lost. As can be seen, a good deal of these involve smart contract vulnerabilities, which you can frontrun by checking each contract on the De.Fi Scanner, before you go about investing your hard-earned cash.
Exploit/Phishing (14 cases, $67,824,655 lost): Phishing attacks remained a persistent threat in 2023. These attacks typically involved deceiving users into revealing sensitive information such as private keys or login credentials. Despite being one of the oldest forms of cyberattacks, phishing continued to be effective in the Web3 era, causing substantial financial losses.
Exploit/Flash Loan Attack (36 cases, $275,594,997 lost): Flash loan attacks became increasingly prevalent in 2023. These attacks exploit the uncollateralized loan feature in DeFi, allowing attackers to borrow large amounts of cryptocurrency without upfront capital. The borrowed funds are then used to manipulate market prices or exploit vulnerabilities in DeFi protocols, resulting in substantial losses.
Exit Scam/Rugpull (263 cases, $136,991,987 lost): Rugpulls were a common occurrence, particularly in less-regulated or emerging projects. In these schemes, project developers abruptly withdraw all funds from a liquidity pool or project wallet, leaving investors with worthless tokens. This type of exploit highlights the risks associated with investing in new and unvetted projects.
Exit Scam/Other (7 cases, $78,232,623 lost): Other forms of exit scams also caused significant damage. These varied in their execution but generally involved the deliberate disappearance of project teams with investors’ funds, often after building trust over time.
Exploit/Other (74 cases, $330,922,107 lost): This category includes a variety of other exploits that may span multiple categories, and made up the most frequent type of issue. These could range from smart contract vulnerabilities to more sophisticated attacks exploiting unique features or flaws in specific protocols or platforms.
Exploit/Oracle Issue (7 cases, $134,479,921 lost): Oracle issues, which involve manipulating the data sources that smart contracts rely on to function, such as for external price data, were a notable problem. Attackers exploit these vulnerabilities to feed false information to smart contracts, leading to erroneous executions and financial losses.
