DeFi Rekt Report October 2025: $38.6 Million Lost Across 9 Exploits
October 2025 saw a total of $38.63 million lost across nine distinct security incidents in both centralized and decentralized platforms.

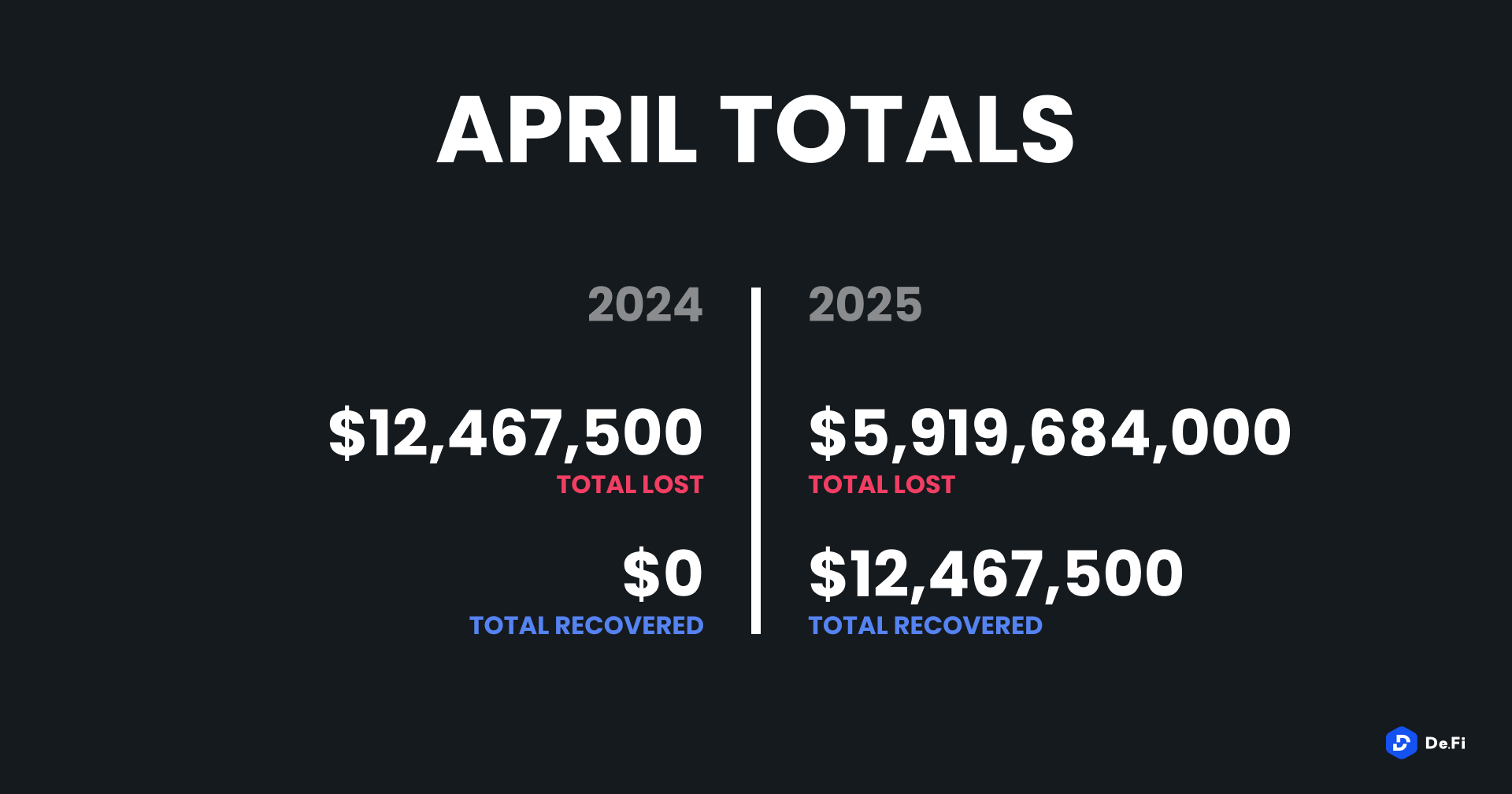
April 2025 witnessed a large escalation in exploit volume and value, with a massive $5,919,684,000 being stolen in 10 confirmed events. While minor recoveries were realized, to the tune of $2.8 million, this month’s metrics were overwhelmed by a single gigantic exit scam, which skewed aggregate losses to record levels in the second part of this year. The total value lost in the top 3 events accounted for over 99% of the month’s aggregate loss.
