DeFi Rekt Report October 2025: $38.6 Million Lost Across 9 Exploits
October 2025 saw a total of $38.63 million lost across nine distinct security incidents in both centralized and decentralized platforms.
DeFi is growing quickly, and so do the threats and vulnerabilities facing the ecosystem. February 2024 is coming to a close, and has already provided us with critical insights into the prevailing trends in DeFi security, highlighting areas of concern and the persistent efforts of recovery. By analyzing the data from the De.Fi REKT database, we have put together some valuable insights to help investors strategize for better protection of assets within the DeFi space.
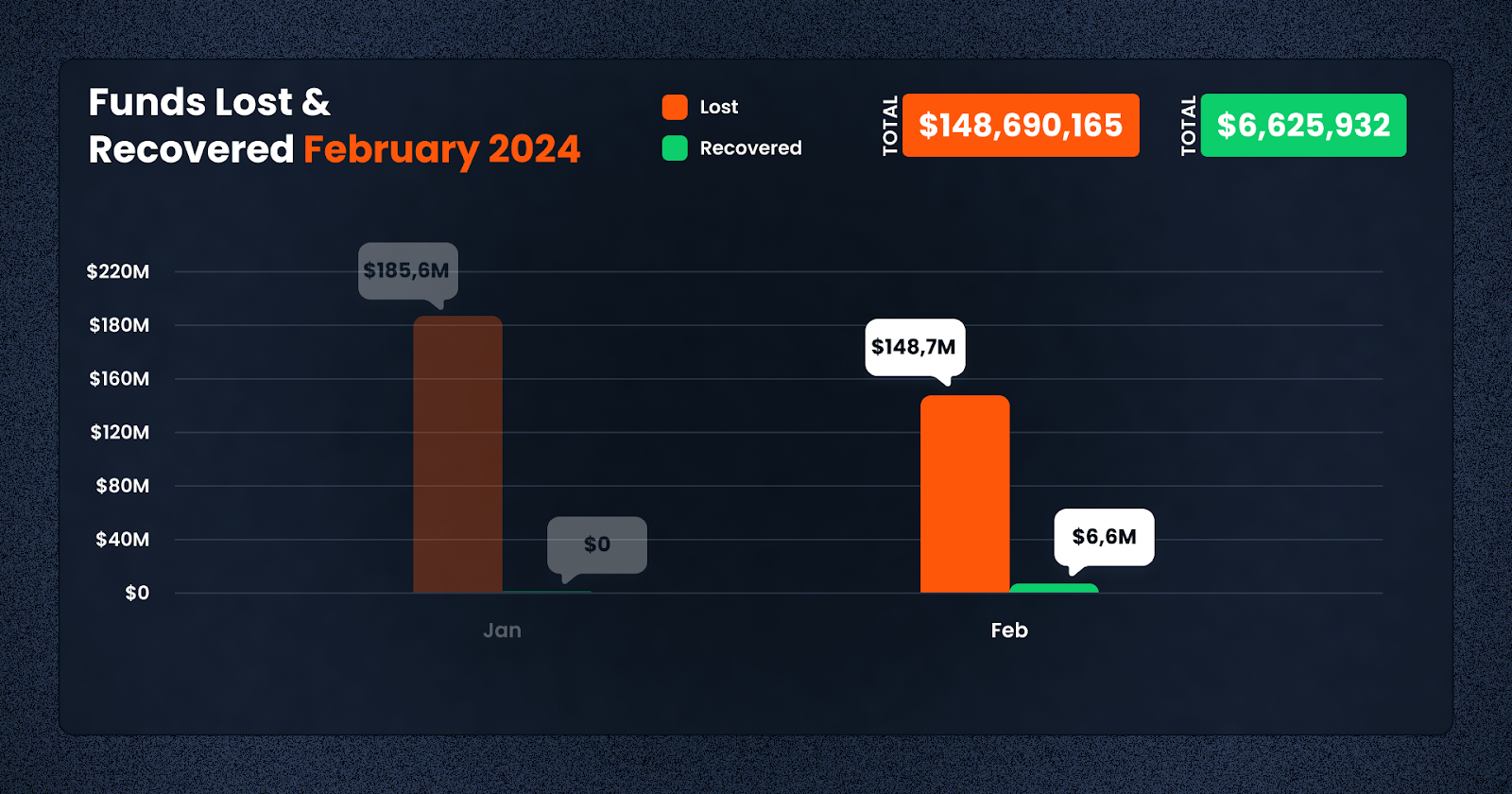
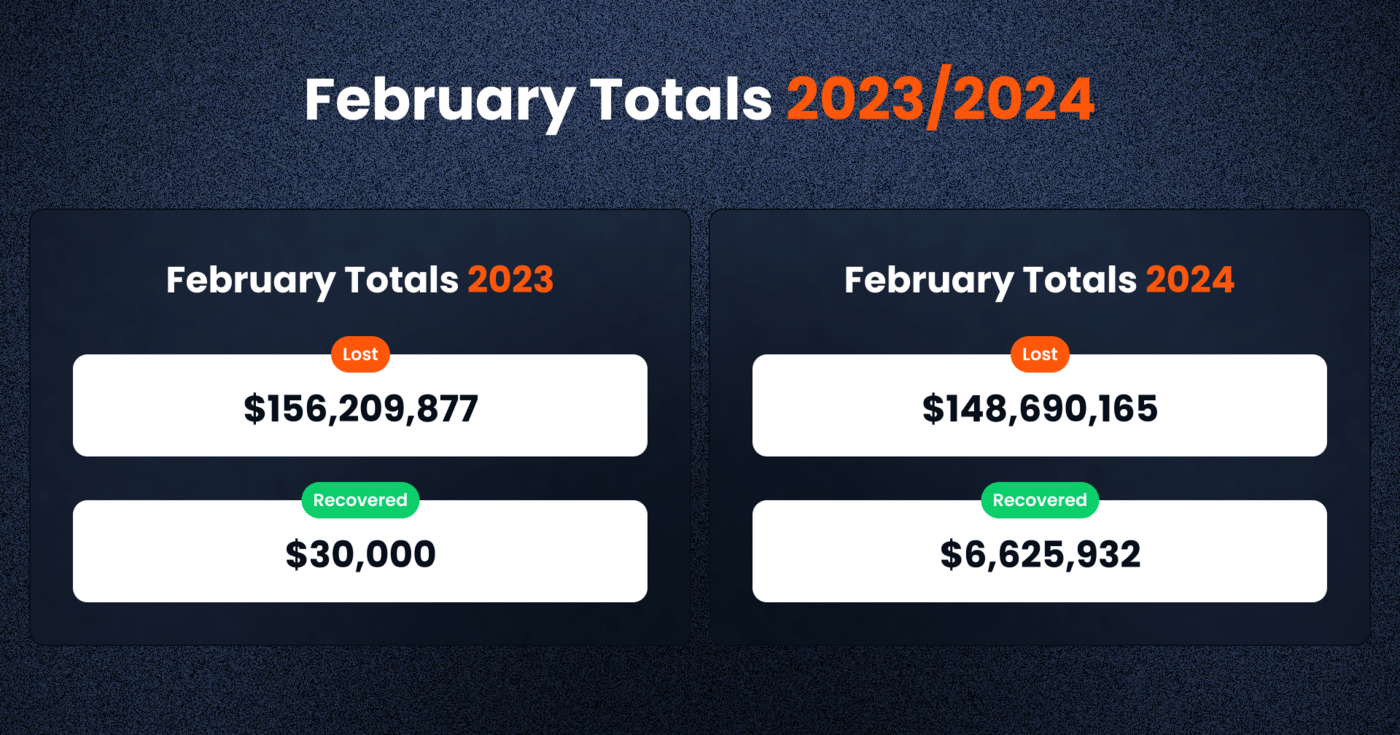
In February 2024, the DeFi sector witnessed a significant amount of activity with regards to security incidents. A total of $148,690,165 was lost across various platforms and chains due to diverse exploits. However, efforts to mitigate these losses led to the recovery of $6,625,932, demonstrating the ongoing battle between security mechanisms and malicious actors.
