These days a number of people have found themselves falling victim to scams, hacks and pretty much learning that REKT events happen almost every day!
Our REKT Database now contains 2,683 scams explained by our Solidity engineers. 14 REKT cases happened in January which equals more than $130M funds lost.
By our projection, in the near future, we will observe scams happening every day but with De.Fi you can catch this very early on and protect yourself and your investments better than before.
Soon we will publish our yearly report on scams and exploits in 2021. We also included there a short cheat sheet on how to ensure your safety in DeFi.
But now, let’s dive into the TOP-7 cases in January!
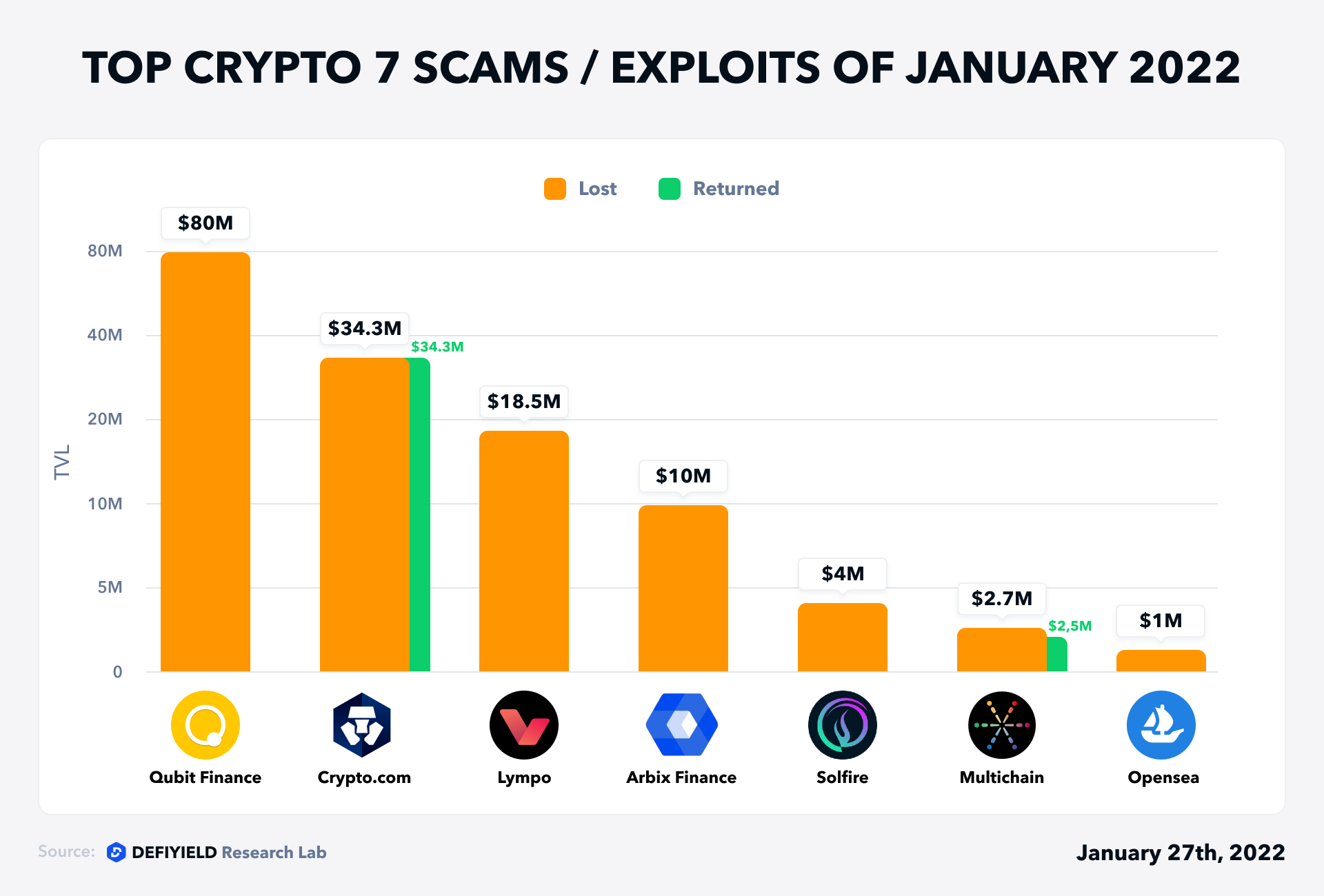
7. Opensea Case — $1M Lost (Exploit, DeFi)
A bug has been exploited to purchase NFTs from users of OpenSea, at well below market value.
At least five attackers were detected who used this loophole to acquire at least twelve NFTs for far less than their market worth. Bored Ape Yacht Club, Mutant Ape Yacht Club, Cool Cats, and Cyberkongz NFTs are among them.
For example, at around 7 am on January 24, a Bored Ape Yacht Club NFT #9991 was purchased for 0.77 ETH ($1,800). This family of NFTs currently sells for at least $198,000. Twenty minutes later the hacker sold the NFT for 84.2 ETH ($196,000) — realizing a profit of $194,000.