Exploit/Access Control (29 cases, $852,896,976 lost): Access control exploits were by far the most damaging, with attackers exploiting weaknesses in how permissions and access rights are managed within smart contracts or platforms. These exploits often led to unauthorized access to funds or critical functionalities, resulting in significant losses.
Exploit/Reentrancy (14 cases, $73,158,394 lost): Reentrancy attacks, where an attacker can repeatedly call a function before the first instance of the call is finished, continued to be a problem. These attacks take advantage of the asynchronous nature of blockchain transactions to drain funds from a contract.
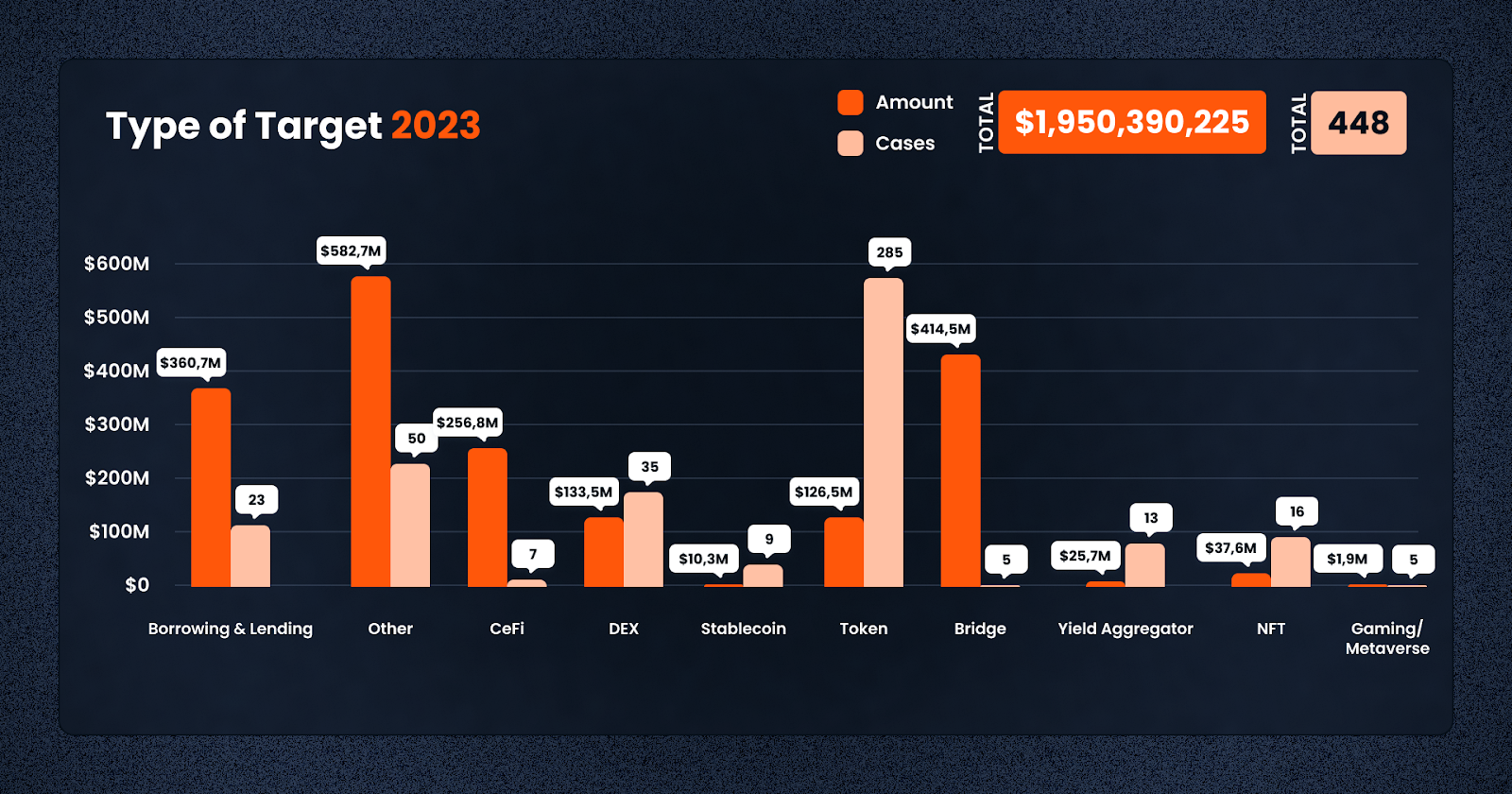
Alongside the common exploits, several key attack vectors were prominent in the DeFi and crypto space in 2023, targeting various aspects of the ecosystem.
CeFi (7 cases, $256,807,187 lost): Centralized Finance (CeFi) platforms were not immune to attacks. These platforms, which operate similarly to traditional financial institutions but within the crypto space, faced significant losses. The centralized nature of these platforms often makes them attractive targets for cyberattacks.
Exchange (DEX) (35 cases, $133,453,007 lost): Decentralized Exchanges (DEXes) also faced numerous security challenges. Despite their decentralized nature, liquidity is clearly concentrated in these protocols. Vulnerabilities in smart contracts or the platforms themselves led to substantial losses. These incidents highlight the ongoing need for improved security in DEX infrastructure.
Borrowing and Lending (23 cases, $360,729,353 lost): The borrowing and lending sector within DeFi was heavily targeted. Vulnerabilities in these platforms were exploited to siphon off funds, often involving complex attacks on the smart contracts governing these protocols.
Yield Aggregator (13 cases, $25,738,200 lost): Yield aggregators, which automate yield farming strategies, were subject to attacks exploiting the complexities and interdependencies of these protocols. These attacks often resulted in the loss of funds pooled for yield farming.
NFT (16 cases, $37,632,929 lost): The burgeoning NFT sector was not spared, with several incidents involving scams and exploits targeting NFT platforms and their users. These ranged from fraudulent projects to vulnerabilities in NFT marketplaces.