The biggest loss was suffered by Mantra, which pulled off a purported $5.5 billion exit scam, the most significant individual incident of 2025 so far. A phishing attack through an externally owned address (EOA) came in second with $330 million in losses, followed by UPCX, which lost $70 million in another highly publicized hack. The other exploits, while much lower in comparison, targeted ecosystems like Base, Solana, zkSync Era and BSC, exposing persistent contract vulnerabilities and poor access controls.
April was defined by a mix of traditional smart contract vulnerabilities and centralized frauds. The Mantra exit scam dramatically overshadowed all other activity, drawing comparisons to historical rug pulls like FTX and Thodex. The phishing EOA case demonstrated that social engineering and user-level breaches continue to yield outsized results for attackers. Meanwhile, the UPCX breach re-emphasized the risks tied to rapidly scaling platforms with under-tested code.
Among smaller-scale attacks, Loopscale, KiloEx and ZKsync fell victim to smart contract and access control vulnerabilities. A pattern of insufficient administrative control persisted across several incidents, particularly in BTCM App, The R0AR and ACB. The dispersion of exploit types, despite the month’s headline numbers, suggests attackers remain opportunistic and chain-agnostic.
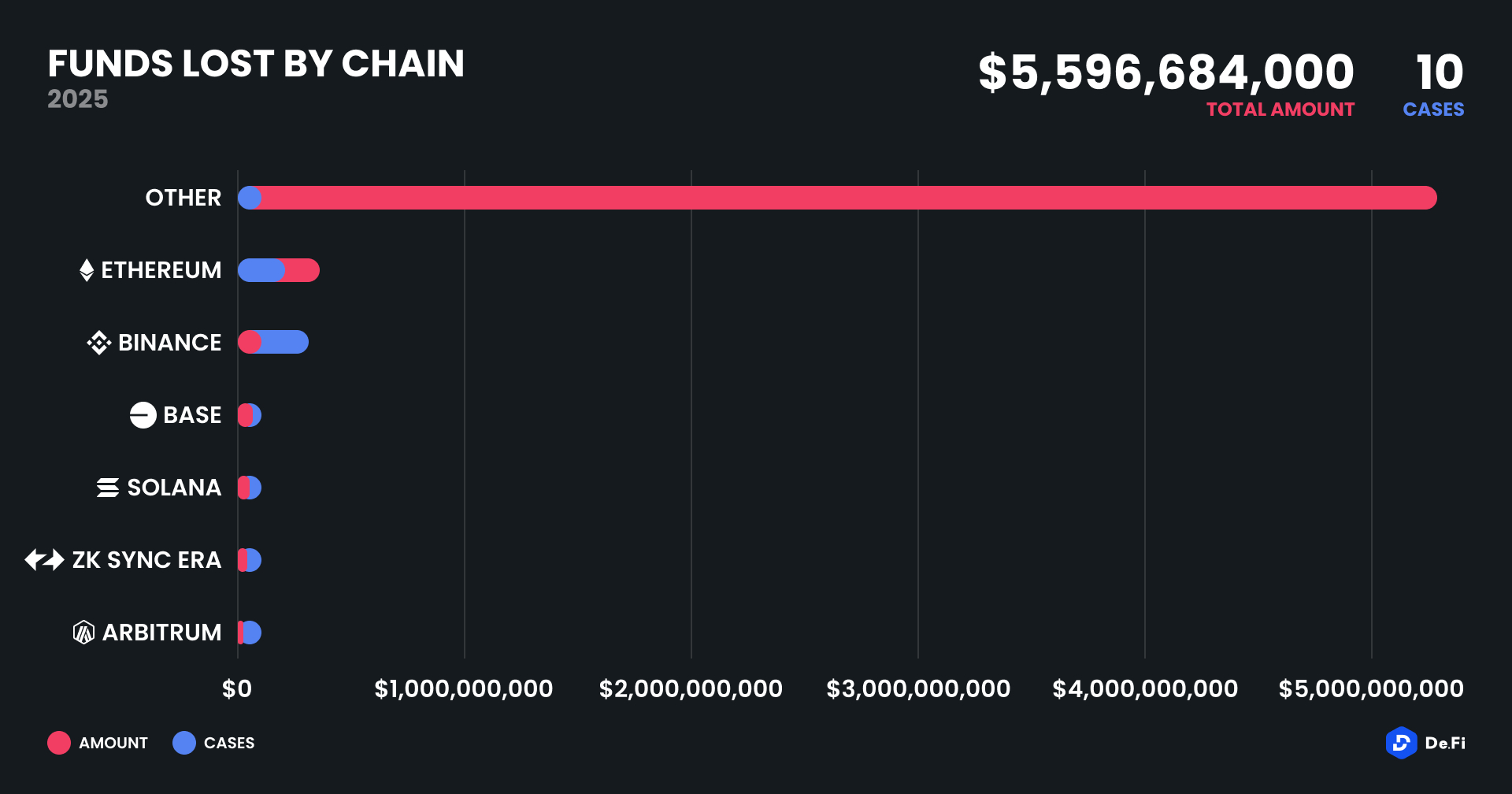
April’s damage was dominated by unclassified chains (referred to as “Other”) due to the Mantra incident. Ethereum followed, registering $70.79 million in losses across two cases. Binance Smart Chain (BSC) was hit by three separate incidents totaling $7.09 million. Other affected chains included Base ($7 million, KiloEx), zkSync Era ($5 million, ZKsync), Solana ($5.8 million, Loopscale) and Arbitrum ($1 million, BTCM App).
This spread reflects the continued presence of vulnerabilities on both mature and newer chains. Despite growing investment in security tooling, access control and contract auditing remain uneven across ecosystems.
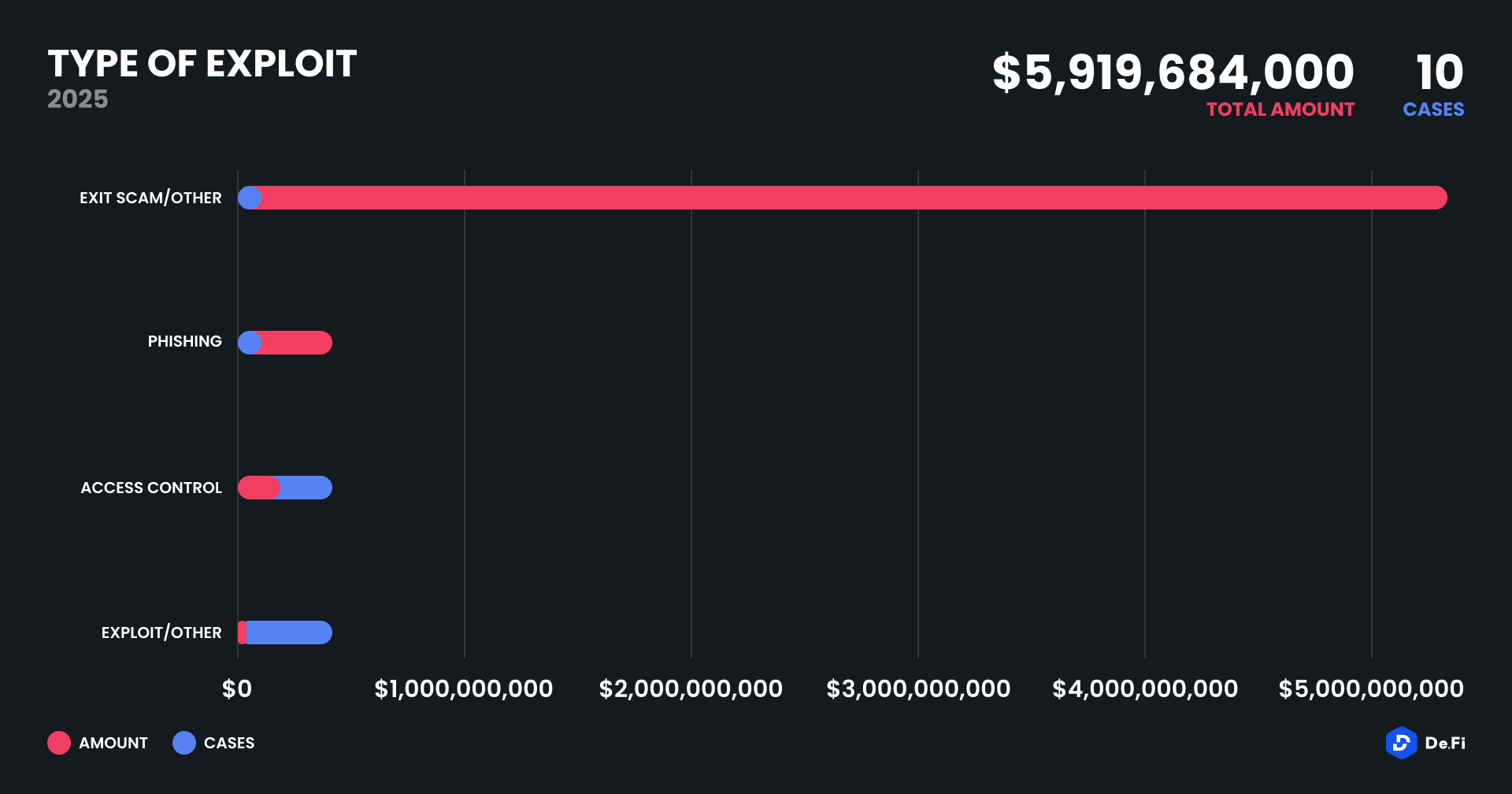
Out of the 10 recorded cases in April, Access Control issues and Phishing dominated the technical landscape. The Mantra loss was classified as an Exit Scam, representing over 93% of all losses. The phishing EOA incident came next at $330 million, highlighting the persistent danger of off-chain exploits.
