What is Permit2? - Contract Guide + How to Revoke
A smart contract originally conceived by Uniswap, Permit2 manages the approval of token transfers via gasless signatures.

As we move into the second month of 2023, hackers and scammers are back in full swing. Despite the mild uptick in the markets, we saw losses mount to a 9-figure amount in February.

A total of $142.4m was lost in February 2023 alone, marking a year-on-year increase since 2022: by over 200%! Here’s a breakdown chart by month for 2022 for comparison:
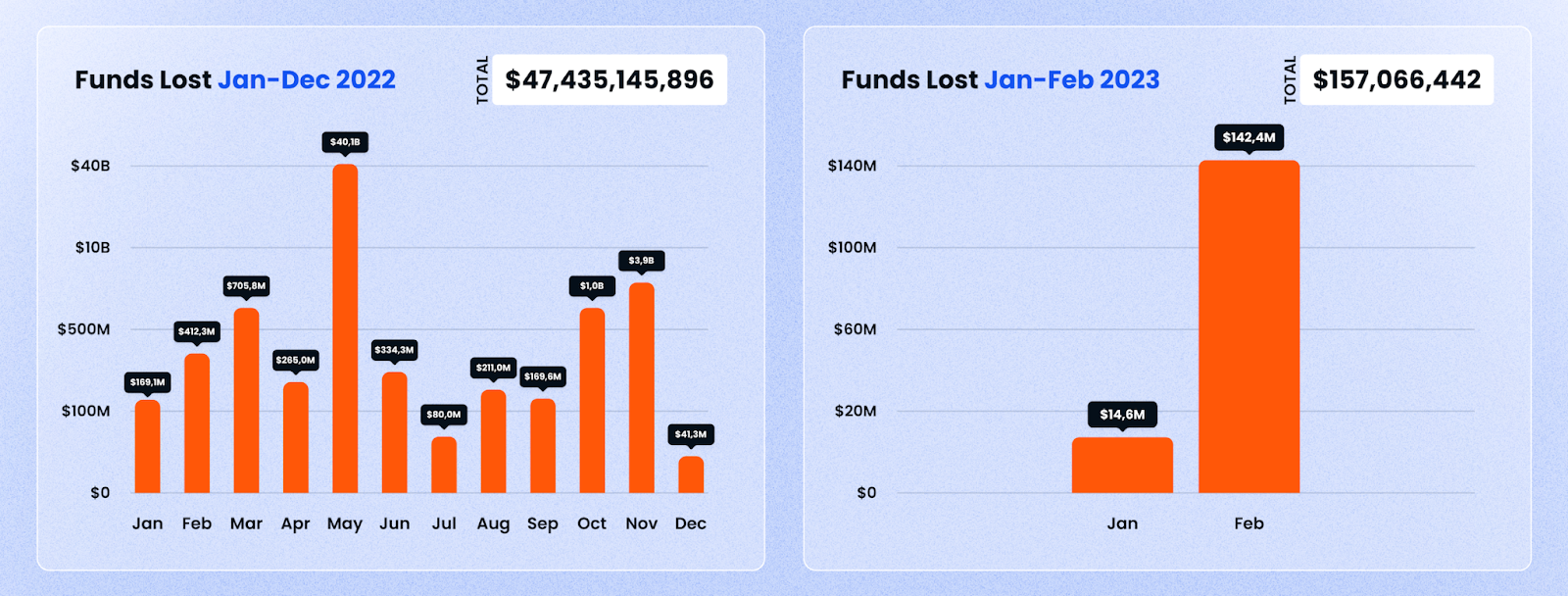
Another unfortunate occurrence this month was that in February, none of the losses were recovered.
On that note, let’s take a brief look at the top 5 cases this month.