Gaming/Metaverse (5 cases, $1,973,552 lost): The gaming and metaverse sectors, increasingly integrated with blockchain and NFTs, experienced targeted attacks. These often involved exploiting the gaming economies or stealing valuable in-game assets.
Stablecoin (9 cases, $10,317,554 lost): Stablecoins, designed to offer stability in the volatile crypto market, faced attacks that often aimed at destabilizing their pegged value or exploiting their backing assets.
Bridge (5 cases, $414,469,505 lost): Blockchain bridges, which allow the transfer of assets between different blockchains, were significant targets due to the large amounts of funds they handle. Exploits here often involved sophisticated attacks on the smart contracts governing these bridges.
The variety and complexity of exploits and attack vectors in 2023 underscore the continuous evolution of threats in the DeFi and crypto space. The industry must persist in enhancing security measures, conducting rigorous audits, and fostering user education to mitigate these risks and protect investments.
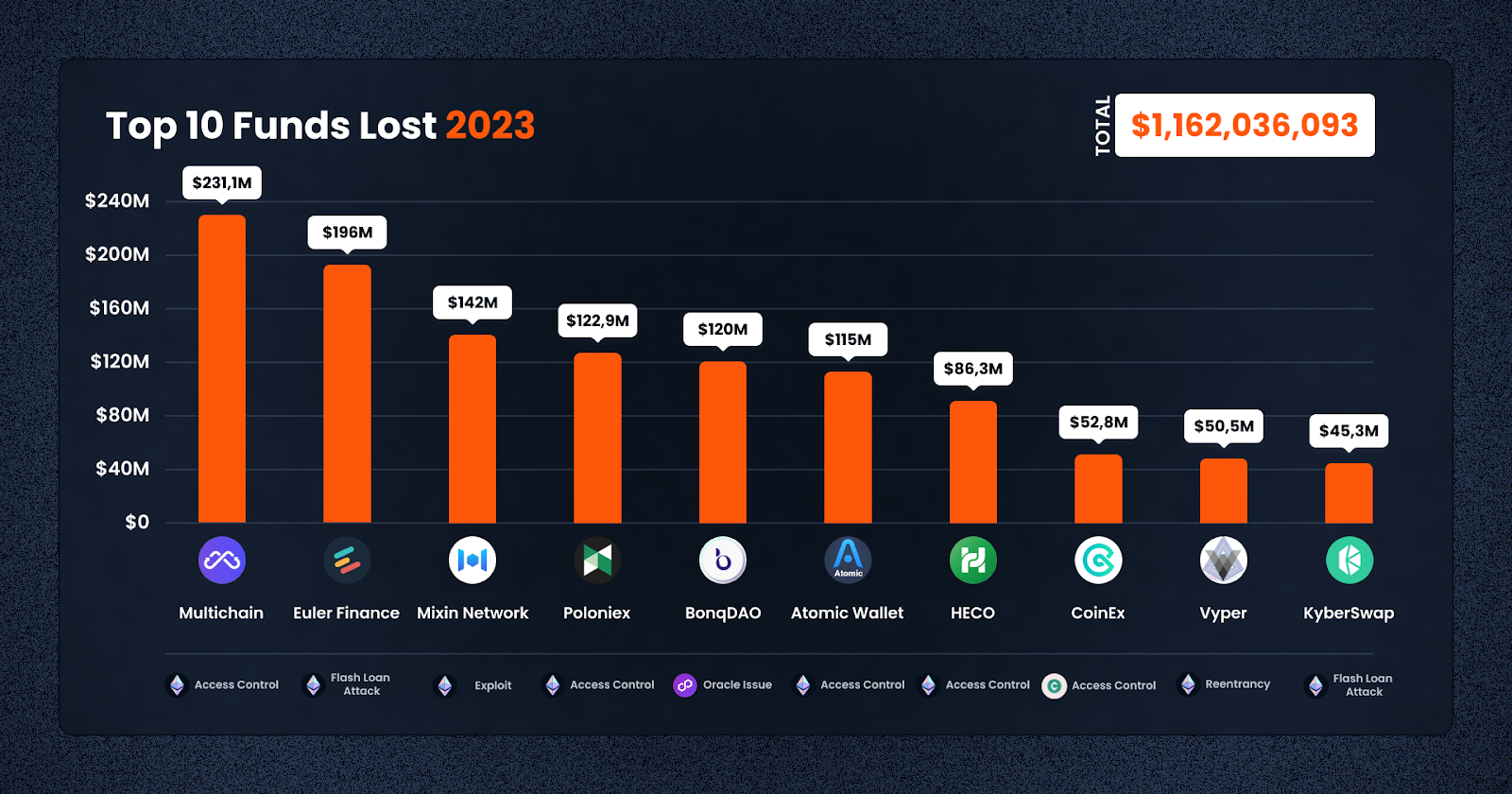
With the above overview in mind, let’s have a look at some of the largest losses in 2023!