One attacker, going by the pseudonym “jpegdegenlove” paid a total of $133,000 for seven NFTs — before quickly selling them on for $934,000 in ether. Five hours later this ether was sent through Tornado Cash, a “mixing” service that is used to prevent blockchain tracing of funds.
Victims were partially compensated.
Read more in the REKT Database →
6. Multichain Case —$2.7M Lost (Exploit, DeFi)
On Jan 18, Multichain urged users to remove approvals for six cross-chain tokens (WETH, PERI, OMT, WBNB, MATIC, AVAX), while the users haven’t revoked WETH approval were exploited (WETH 602.69 total affected).
The whitehat hacker returned 259 ETH at:
https://etherscan.io/tx/0x2bbd6a6a0d4d56db0b231465f56c5fca9d11e874109277a576b69f2acf1ee7a9
Read more in the REKT Database →
5. Solfire Case — $4M Lost (Exit scam, DeFi)
Solfire executed rug pull by withdrawing assets from the Solfire hot wallet.
The list of stolen funds:
- 6.3848 BTC
- 104.86 soETH
- 4,414.47 SOL
- 1,537,822.99 USDT
- 299,702.9 USDC
- 4,030.4 mSOL
- 1,457.89 LUNA
- 26,347.69 RAY
- 46,110.45 SRM
- 830,270.48 SBR
Initial gas funding was performed through the following wallet and then funds were bridged to Solana:
https://etherscan.io/address/0xe8032c0270164819bbee809324e09d899cc97f18
Stolen funds have arrived in the next wallets:
https://etherscan.io/address/0xc5afc6c1d4002dc9bc765542a17bb0fc49044ec5
https://etherscan.io/address/0x1e669254badd2866b217983d6a2fcbbf07d66ff7
Part of stolen funds was deposited into Curve pool:
https://etherscan.io/tx/0x6719f05a0c62fa06f513b56fb9276b7b7ac38253960ac5d692c3476bfcadf292
FIRE tokens circulation supply was sent to this address:
https://solscan.io/account/3SfihoLDctTc7fna3akRMkVuSFrhBkCzVv6scBJnjQSF#splTransfers
The liquidity from the pair was removed.
Read more in the REKT Database →
4. Arbix Finance Case — $10M Lost (Exit scam, DeFi)
The rug pull flow:
- ARBX contract has mint() with onlyOwner function
- 10M ARBX were minted to 8 addresses
- ~4.5M ARBX were minted at:
https://bscscan.com/tx/0x4707d30a8d8152eebad1cdcae1d93af24cb9a344b447412ee1d65638b5c3db6f
- The 4.5M ARBX were then dumped by the token recipient
- Deposited users’ assets were drained from several pools, the example transaction:
https://bscscan.com/tx/0xfbba507c8e90a264d5e77e5db854f5697572da1681f3647d4fa4381f7ef825b9
- Stolen funds were bridged to Ethereum on this address:
https://etherscan.io/address/0xdc85c1eb22b0ece7be559a83fd788fe57f5a7a9f
Read more in the REKT Database →
3. Lympo Case —$18M Lost (Access control, DeFi)
On 10 January 2022 at approximately 2:32 PM (UTC +2), hackers managed to gain access to Lympo’s operational hot wallet and stole a total of approximately 165.2 million LMT from it.
Hackers distributed tokens to several external addresses which then sold them on different DEXs.
Read more in the REKT Database →
2. Crypto.com Case —$34M Lost (Access control, CeFi)
On Monday, 17 January 2022 at approximately 12:46 AM UTC Crypto.com’s risk monitoring systems detected unauthorized activity on a small number of user accounts where transactions were being approved without the 2FA authentication control being inputted by the user. This triggered an immediate response from multiple teams to assess the impact.
All withdrawals on the platform were suspended for the duration of the investigation. Any accounts found to be impacted were fully restored. Crypto.com revoked all customer 2FA tokens and added additional security hardening measures, which required all customers to re-login and set up their 2FA token to ensure only authorized activity would occur.
The hacker stole:
- 4,836.26 ETH
- 443.93 BTC
- $66,200 in other currencies
Stolen funds were deposited into the Tornado Cash mixer.
Read more in the REKT Database →
1. Qubit Case — $80M Lost (Exploit, DeFi)
The attacker:
- funded his wallet with 0.8887725 ETH from Tornado Cash
- sent 16 deposit transactions to QBridge of Ethereum
- sent 16 voteProposal transactions to QBridge contract of BSC by Qubit Relayer
- a number of xETH tokens were minted by 16 voteProposal transactions, and liquidity in Qubit was withdrawn using this as collateral.
The attacker called the QBridge deposit function on the Ethereum network, which calls the deposit function QBridgeHandler. QBridgeHandler should receive the WETH token, which is the original tokenAddress, and if the person who performed the tx does not have a WETH token, the transfer should not occur.
In summary, the deposit function was a function that should not be used after depositETH was newly developed, but it remained in the contract.
Read more in the REKT Database →
As always, stay safe and DYOR!
If you’ve been a victim of one of the explained or other scams — share your story and tag us on Twitter. We will investigate the case and extend our database with your REKT story.
For more De.Fi updates you can visit us at Website https://de.fi/ 📱 Telegram https://t.me/DeDotFi 🐦Twitter https://twitter.com/DeDotFi