DeFi Rekt Report October 2025: $38.6 Million Lost Across 9 Exploits
October 2025 saw a total of $38.63 million lost across nine distinct security incidents in both centralized and decentralized platforms.

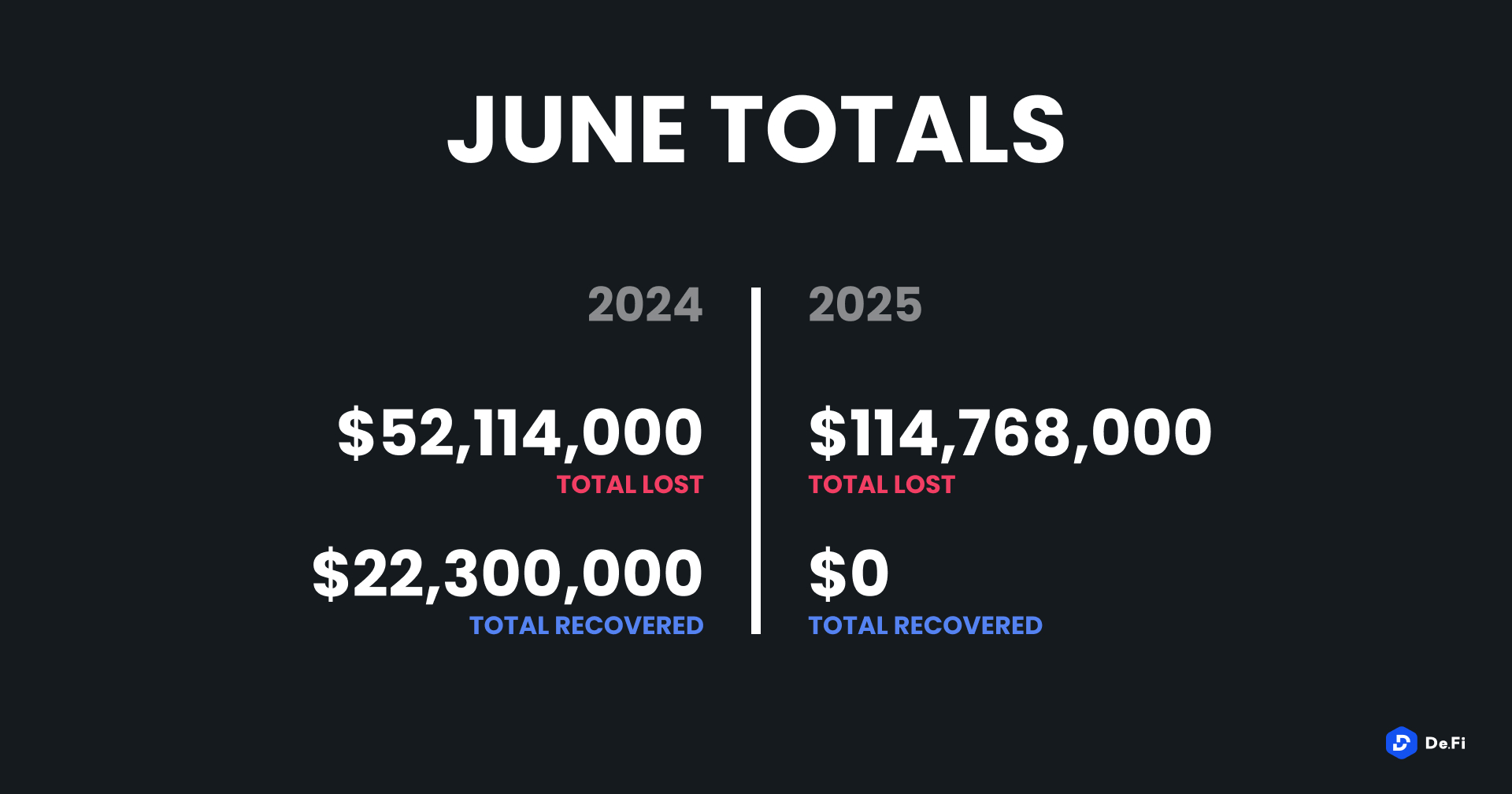
June 2025 witnessed another alarming month for Web3 security, with a total of $114,768,000 lost during 11 separate attacks. This figure doubled the loss in June 2024 ($52.1 million), indicating an existing vulnerability in both centralized and decentralized networks. No funds were recovered in the month, reflecting lackluster failure to remediate even as exploit complexity continues to increase.