The month saw several high-profile cases, with Bitforex, PlayDapp, and Fixed Float being among the most impacted. Bitforex experienced the largest loss at $56,000,000 on the Ethereum chain, primarily affecting the centralized exchange category, showcasing vulnerabilities within exchange platforms. PlayDapp followed with a $32,350,000 loss on Ethereum. Fixed Float’s $26,130,157 loss on Ethereum highlighted the diverse nature of targets within the DeFi ecosystem.
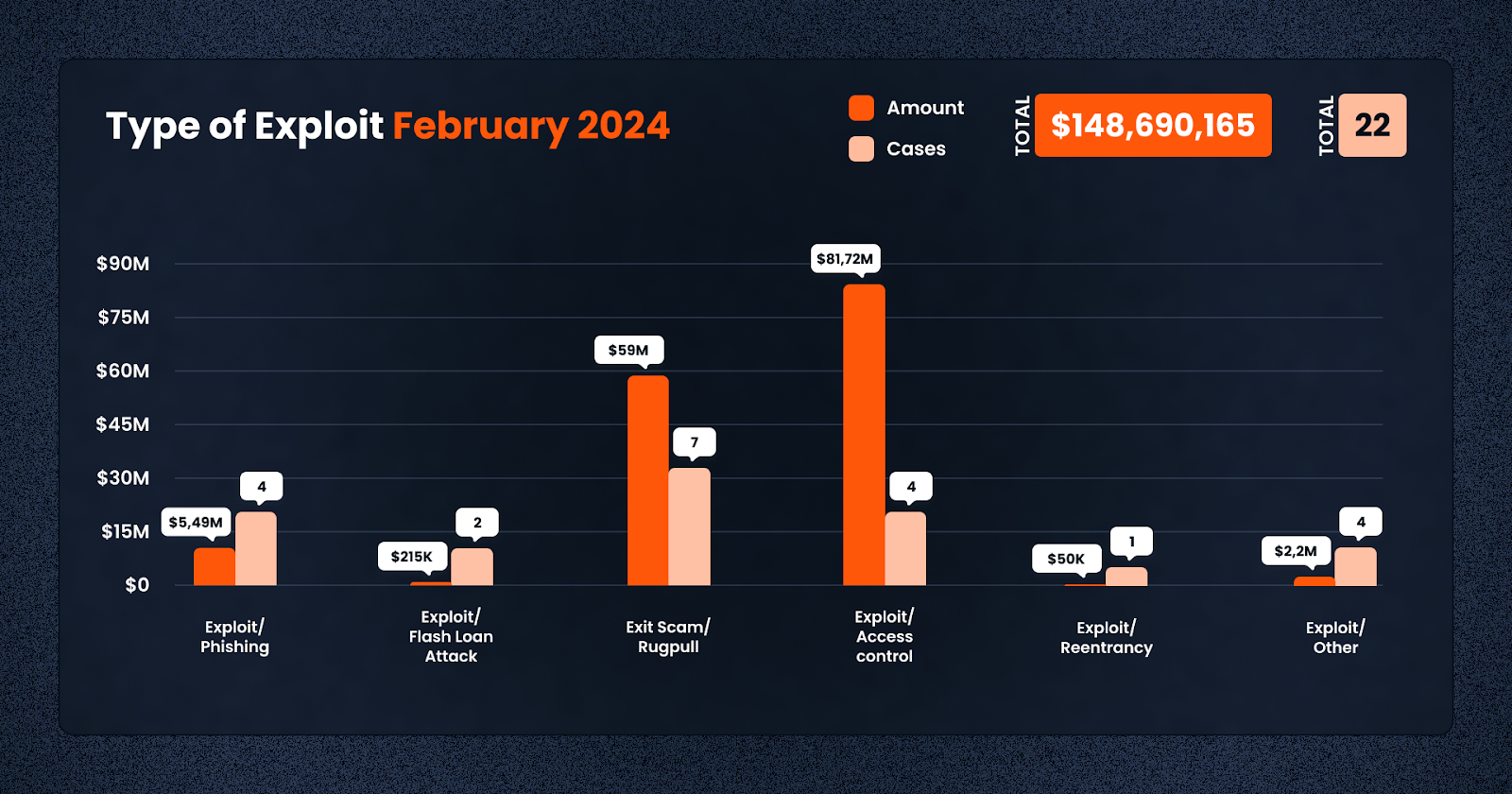
Access control issues dominated February, accounting for $81,723,472 across four cases. This suggests that permission settings and access management remain critical vulnerabilities within DeFi platforms. These incidents underscore the critical need for stringent permission settings and access management on DeFi platforms. Proper access control mechanisms are essential to ensure that only authorized users can perform sensitive operations, thereby preventing unauthorized access or manipulation of funds. The cases impacted by access control issues emphasize the importance of comprehensive security audits to identify and rectify potential vulnerabilities in the system’s access control protocols.
Exploits, which generally involve taking advantage of vulnerabilities in smart contracts or platform architectures, were also notable during the month. Four cases of exploits led to $2,202,006 in losses. These incidents highlight the necessity for thorough smart contract auditing and testing before deployment. By identifying and addressing vulnerabilities early, platforms can significantly reduce the risk of exploits and protect user assets.
Phishing attacks, aimed at deceiving users into disclosing sensitive information such as private keys or login credentials, resulted in four cases totaling $5,499,384 in losses, rounding out the Top 3. These attacks often exploit social engineering techniques and highlight the need for ongoing user education and awareness programs. Users should be informed about the common tactics used by attackers and encouraged to verify the authenticity of communications and websites before providing any personal or financial information.
The СEX category emerged as an unexpected target, with significant losses recorded. This trend emerges not so often as other exploited categories. Over $56m was lost in this category, with a Bitforest CEX as the only one and the biggest projects being exploited since a long time.
The gaming/metaverse category emerged as a notable target, with significant losses recorded. This trend underscores the growing interest in NFTs and gaming platforms within DeFi, attracting both users and malicious actors. Over $32.6m was lost in this category, with a bulk of it coming from the PlayDapp exploit.