Access Control vulnerabilities featured in at least 4 incidents (KiloEx, Loopscale, ZKsync, ACB), confirming the need for improved role separation, function gating and multisig usage. Smart contract bugs and permission exploits contributed to the losses at BTCM App, The R0AR and AIRWA.
Despite increased security awareness in the ecosystem, the diversity of exploit techniques suggests that both operational and technical vulnerabilities remain endemic.
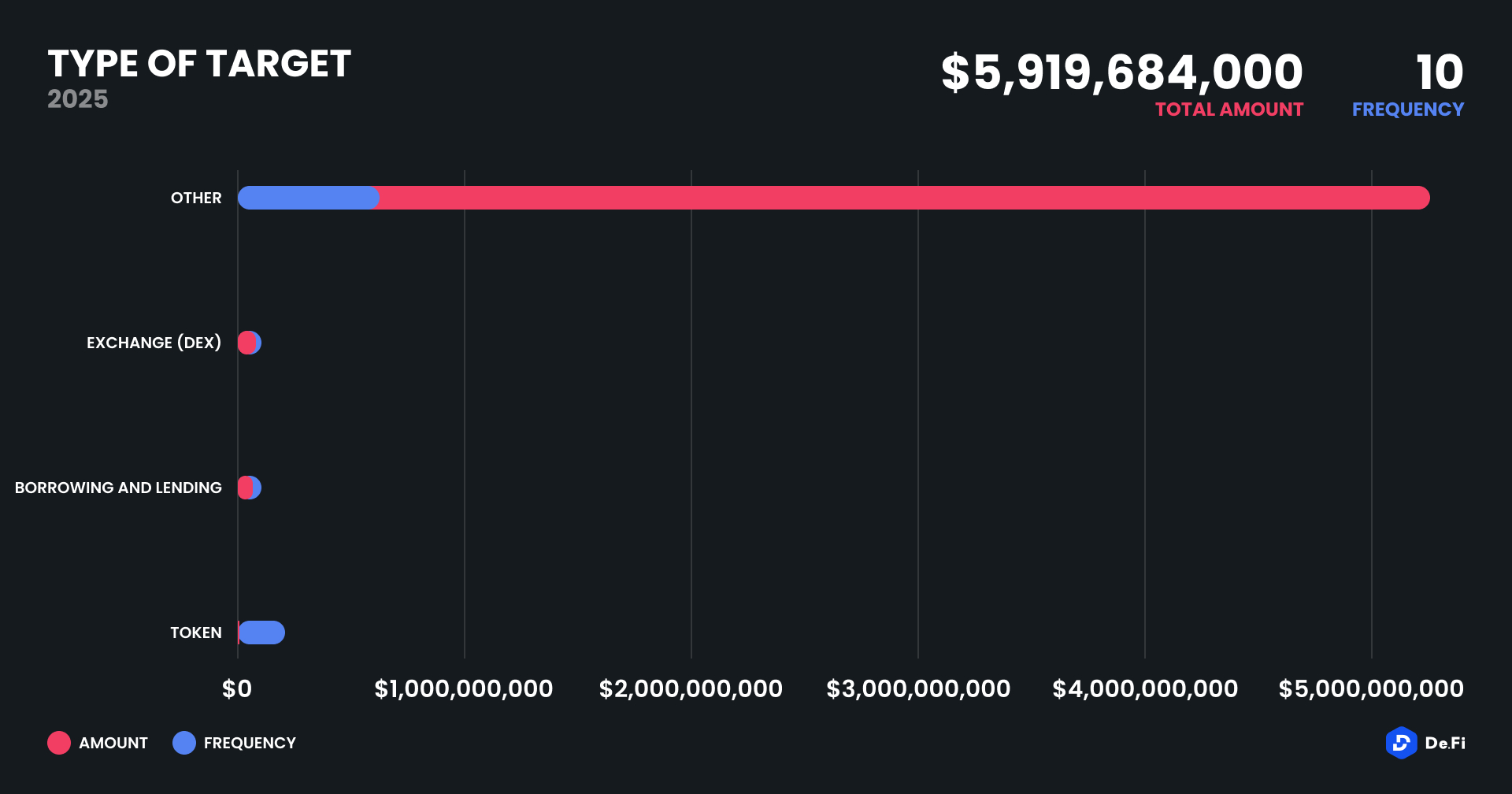
A majority of incidents in April (6 of 10) were categorized as “Other,” indicating unaudited multi-purpose platforms or protocols without clear classification. The highest-profile DEX exploit occurred on KiloEx, which lost $7 million due to access mismanagement. Lending protocol Loopscale saw $5.8 million drained on Solana, continuing the trend of vulnerabilities in borrowing platforms.
Two token-based platforms, ACB and AIRWA, suffered small but avoidable breaches, each under $100,000, reinforcing the theme of poor token contract design and administrative access mismanagement.
1. Mantra Exit Scam – $5,500,000,000
On April 13, 2025, Mantra’s OM token crashed by over 90%, wiping out more than $5.5 billion in market cap. The event appears to be a coordinated insider dump rather than a technical smart contract exploit.
The price collapse began after suspicious on-chain activity showed over 43 million OM tokens—roughly 4.5% of the circulating supply—being sent to exchanges like OKX just days prior to the crash. A particularly large transfer of 14 million OM was identified, further fueling speculation of insider involvement. Although Mantra co-founder JP Mullin denied any wrongdoing and claimed centralized exchanges liquidated OM margin positions irresponsibly, blockchain data suggests otherwise. The OM token had recently undergone changes in emissions and tokenomics, which may have enabled early investors or insiders to unlock and sell significant volumes. The Mantra team insisted that team wallets remain locked, yet failed to provide clear evidence absolving themselves. While the price partially recovered to $1.10, the scale and suddenness of the drop raised red flags across the crypto community, prompting comparisons to the Terra collapse and triggering calls for deeper scrutiny of token transparency and centralized exchange practices.