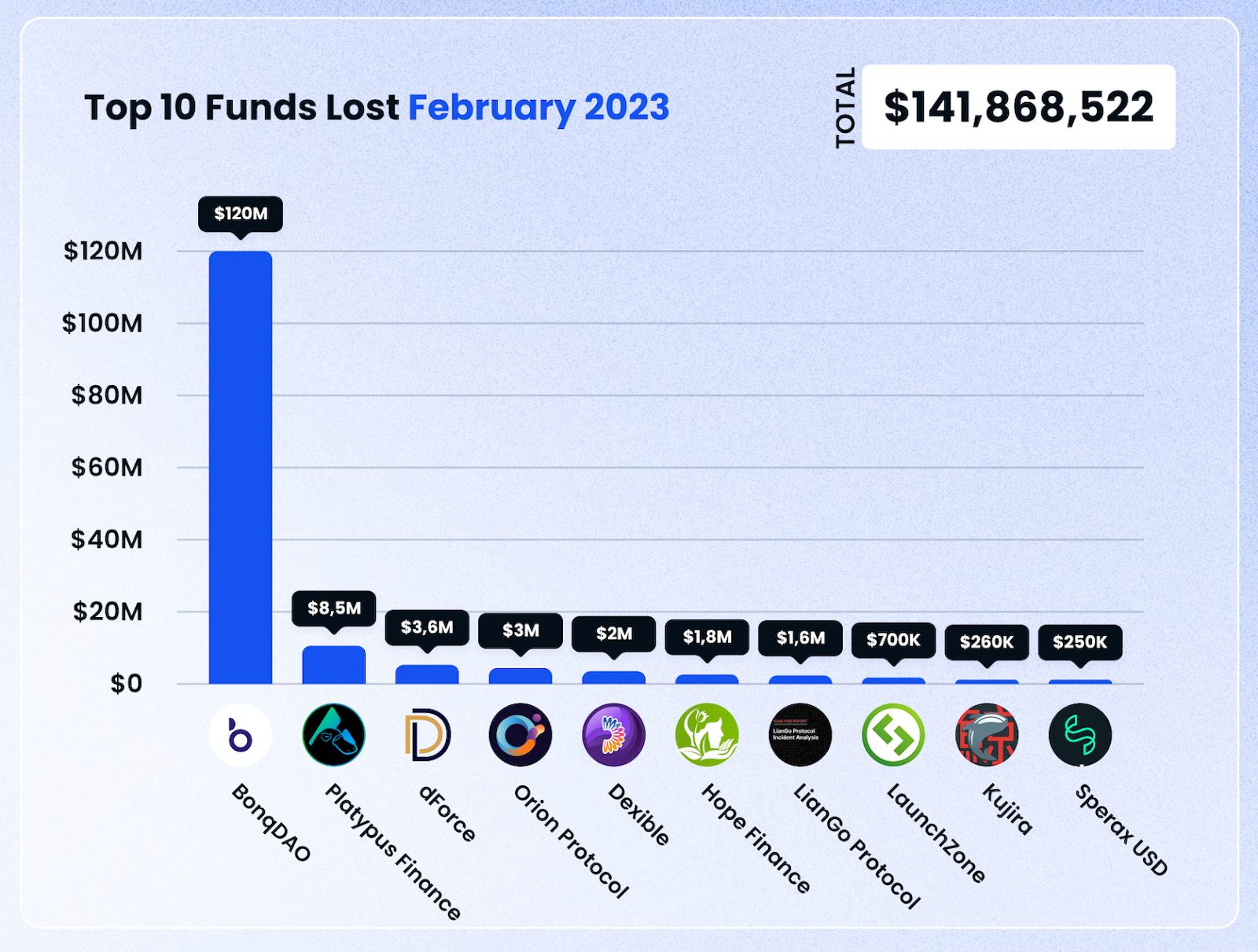
1. BonqDAO — $120m Lost (Oracle Issue, February 2)
On 2 February, BonqDAO and AllianceBlock, two blockchain-based platforms, have suffered a major loss of $120 million due to a vulnerability in the BonqDAO smart contract. The exploit has forced the suspension of trading and liquidity to prevent the stolen tokens from being converted into other assets. The Bonq protocol has also since been suspended, and the team is currently working on a solution to enable users to withdraw the remaining collateral.
The BonqDAO exploit occurred when its price oracle was manipulated, resulting in an increase in the WALBT price. This allowed the attacker to mint over 100 million BEUR. The attacker then manipulated the WALBT price and liquidated multiple troves, enabling them to withdraw 113.8 million WALBT and 98 million BEUR, with a combined value of over $10 million.
The dumping of these illicit gains resulted in a significant drop in the value of both WALBT and BEUR. The WALBT price dropped by more than 50%, and the BEUR price dropped by 34%. As a result, the total loss for BonqDAO and AllianceBlock was estimated to be $120 million.