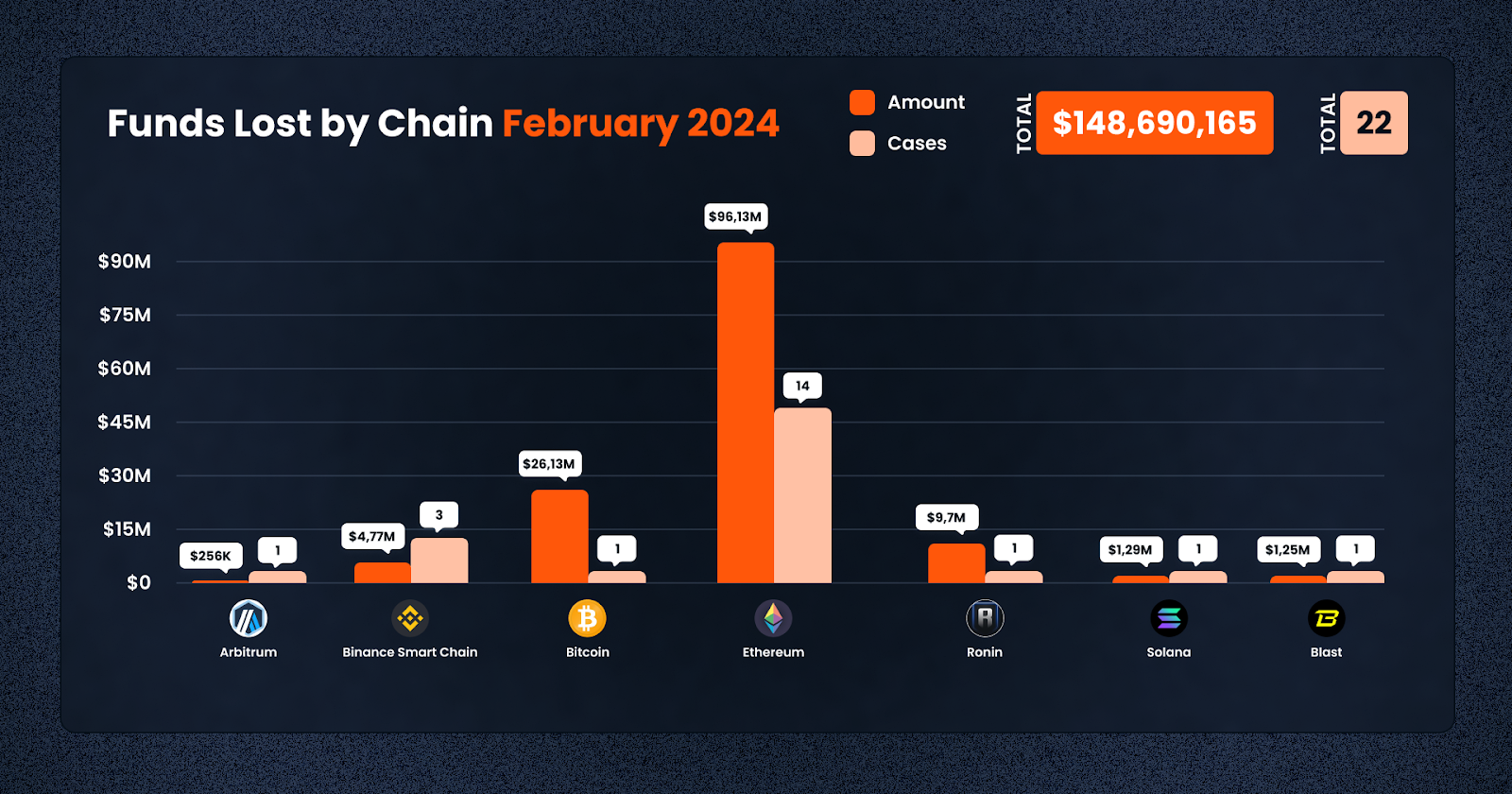
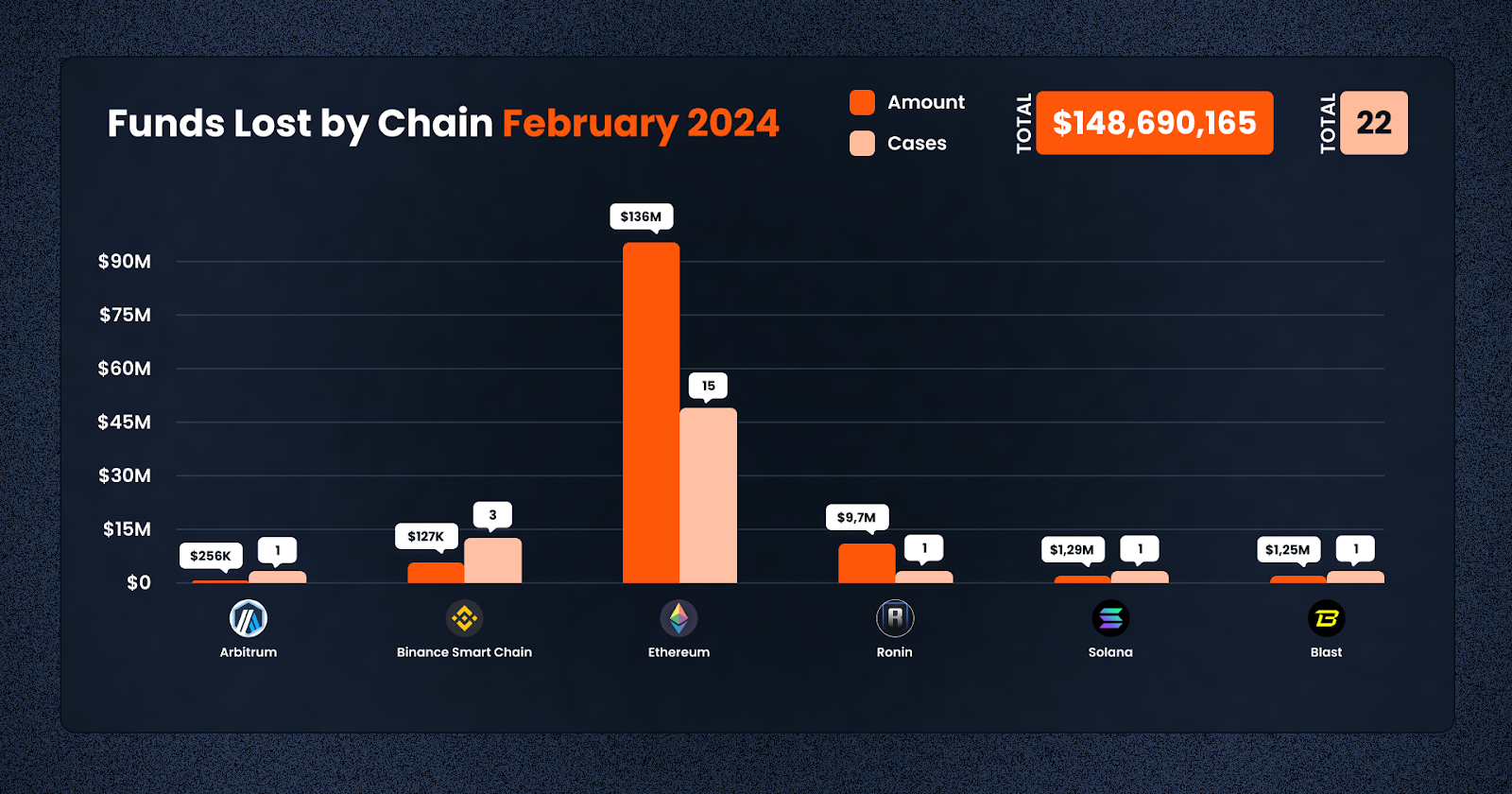
In total, February 2024 witnessed 22 distinct cases leading to an aggregate loss of $148,690,165 across these blockchain networks. This data underscores the critical need for enhanced security measures and vigilance across all chains to protect assets against the evolving strategies of malicious actors. Here are the losses by chain:
1. Ethereum: Dominating the scene, Ethereum witnessed the highest losses amounting to $136,049,923 spread over 15 incidents. This figure highlights Ethereum’s