The stand-out attack of the month was the exploitation of Nobitex, centralized Iranian exchange, which cost $82 million in damage alone—ranking as the single most costly event since the Bybit attack a few months previously.
The month was marked by an abrupt return to centralized exchange exploits, as Nobitex’s access control problem alone resulted in more than 70% of the total month losses. Other significant incidents included the $16.1 million stolen from Bitcoin Layer 2 protocol AlexLab and the $9.5 million attack on Ethereum-based protocol Resupply.
Overall, the mix of access control and smart contract logic vulnerabilities resulted in 11 instances of exploits. This was largely a repeat of a trend seen throughout 2025—where both small-cap projects and large centralized actors are more than ever vulnerable to very simple but devastating attacks.
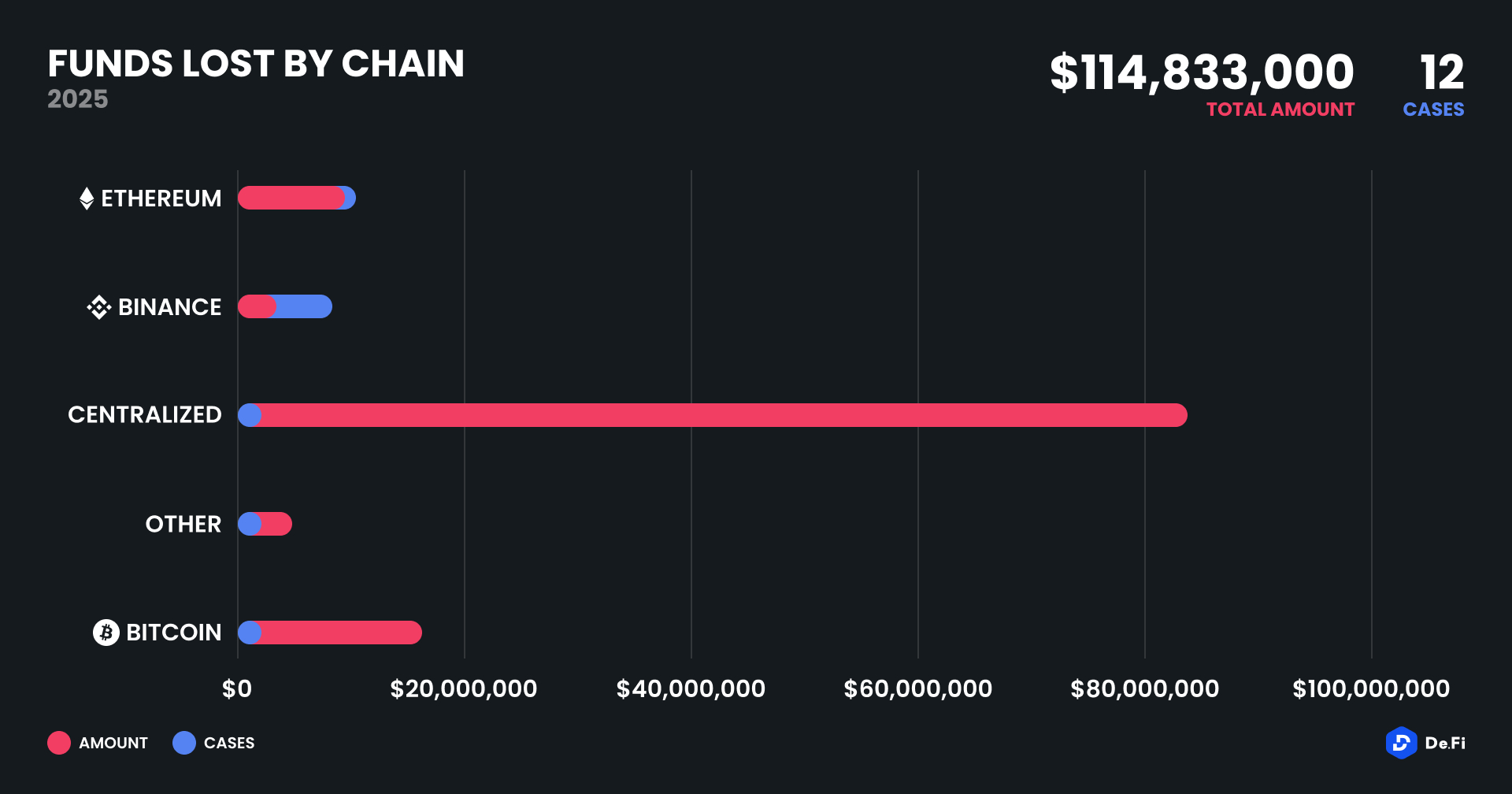
Ethereum was the most attacked blockchain by incident frequency with five separate attacks totaling $10.63 million in lost funds yet again. However, on a monetary value basis, exchanges centralized dominated with only the single $82 million loss at Nobitex. Bitcoin appeared in only one significant case – AlexLab – which accounted for $16.1 million, indicating ongoing security vulnerabilities even in Bitcoin-based Layer 2 platforms. Binance Smart Chain ranked second with three lower-value incidents, with $2.4 million lost. Nervos and other chains were also impacted, losing $3.7 million due to an access control vulnerability. The growing occurrences of multi-chain exploits further perpetuate the decentralized and inhomogeneous nature of cross-chain security deployments.