Block Data Reference
Examples of exploit TXs:
https://polygonscan.com/tx/0x31957ecc43774d19f54d9968e95c69c882468b46860f921668f2c55fadd51b19
https://polygonscan.com/tx/0xa02d0c3d16d6ee0e0b6a42c3cc91997c2b40c87d777136dedebe8ee0f47f32b1
Exploiter address:
https://polygonscan.com/address/0xcacf2d28b2a5309e099f0c6e8c60ec3ddf656642
https://etherscan.io/address/0xcAcf2D28B2A5309e099f0C6e8C60Ec3dDf656642
2. Platypus Finance — $8.5m Lost (Flash Loan, February 16)
Platypus Finance, an automated market maker (AMM) providing stableswap opportunities, was recently targeted by a flash loan attack. The attacker exploited multiple asset contracts of the protocol, using a malicious smart contract with unverified source code, and stole $8,500,887 worth of assets in stablecoins. This included nearly 4,400,000 $USDC, 2,700,000 $USDT, 687,000 $BUSD, and 691,000 $DAI.
The attacker used a weakness in the USP solvency check mechanism to take out a flash loan of 44,000,000 $USDC, which was then used to swap for 44,000,000 Platypus LP-USD. The attacker then minted 41,700,000 $USP tokens for free and swapped them for various stablecoins. As of the time of writing, the Platypus Finance team is working with third-party services like Binance, Tether, and Circle to freeze the stolen funds, and it has been reported that $USDT has already been frozen.
However, the attacker managed to bridge 2,403,165 $USDC through Gnosis Proxy, allowing them to move a portion of the stolen funds. The platform’s team has since identified and removed the malicious contract and has taken additional security measures to prevent similar attacks from occurring in the future.
Block Data Reference
Malicious transaction:
https://snowtrace.io/tx/0x1266a937c2ccd970e5d7929021eed3ec593a95c68a99b4920c2efa226679b430
Attacker’s address:
https://snowtrace.io/address/0xeff003d64046a6f521ba31f39405cb720e953958
Malicious contract:
https://snowtrace.io/address/0x67afdd6489d40a01dae65f709367e1b1d18a5322
Transfer transactions:
https://snowtrace.io/tx/0x5e3eb070c772631d599367521b886793e13cf0bc150bd588357c589395d2d5c3
https://snowtrace.io/tx/0x76ceab91aef320d0556029861dc1dde423d100e2a85f7ca4891a924efce4ed5a
3. DForce — $3.65m Lost (Oracle Issue, February 10)
On February 10th, the DeFi aggregator platform dForcenet fell victim to an attack, and the attacker made a profit of approximately $3.65 million.
The attacker employed a flash loan to borrow Wrapped Ethereum (WETH), swapped it into Ethereum (ETH), and added liquidity to the wstETH/ETH pool on Curve, earning wstETHCRV tokens. A portion of the tokens was then deposited in the Curve wstETH-CRV gauge, receiving wstETH-CRV gauge tokens, which were further deposited in the dForce wstETH/ETH Vault, and used to mint share tokens and USX tokens.
The attacker then removed liquidity using the “remove_liquidity” function, triggering the fallback function of the attack contract, which ultimately decreased the virtual price in the wstETH/ETH pool.
As a result, the attacker liquidated other users in the dForce wstETH/ETH Vault, profiting from the manipulated virtual price. The stolen funds are still in the attacker’s address as of now.
The root cause of the attack was the exploitation of the process of transferring native tokens before burning LP when removing liquidity in the wstETH/ETH pool. This triggered the callback for receiving native tokens, which the attacker manipulated to influence virtual prices and liquidate other users for profit.
Block Data Reference
Exploit TXs:
4. Orion Protocol — $3.0m Lost (Reentrancy, February 2)
On February 2nd, Orion Protocol, a decentralized finance (DeFi) platform that aggregates liquidity from centralized exchanges, fell victim to a reentrancy exploit resulting in a loss of approximately $3 million in Ethereum (ETH).
The attacker utilized manipulated swaps of flash loaned stablecoins and artificially deposited assets twice before withdrawing the inflated balance. To double their balance, the exploiter created and utilized a fake token before making off with the stolen loot. However, Orion CEO Alexey Koloskov confirmed that user funds remained safe and that the damage was contained within an internal broker account.