central role in the DeFi ecosystem and its appeal to attackers due to its extensive user base and wealth of DeFi applications.
2. Ronin: With a loss of $9,700,000 from just one case, Ronin’s security breach highlights the vulnerabilities even in side chains and specialized networks designed for gaming and NFTs.
3. Solana: Solana saw a loss of $1,297,344 in a single event, reflecting the growing interest and subsequent risks in its rapidly expanding DeFi and dApp ecosystem.
4. Blast: A newer entrant in the DeFi space, Arbitrum faced a loss of $1,259,000 in one incident, indicating that even layer 2 solutions and scaling networks are not immune to the pervasive threat of exploits.
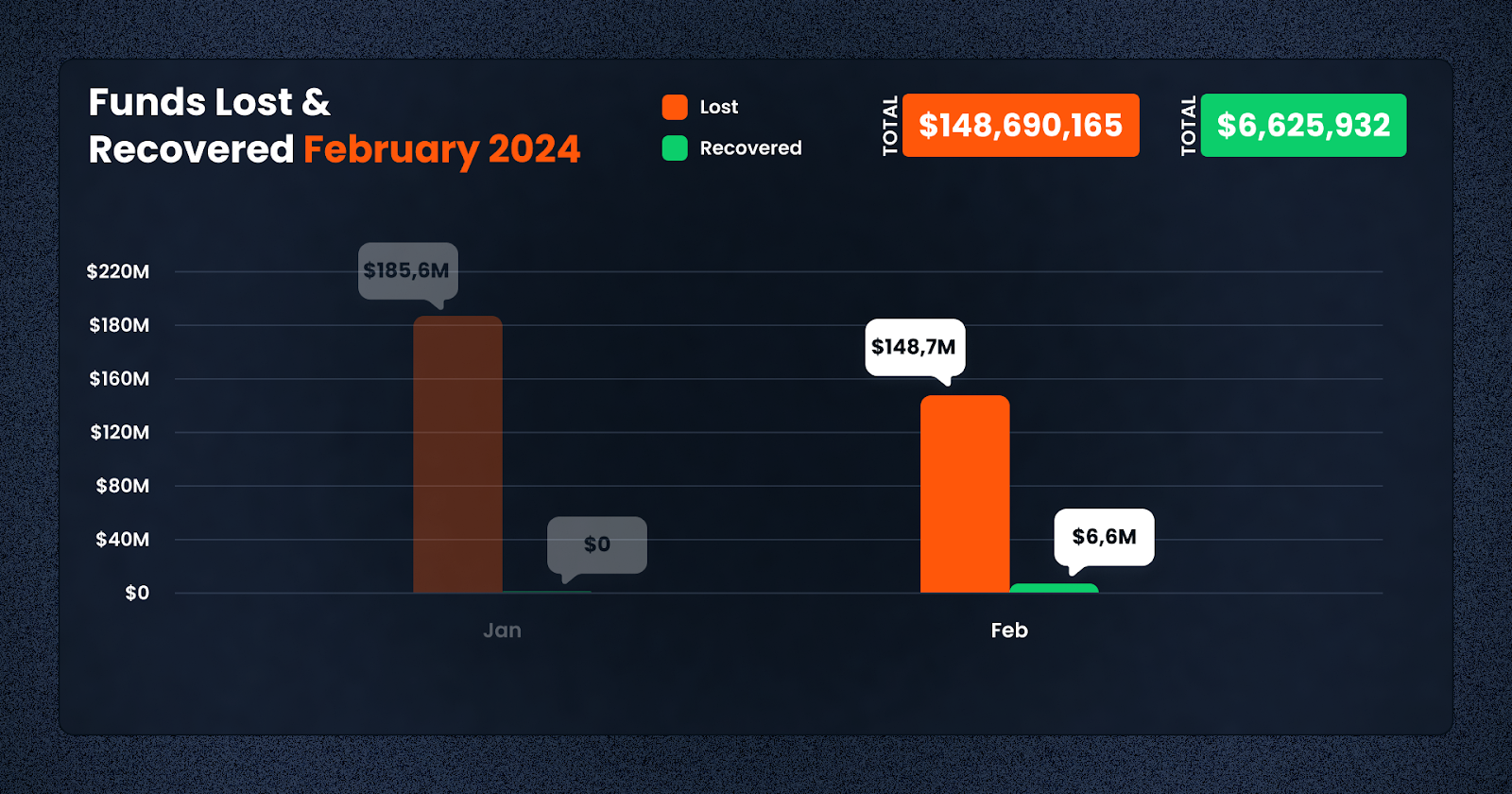
The recovery of over $6,6 million, while only a fraction of the total lost, indicates successful efforts in asset recovery and the importance of rapid response mechanisms. Platforms and communities must continue to develop and support tools and strategies for mitigating losses post-exploit.
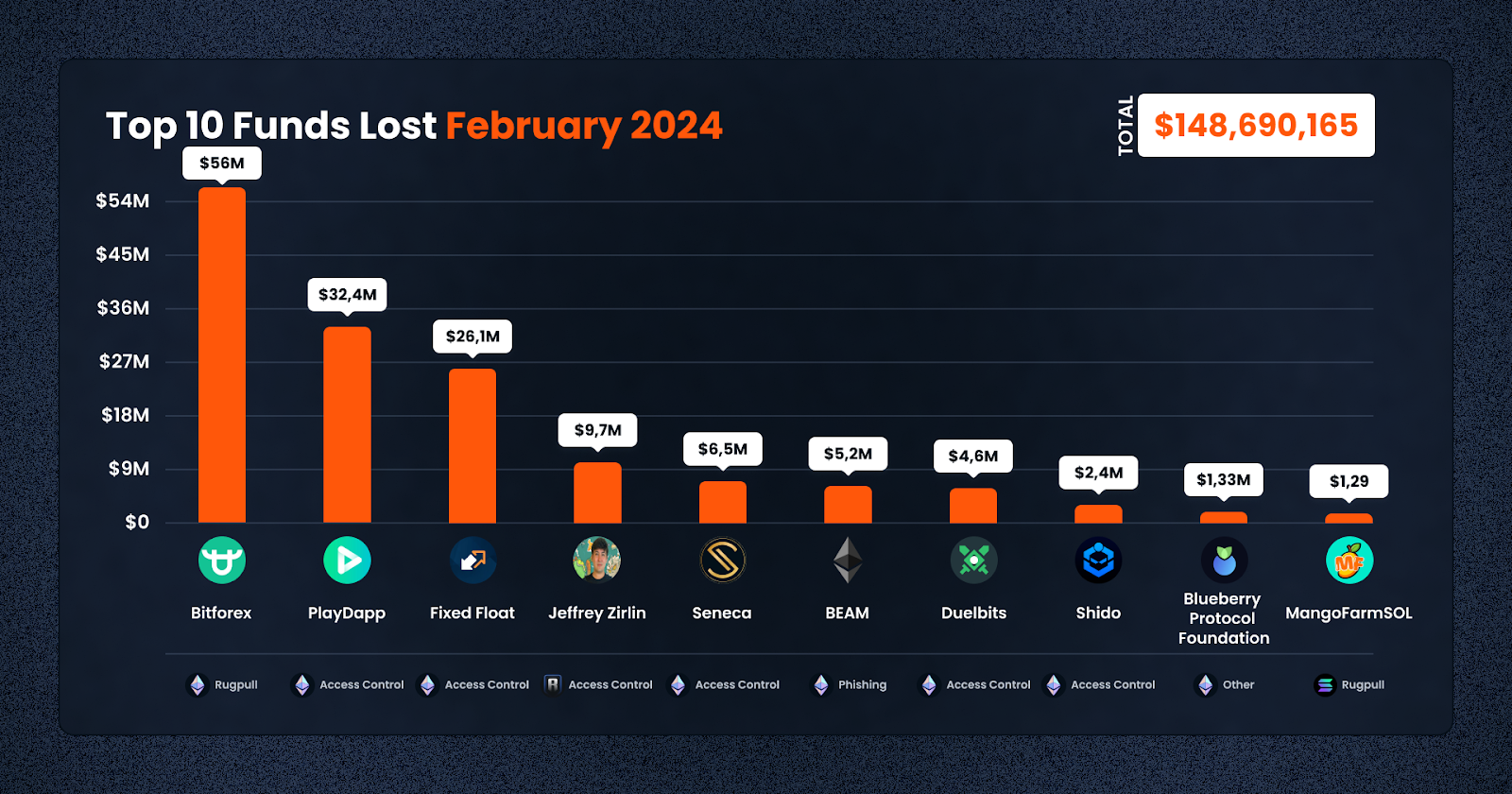
With the trends covered, let’s have a look at the top 10 exploit cases for February 2024.