2. Phishing EOA Incident – $330,000,000
On April 28, 2025, a social engineering attack led to the theft of 3,520 BTC (~$330.7M) from an individual user.
The attacker used social engineering to deceive an elderly U.S. victim into transferring 3,520 BTC to the address bc1qcrypchnrdx87jnal5e5m849fw460t4gk7vz55g. Soon after the theft, the funds began moving through over six instant exchanges and were rapidly converted into Monero (XMR), contributing to a 50% spike in XMR’s price. This laundering tactic was likely chosen for its privacy features, making tracking difficult. The event has been confirmed as a non-smart-contract exploit, and instead a high-value personal compromise—highlighting ongoing risks from social engineering in crypto.
3. UPCX Exploit – $70,000,000
On April 1, 2025, UPCX suffered an exploit, leading to the theft of 18.4M UPC (~$70M). The attacker gained access to the ProxyAdmin contract, upgraded it, and used the withdrawByAdmin function to drain funds from three management accounts.
The attacker compromised the ProxyAdmin contract, which controls contract upgrades. They modified it to introduce a malicious function, withdrawByAdmin, enabling them to transfer 18.4M UPC (~$70M) from three management accounts. The funds remain untouched at address 0xFf7…334, suggesting further laundering or negotiation attempts. UPCX has suspended deposits/withdrawals but claims user assets are safe while investigations continue.
4. KiloEx Access Control Breach (Base) – $7,000,000
On April 14, 2025, KiloEx was exploited due to a contract vulnerability, resulting in the loss of an undisclosed amount of funds from its Vault.
The attacker exploited a critical lack of access control in the MinimalForwarder contract, enabling unauthorized calls that manipulated oracle prices. Through a multi-step function call chain involving MinimalForwarder, PositionKeeper, Keeper, and ultimately the KiloPriceFeed, the attacker was able to pass a forged signature and arbitrary data, bypassing intended permission checks. By doing so, they first set the oracle price to an abnormally low value to open a leveraged long position, then artificially raised the price to close the position for profit. The malicious activity originated from the wallet 0x00fac92881556a90fdb19eae9f23640b95b4bcbd, which has since begun bridging the stolen funds to BNB Chain via Polyhedra. KiloEx has halted platform activity, is working with security firms and partners to trace the stolen assets, and plans to launch a bounty program while preparing a detailed postmortem report.
5. Loopscale Exploit (Solana) – $5,800,000
On April 26, 2025, Loopscale was exploited due to a pricing system vulnerability, resulting in the loss of approximately 39,474 SOL (~$5.8M), though over $2.8M has since been returned.
The attacker exploited a flaw in Loopscale’s pricing mechanism, enabling them to manipulate loan conditions and extract funds from the SOL and USDC Genesis Vaults. In response, the Loopscale team temporarily suspended most app functions while investigating the breach and coordinating with security partners and law enforcement. A message was sent directly to the exploiter, offering a whitehat agreement: return 90% of the stolen funds (35,527 SOL) in exchange for keeping a 10% bounty (3,947 SOL) and exemption from liability. As of April 27, the exploiter returned a total of 19,463 WSOL (~$2.88M), with funds delivered across multiple transactions. Law enforcement, exchanges, and bridge protocols have been alerted, and further legal steps are pending if no agreement is reached. A full post-mortem is in progress.
6. ZKsync Smart Contract Exploit – $5,000,000
On April 15, 2025, a compromised admin account exploited the ZKsync airdrop distribution contracts and stole approximately $5 million worth of unclaimed ZK tokens.
The attack stemmed from the compromise of the admin address 0x842822…587D, which had privileged access to three airdrop distribution contracts. Using this access, the attacker called the sweepUnclaimed() function and minted around 111 million unclaimed ZK tokens, representing roughly 0.45% of the total token supply. This unauthorized minting directly inflated the circulating supply and resulted in the attacker gaining control of tokens worth about $5 million. Importantly, this was an isolated incident affecting only the airdrop contracts; the ZKsync protocol itself, the core ZK token contract, governance contracts, and capped minters were not compromised. The attacker still holds most of the stolen funds at 0xb1027e…05d3, and recovery efforts are ongoing in coordination with Seal and various exchanges. The ZKsync team has reached out to the attacker to encourage communication and possible fund return.