After the exploit, the attacker sent 1,100 ETH through the Tornado Cash mixer, which allows users to enhance their anonymity on the Ethereum network, and still holds 657 ETH in their balance.
Block Data Reference
Exploit TX:
https://bscscan.com/tx/0xfb153c572e304093023b4f9694ef39135b6ed5b2515453173e81ec02df2e2104
Exploiter addresses:
https://bscscan.com/address/0x837962b686fd5a407fb4e5f92e8be86a230484bd
https://bscscan.com/address/0x3dabf5e36df28f6064a7c5638d0c4e01539e35f1
https://etherscan.io/address/0x3dabf5e36df28f6064a7c5638d0c4e01539e35f1
Attacker contract:
https://bscscan.com/address/0x84452042cb7be650be4eb641025ac3c8a0079b67
5. Dexible — $2m Lost (Access Control, February 17)
On February 17th, 2022, the multichain exchange aggregator Dexible suffered a flash loan attack that resulted in the loss of over $2,000,000 worth of Ethereum (ETH). Dexible is a decentralized exchange aggregator that allows users to trade on centralized exchanges (CEXs) without losing custody of their assets.
The attacker was able to exploit Dexible’s v2 contracts by using the app’s selfSwap() function to move over 2,000,000 $USD worth of cryptocurrency from users who had authorized the app to move their tokens.
Block Data Reference
Attacker address:
https://etherscan.io/address/0x684083f312ac50f538cc4b634d85a2feafaab77a
Funds transfer example transaction:
https://etherscan.io/tx/0x4393ca721175e8bc97458f97b5118927a026e73b4a6964d16035090b05686a8c
DeFi Exploit Trends
As can be seen from the scale of the losses in February, a large majority of losses came from just one key case: BonqDAO.
This amounted to over $120 million being lost. Notably, this means that the biggest losses this month were due to oracle issues, which have been becoming increasingly common in recent months.
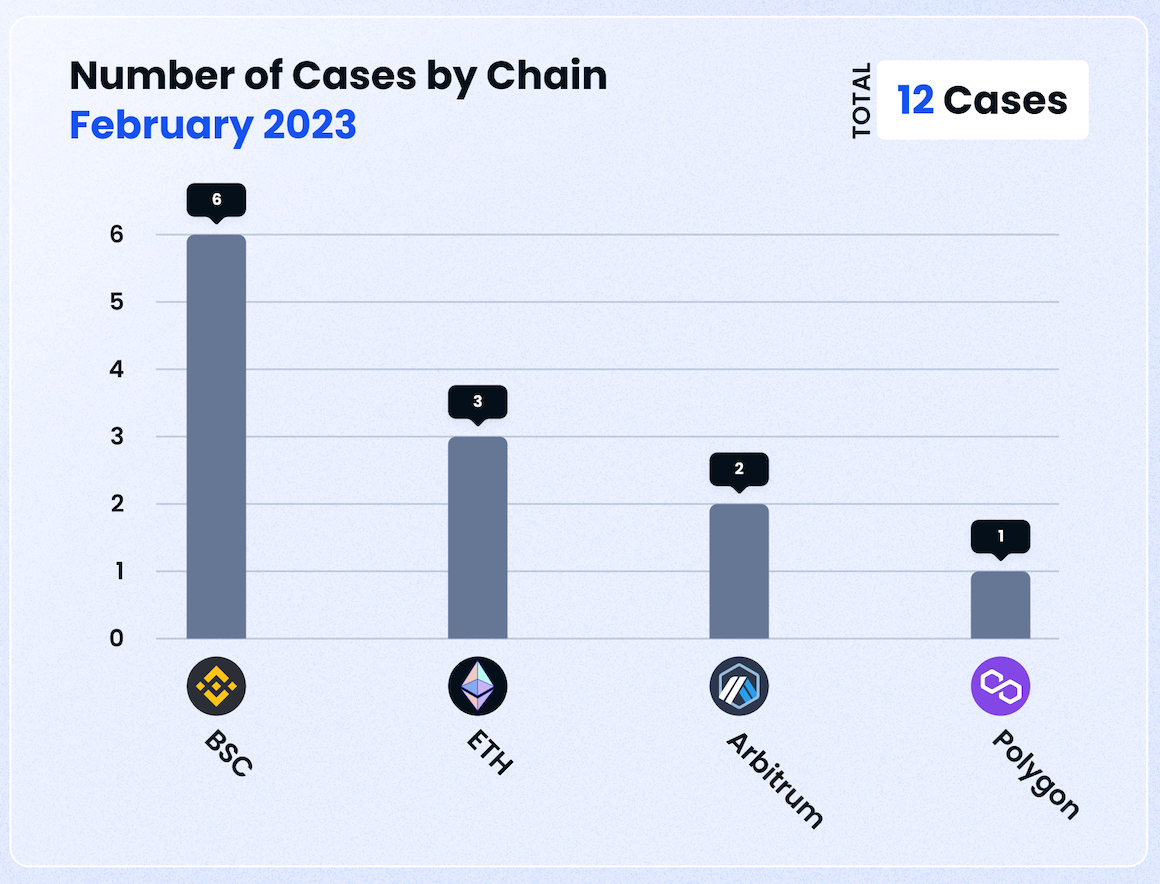
This also makes Polygon the chain where cumulative losses this month have been the largest.