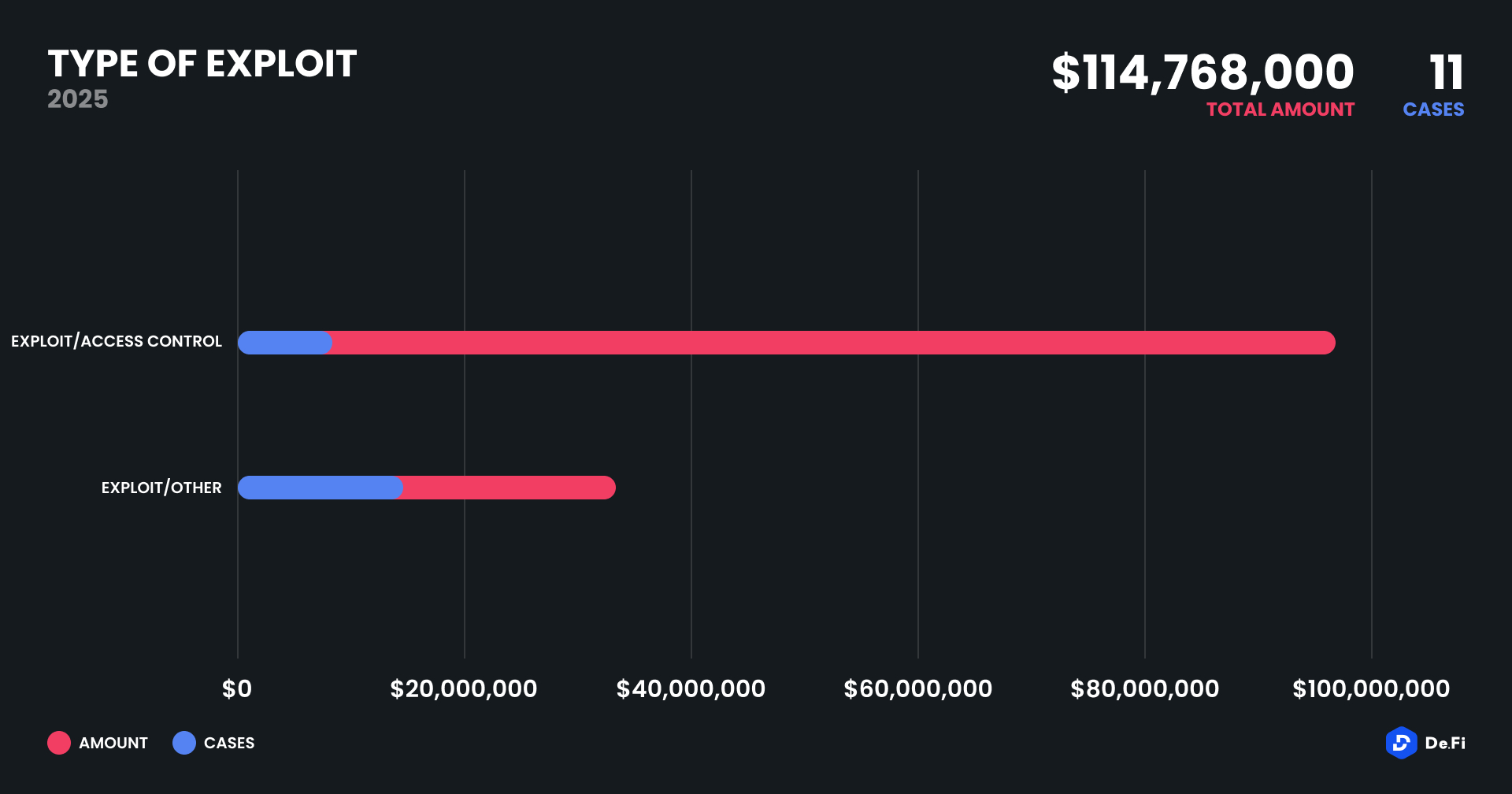
Access control weaknesses remained the dominant vector in terms of total value lost. Four access control-related incidents collectively drained $87.95 million, most notably the Nobitex and Nervos breaches. These attacks typically stemmed from weak internal permissions, private key compromise, or flawed multisig logic.