7. BTCM App Exploit (Arbitrum) – $1,000,000
On April 22, 2025, BTCMapp contracts on Arbitrum were exploited through a logical vulnerability, resulting in ongoing losses exceeding $1 million.
The attackers targeted a flaw in the overPaper function of the BTCMapp smart contract, which lacked proper checks and allowed them to withdraw approximately half of the contract’s balance in repeated calls. The exploit was initiated by a wallet that performed several malicious transactions, systematically draining assets. Following the theft, the attacker began laundering the funds by bridging them to Ethereum using intermediary addresses. The exploit is still in progress, with stolen funds actively moving across chains, prompting investigators and the community to monitor and attempt containment.
8. The R0AR Token Exploit – $790,000
On April 16, 2025, The R0AR staking contract was exploited due to a backdoor vulnerability, leading to the loss of approximately $790,000.
The attack stemmed from a maliciously embedded backdoor in the staking contract during its deployment. Specifically, the attacker preset the user.amount mapping for their wallet (0x8149f77504007450711023cf0eC11BDd6348401F) to a large value directly in the contract’s storage. This manipulation gave the appearance that the wallet had staked a substantial number of tokens. Later, by invoking the emergencyWithdraw() function, the attacker was able to withdraw 100 million $1ROR tokens from the contract. This withdrawal was possible despite the tokens never actually being staked, resulting in the full drain of the contract’s funds. The vulnerability highlights poor storage initialization and the absence of proper validation checks on state variables at contract deployment.
9. ACB Access Control Breach – $60,000
On April 23, 2025, the ACB token on BNB Chain was exploited through an airdrop vulnerability, resulting in losses of approximately $60,000.
The attacker, funded via Tornado Cash, exploited a vulnerability in the ACB token’s airdrop mechanism that allowed them to claim rewards multiple times, draining the airdrop contract. The exploit involved abusing a cash exploit flaw without proper eligibility or duplication checks. After successfully extracting around $60,000, the attacker moved the stolen funds back to Tornado Cash to obfuscate their trail. The compromised contract was a proxy pointing to a vulnerable implementation contract, and the exploit has been confirmed as fully executed.
10. AIRWA Token Exploit – $34,000
On April 4, 2025, AIRWA token on BNB Smart Chain (BSC) was exploited for approximately $34,000 due to a misconfigured public setBurnRate() function.
The vulnerability stemmed from the setBurnRate() function in the AIRWA token contract being publicly accessible. The attacker called setBurnRate(980)—an extremely high burn percentage—and then executed a transfer(pair, 0). This combination caused the pair’s tokens to be burned, manipulating the liquidity pool and allowing the attacker to extract value.
April 2025 marked a seismic month in DeFi and Web3 exploits, driven primarily by the Mantra exit scam. The single event redefined the month’s statistics, masking the ongoing persistence of access control issues, phishing campaigns and smart contract exploits across emerging ecosystems.
With only $2.8 million recovered from nearly $6 billion in losses, the recovery rate was virtually negligible. The month’s exploits highlighted a diverse attack surface, centralized exit scams, phishing and DeFi vulnerabilities, all pointing to the urgent need for stricter governance, real-time auditing and improved operational transparency.
As developers and auditors assess the damage, the April 2025 REKT Report serves as another regular reminder that explosive growth without security discipline remains an existential risk in Web3.
October 2025 saw a total of $38.63 million lost across nine distinct security incidents in both centralized and decentralized platforms.
The third quarter of 2025 marked yet another turbulent period for the DeFi and wider crypto ecosystem, with $434,124,000 lost to exploits, scams, and security failures across both centralized and decentralized platforms.
June 2025 witnessed another alarming month for Web3 security, with a total of $114,768,000 lost during 11 separate attacks
May 2025 saw both DeFi and CeFi security once again under attack, with $275,953,000 lost across just 8 recorded incidents
April 2025 witnessed a large escalation in exploit volume and value, with a massive $5,919,684,000 being stolen in 10 confirmed events.