Meanwhile, BNB Smart Chain unfortunately remains popular for crypto criminals, with 6 cases happening this month, as compared to 3 on Ethereum, 2 on Arbitrum and 1 on Polygon.
Funds Recovered
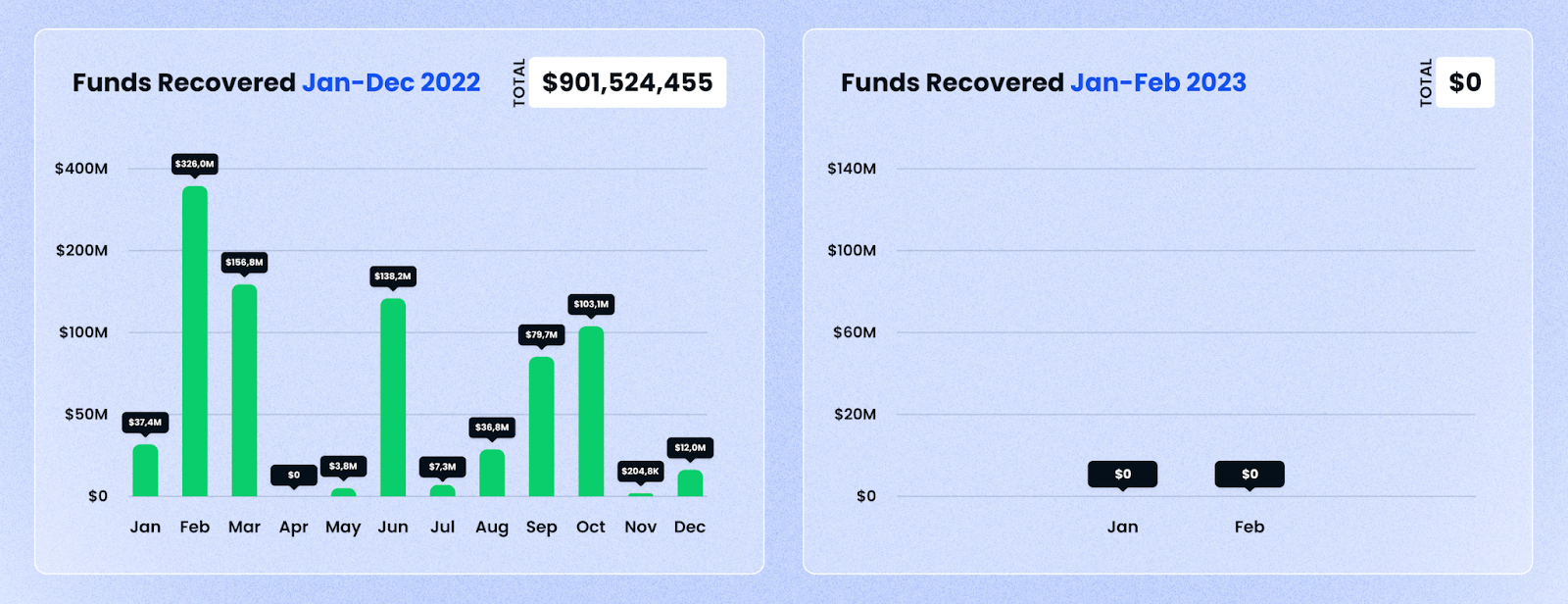
Unfortunately, in February, none of the losses were ultimately recovered. This is the second successive month where we are observing a break in the trend of increasing recoveries we have seen over the past few months, on a year-on-year basis.