1. Multichain ($231,129,033; Ethereum, Access Control Exploit):
2. Euler Finance ($196,000,000; Ethereum, Flash Loan Attack):
3. Mixin Network ($142,041,764; Ethereum, Exploit):
4. Poloniex ($122,981,391; Ethereum, Access Control Exploit):
5. BonqDAO ($120,000,000; Polygon, Oracle Issue):
6. Atomic Wallet ($115,000,000; Ethereum, Access Control Exploit):
7. HECO ($86,284,430, Ethereum; Access Control Exploit):
8. CoinEx ($52,847,077; Other, Access Control Exploit):
9. Vyper ($50,476,970; Ethereum, Reentrancy Exploit):
10. KyberSwap ($45,275,428; Ethereum, Flash Loan Attack):
All in all, the DeFi and crypto space in 2023 experienced significant losses due to bad actors – the top 10 cases alone accounted for losses exceeding $1 billion. These incidents, ranging from access control exploits to flash loan attacks, highlight the critical need for enhanced security measures and vigilance in the DeFi space.
To mitigate such risks, investors and users can take proactive steps to safeguard their assets. Tools like the De.Fi Scanner offer a valuable resource for checking the security of smart contracts before making investments. This tool helps in identifying potential vulnerabilities and risks, allowing users to make informed decisions. Additionally, the De.Fi Shield serves as a crucial tool for managing and revoking contract approvals, providing an extra layer of security against unauthorized access and potential exploits.
These tools, along with a cautious and informed approach to DeFi investments, are essential for protecting assets in this dynamic and ever-changing landscape.
About De.Fi
De.Fi is a pioneering Web3 Super App, featuring all-in-one Asset Management Dashboard, Social Profiles, Opportunity Explorer, and the world’s first Crypto Antivirus. With a trusted user base of 1.5M globally, De.Fi is committed to driving DeFi adoption by simplifying and securing the self-custody transition. The platform is endorsed by prominent partners, including OKX and Huobi, supported by former Coinbase M&A expertise, and trusted by leading institutions such as University College London and Coingecko.
October 2025 saw a total of $38.63 million lost across nine distinct security incidents in both centralized and decentralized platforms.
The third quarter of 2025 marked yet another turbulent period for the DeFi and wider crypto ecosystem, with $434,124,000 lost to exploits, scams, and security failures across both centralized and decentralized platforms.
June 2025 witnessed another alarming month for Web3 security, with a total of $114,768,000 lost during 11 separate attacks
May 2025 saw both DeFi and CeFi security once again under attack, with $275,953,000 lost across just 8 recorded incidents
April 2025 witnessed a large escalation in exploit volume and value, with a massive $5,919,684,000 being stolen in 10 confirmed events.
Q1 2025 marked one of the worst quarters in blockchain exploit history, with total recorded losses topping $2,052,584,700 across 37 incidents
© De.Fi. All rights reserved.