Seven other incidents fell under general exploit categories – including contract logic vulnerabilities, manipulation of protocol rules, and integrations gone wrong – contributing the remaining $26.8 million in losses. This consistent bifurcation between high-value access control attacks and low- to mid-value smart contract exploits points to an enduring challenge in securing both back-end infrastructure and on-chain logic simultaneously.
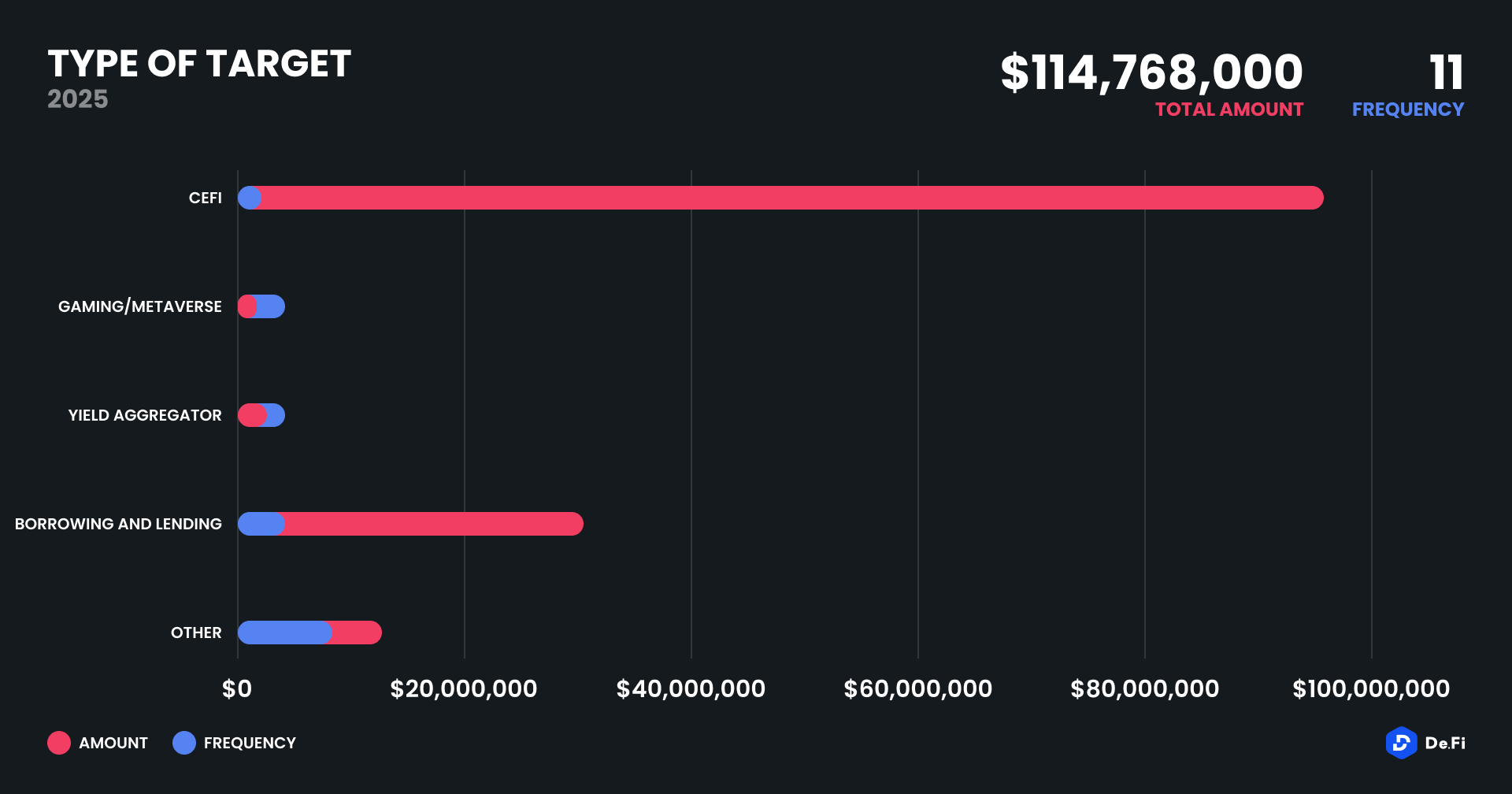
CeFi platforms suffered the brunt of the damage in June 2025. The Nobitex exploit alone placed centralized entities at the top of the loss chart with $82 million in damages, reinforcing concerns around custodial risks and centralized access permissions.