Types of Exploit
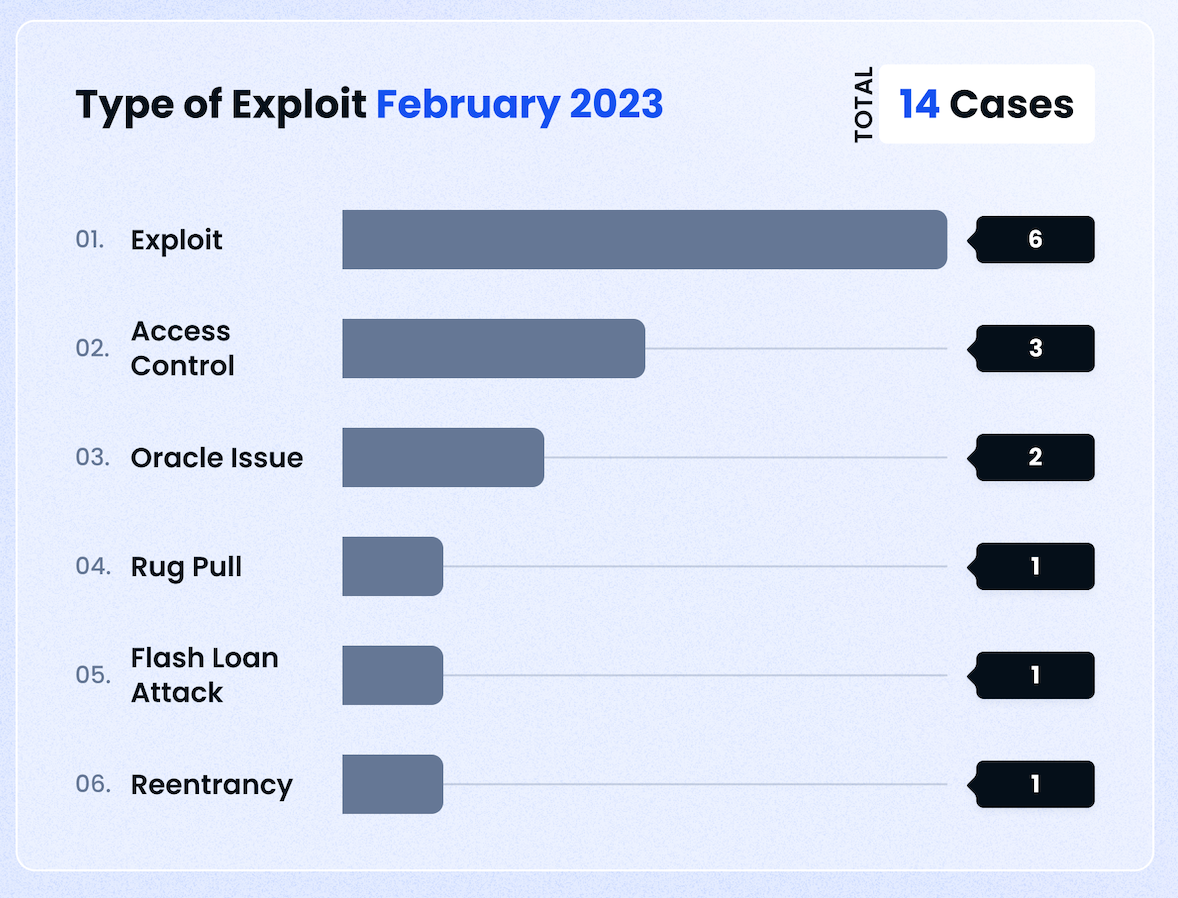
In terms of frequency, smart contract exploits were the most popular among criminals. This was followed by access control issues, and of course, oracle issues that played a role in the biggest case this month.