1. Bitforex – $56,000,000
BitForex, a cryptocurrency exchange, shut down access to its platform after a suspicious outflow of approximately 56,500,000 USD across several blockchains. Users attempting to log in are blocked by CloudFlare’s DDoS protection service. The exchange stopped processing withdrawals and has not been responding to customer support inquiries. The outflows appear to be an exit scam rather than an external attack. The funds were received from multiple addresses in BitForex’s hot wallets, most of the funds were on the Ethereum chain, in the TRB tokens, and remain in wallets as of Feb 29,2024.
Funds Holder:
– Ethereum: https://etherscan.io/address/0xdCaCd7EB6692b816b6957f8898c1C4B63D1fC01F
– Bitcoin: https://blockstream.info/address/3DbbF7yxCR7ni94ANrRkfV12rJoxrmo1o2
– TRON: https://tronscan.org/#/address/TQcnqaU4NDTR86eA4FZneeKfJMiQi7i76o
2. PlayDapp – $32,350,000
PlayDapp, a P2E game running on the Ethereum chain, was exploited two times,between Feb 9-12, 2024. The root cause of the exploit was reportedly due to the compromise of private keys. Before the first exploit transactions, a new minter was added to the PlayDapp: PLA Token. The attacker minted a total of 1.79 billion PLA tokens in two separate incidents, worth around 287,775,772 USD at the time. However, the attacker was able to convert only 32 million USD. The stolen funds were transferred to various addresses, with some being deposited on the Polygon chain, Binance exchange, and a significant portion remaining in the scammer’s address as of Feb 13, 2024. The attacker was funded by FixedFloat. A reward of 1 million USD was offered to the hacker for the immediate return of all stolen contracts and assets.
Attacker’s Initial Address:
https://etherscan.io/address/0xD151050d43c28690766f50Ce9ea8686c5D243a40
3. Fixed Float – $26,130,157
FixedFloat, a cryptocurrency exchange platform, was exploited on February 16, 2024. The attacker stole approximately $26.1 million worth of Bitcoin and Ethereum. Most of the money stolen was on the Bitcoin chain, funds were distributed between multiple addresses. The stolen funds on the Ethereum Mainnet were transferred to the eXch exchange through multiple addresses, with a small portion deposited into HitBTC. Additional clarifications regarding the incident were not disclosed by FixedFloat.
Attacker Addresses:
https://www.blockchain.com/btc/address/bc1q2skp47p9f5mr4n4m27k66v0l68gh3xdd7ad4e5
https://etherscan.io/address/0x85c4fF99bF0eCb24e02921b0D4b5d336523Fa085
4. Jeffrey Zirlin – $9,700,000
On February 23, 2024, Jihoz_Axie tweeted on his X (formerly twitter) about compromise of his two personal wallet addresses,. The attacker stole assets from these wallets, swapped them to Ronin WETH, and bridged them to the Ethereum mainnet using Axie Infinity:Ronin Bridge. The stolen funds were then transferred to other EOA addresses and eventually deposited into TornadoCash through several addresses.
Attacker Address:
https://ronin.bloks.io/address/0x39f817976c51a91b60145febad81067e69713105
5. Seneca – $6,500,000
On February 28, 2024, Seneca Protocol experienced exploitation on both the Ethereum Mainnet and Arbitrum Chain due to a smart contract vulnerability. The vulnerability, rooted in an arbitrary external call vulnerability within the protocol’s contracts, enabled attackers to drain assets. Specifically, the vulnerable contracts contained a _call function that lacked sufficient restrictions on the types of calls allowed and failed to adequately validate callee addresses. Exploiting this, attackers manipulated the performOperations function to craft calldata triggering arbitrary calls, facilitating unauthorized token transfers to their addresses.
Exploiter Addresses:
https://etherscan.io/address/0x98c6ced9b18d57ee58820e61aa126c0fec30435d
https://etherscan.io/address/0xfeb5BCbB85E77F42b9B89d8772d4f6C7C5183Aa4
6. BEAM – $5,170,000
A victim, identified by the address 0x83664b8a83b9845ac7b177df86d0f5bf3b7739ad, fell prey to a phishing scam resulting in the loss of $5.17 million worth of BEAM tokens. The scam involved the victim signing an ‘increaseAllowance’ transaction, with the token spender being a GnosisSafe wallet address 0xbaEE148DF4bf81aBf9854c9087F0D3a0fFd93DBB.