Lending and borrowing protocols followed with two cases amounting to $25.6 million, suggesting renewed targeting of debt instruments and collateral mechanisms. Yield aggregators and gaming/metaverse platforms were affected on a smaller scale, with a combined total of less than $1 million lost.
These categories remain frequent but low-yield targets, often suffering from unaudited contracts and user experience complexity. The “Other” category contributed $6.35 million across four incidents, showing that tail risks remain for smaller or more obscure protocols regardless of niche.
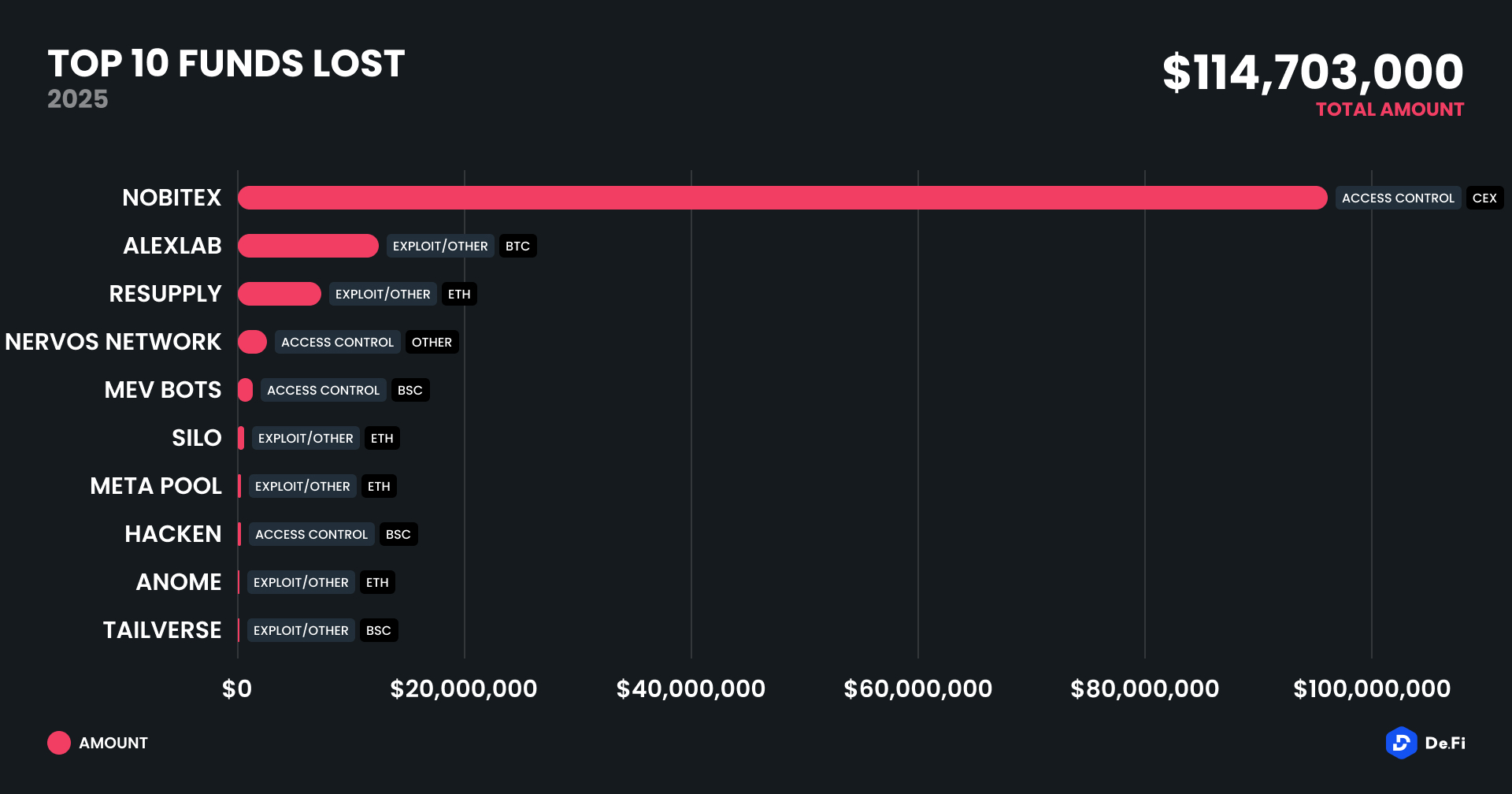
1. Nobitex Exchange Breach – $82M
On June 18, 2025, Iranian crypto exchange Nobitex was hacked for over $82 million. The attack was claimed by the from-Israel hacktivist group Gonjeshke Darande, who also threatened to leak the platform’s internal source code and data.