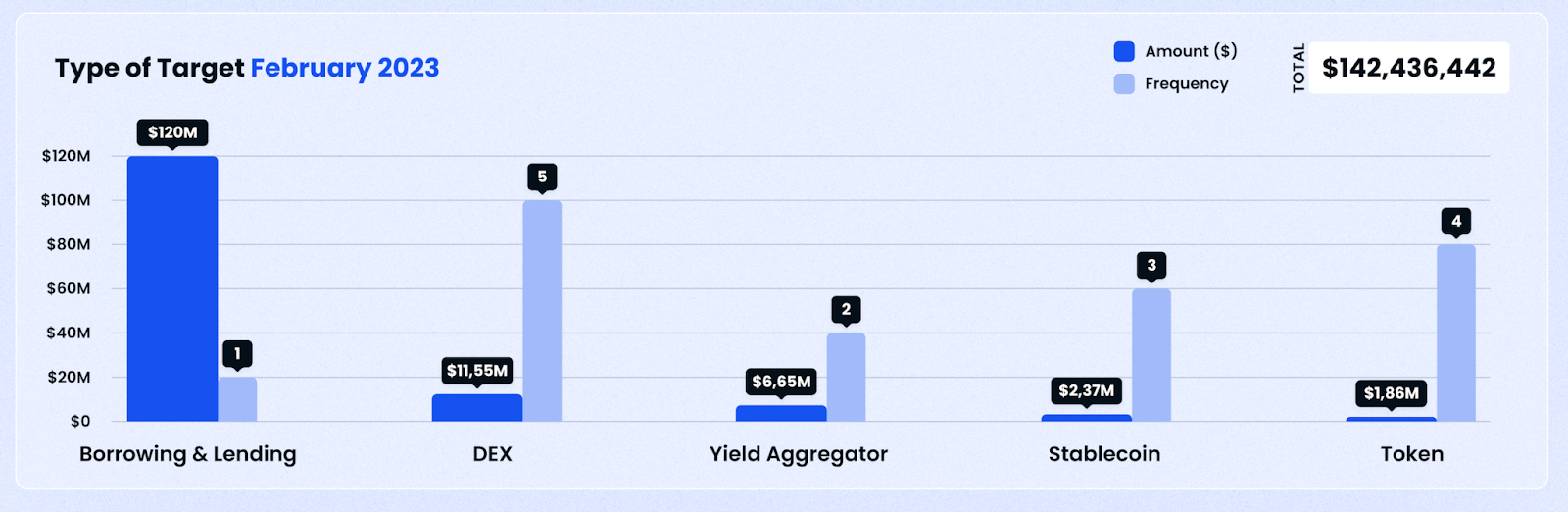
Attack Vectors
In terms of attack vectors, DEXes and Tokens proved to be popular targets this month — this is unsurprising — in previous months, tokens have often been used as a vehicle to rug investors. At the same time, DEXes hold a large amount of liquidity to facilitate trading, and can therefore be attractive targets to scammers and hackers. In terms of amounts lost, though, Lending and Borrowing protocols took the prize, though this was driven by just one event — BonqDAO.
Conclusion
In summary, the sharp increase in losses this month is a reminder of how investing in the decentralized finance (DeFi) space requires a certain level of risk management and vigilance. It is imperative for investors to inform themselves on potential threats and to take the necessary measures to safeguard their investments. At De.Fi, we recognize the importance of providing education in navigating the complex and ever-changing DeFi landscape. We are thus dedicated to providing our users with the resources they need to make informed investment decisions in the sector.
A smart contract originally conceived by Uniswap, Permit2 manages the approval of token transfers via gasless signatures.
On that front, DeFi wallets are in high demand and Rabby Wallet is an option that's quickly gaining mindshare. But the fact of the matter is, Rabby is only one in a sea of wallet providers. Users must carefully weigh their options to know whether or not it's the right choice.
During Q2 of 2024, we noticed a significant increase in crypto losses caused by hacks and scams - the total was $430,118,000, which is much higher than what we observed during this period last year (a loss of $204,308,280).
In the rapidly expanding universe of web3 and decentralized finance (DeFi), selecting a reliable and secure wallet is crucial. Rainbow Wallet has emerged as a popular choice, especially for those new to the crypto world.
In this blog, we'll walk through what Gnosis token approvals are and how you can audit + revoke them using the free De.Fi Shield tool.
During Q1 2024 ... total losses amounting to $414,875,820 across a range of exploits and security incidents.
© De.Fi. All rights reserved.