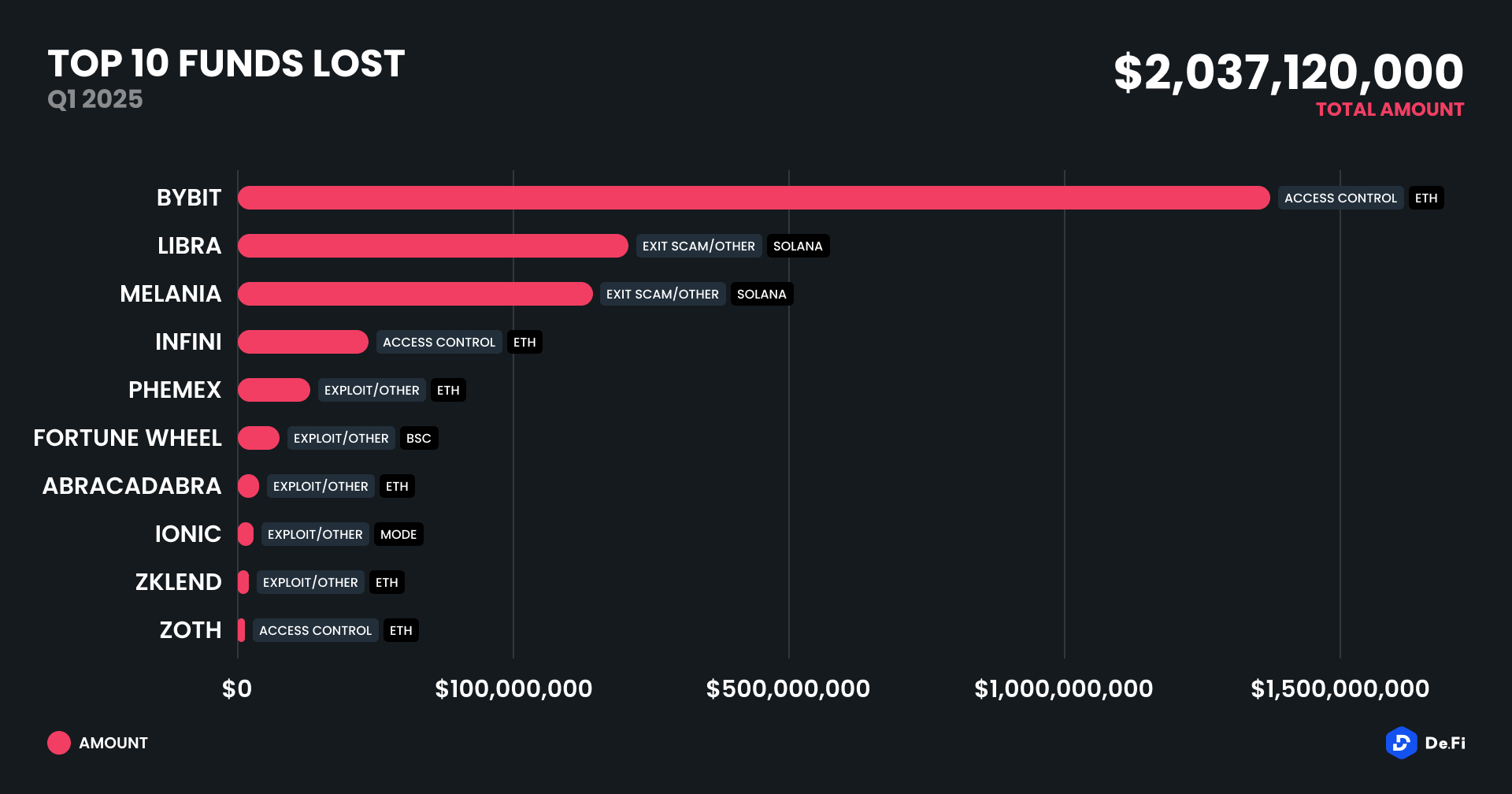
Q1 2025 marked one of the worst quarters in blockchain exploit history, with total recorded losses topping $2,052,584,700 across 37 incidents
© De.Fi. All rights reserved.