Scammers’ Addresses:
https://etherscan.io/address/0x98c6ced9b18d57ee58820e61aa126c0fec30435d
https://etherscan.io/address/0xfeb5BCbB85E77F42b9B89d8772d4f6C7C5183Aa4
https://etherscan.io/address/0x09e0cA7E92E2B893f07cdAE75C011C3606ecD61a
7. Duelbits – $4,643,315
Duelbits, a crypto casino and sports betting platform, experienced an exploit on February 13, 2024. The attacker gained access to a Duelbits wallet. The root cause of this exploit appears to be a loss of wallet access control. The attacker stole various assets, including ETH, BNB, BUSD, USDT, SHIBA INU, and ApeCoin, totaling a loss of 4,643,315 USD. The stolen funds were bridged, exchanged to ETH, and transferred to another EOA address.
Attacker Address:
https://bscscan.com/address/0x3933924FAf011aE8d24e44beE450b3d78E46a666
8. Shido – $2,400,000
ShidoGlobal recently encountered a transfer of ownership, resulting in a significant loss amounting to approximately $4 million. The exploit occurred when the new owner swiftly upgraded the StakingV4Proxy contract by introducing a concealed withdrawToken() function. This function enabled the attacker to execute withdrawals of the entire balance of 4,353,473,223.864904 $SHIDO tokens from the contract. Subsequently, the attacker swapped a portion of the acquired $SHIDO tokens for $ETH and transferred 692.8 $ETH, equivalent to $2.4 million, to address 0x4621e0cd8c91ecf1b0efcbf07f0838a5ee25c5dd. The remaining $SHIDO tokens, valued at $1.6 million, are still retained in the attacker’s address 0x1982358c84da9d0b4b96fc9e8564d132f7d0041f.
Attacker’s ETH Address:
https://etherscan.io/address/0x4621e0cd8c91ecf1b0efcbf07f0838a5ee25c5dd
9. Blueberry Protocol – $1,337,128
Blueberry, a decentralized financial lending and leverage protocol, suffered an exploit on February 23, 2024.An attacker attempted to exploit the vulnerability, but was overtaken by c0ffeebabe.eth, a well-known MEV bot and whitehat operator that had previously beaten other exploits and returned funds to projects. Initially 457.7 ETH was withdrawn from the project, but 366.6 ETH was of that was able to be returned.The remaining 91 ETH, worth about $1,350,000, was lost due to validator payments.
c0feebabe.eth’s Contract Address:
https://etherscan.io/address/0x3AA228a80F50763045BDfc45012dA124Bd0a6809
10. MangoFarmSOL – $1,297,334
MangoFarmSOL, a yield farming protocol on the Solana blockchain, encouraged users to deposit Solana tokens into the protocol to earn airdrops. On January 6, 2024, the project conducted an exit scam, withdrawing a total of 13,514 SOL tokens (worth around 1.29 million USD) deposited by users. The stolen funds primarily consisted of SOL tokens, which were then laundered through various channels, first bridging to the Ethereum network via wormhole and allbridge and then deposited into platforms such as Railgun and eXch. The acquired USDC was bridged from the Solana network to Ethereum via the wormhole bridge. The project subsequently deleted their website and Twitter account.
Scammer Address: https://explorer.solana.com/address/FLq2GE2x4kv5UbK6Qw2h9FtBPcLeZnNhwSeGvDDokYbH
Conclusion
The DeFi exploits and losses in February 2024 has highlighted several trends of concern, from access control vulnerabilities to the targeting of emerging sectors like gaming/metaverse. To navigate these challenges, platforms must prioritize comprehensive security audits, embrace robust access management practices, and foster community education to empower users against phishing and other social engineering attacks. As DeFi continues to mature, the collaboration between platforms like De.Fi, security researchers, and users will be paramount in safeguarding the ecosystem and fostering its sustainable growth.
About De.Fi
De.Fi is an all-in-one Web3 Super App featuring an Asset Management Dashboard, Opportunity Explorer, and home of the world’s first Crypto Antivirus powered by the largest compilation of hacks and exploits, the Rekt Database. Trusted by 850K users globally, De.Fi aims to drive DeFi adoption by making the self-custody transition as simple and secure as possible. Backed by Okx, Huobi, former Coinbase M&A, and used by large companies worldwide, including University College London and Coingecko.
Website | Twitter | De.Fi Security | Rekt Database
October 2025 saw a total of $38.63 million lost across nine distinct security incidents in both centralized and decentralized platforms.
The third quarter of 2025 marked yet another turbulent period for the DeFi and wider crypto ecosystem, with $434,124,000 lost to exploits, scams, and security failures across both centralized and decentralized platforms.
June 2025 witnessed another alarming month for Web3 security, with a total of $114,768,000 lost during 11 separate attacks
May 2025 saw both DeFi and CeFi security once again under attack, with $275,953,000 lost across just 8 recorded incidents
April 2025 witnessed a large escalation in exploit volume and value, with a massive $5,919,684,000 being stolen in 10 confirmed events.
Q1 2025 marked one of the worst quarters in blockchain exploit history, with total recorded losses topping $2,052,584,700 across 37 incidents
© De.Fi. All rights reserved.