The Nobitex exploit appears to stem from a critical failure in access controls, allowing attackers to infiltrate internal systems and drain hot wallets across multiple blockchains. The stolen funds span $49.3M on the Tron network, $24.3M on EVM-compatible chains, $2M on the BTC network, $6.7M on DOGE, and an unspecified amount on TON. The attackers used provocative vanity addresses on each chain, such as “TKFuckiRGCTerroristsNoBiTEX…” on Tron and “0xffFFfFFffFFffFfFffFFfFfFfFFFFfFfFFFFDead” on Ethereum. A group calling itself Gonjeshke Darande has claimed responsibility and is threatening to leak internal data and source code. Nobitex confirmed unauthorized access to internal communication systems and portions of hot wallet infrastructure. So far, no swaps or movement of the stolen funds has been observed.
2. AlexLab Bitcoin Layer 2 Exploit – $16.1M
June 6, 2025 – Bitcoin DeFi project AlexLab was exploited for over $16.1M due to a critical flaw in its token listing logic. Fake tokens were used to drain multiple vaults, despite recent audits.
An attacker exploited AlexLab’s self-listing mechanism by deploying a malicious token with a fake transfer function. The token passed AlexLab’s flawed verification checks and was granted vault permissions. By creating a liquidity pool and enabling farming, the attacker triggered vault-level transfers via a single swap-x-for-y call, siphoning out millions in STX, sBTC, aBTC, USDT, USDC, WBTC, and ALEX tokens. Despite AlexLab blaming Stacks’ failure handling, the root cause was insecure access control in AlexLab’s vault contract. Officially, AlexLab claimed $8.3M in losses and promised reimbursement, but onchain analysis shows the actual loss exceeded $16.1M.
3. Resupply Protocol Exploit – $9.5M
On June 26, 2025, Resupply Protocol suffered a $9.5 million exploit affecting only the wstUSR market. The team has identified and paused the compromised contract while confirming that the rest of the protocol remains fully operational.
The attacker exploited a vulnerability in the wstUSR market contract of Resupply, leading to a suspicious transaction resulting in the unauthorized withdrawal of approximately $9.5 million. The exploit was detected by BlockSec’s Phalcon system and involved the manipulation of protocol logic specific to the wstUSR collateral handling, triggering abnormal outflows before the contract was paused.
4. Nervos Network Breach – $3.7M
On June 2, 2025, the Nervos Network’s ForceBridge was exploited, leading to the theft of approximately $3.7 million in assets—$3.1M on Ethereum and $0.6M on BNB Chain. A malicious actor gained control over the bridge and drained funds including USDT, USDC, ETH, DAI, and WBTC, all of which were subsequently swapped to ETH and funneled through Tornado Cash. In response, the Nervos team paused all bridge contracts and is actively investigating the incident with the help of law enforcement and partner exchanges.
The attacker appears to have compromised the ForceBridge contract, gaining unauthorized control and initiating a series of suspicious withdrawals. The stolen funds included: 257,800 USDT; 539.09 ETH; 898,300 USDC; 60,400 DAI; 0.79 WBTC
All assets were swapped to ETH using decentralized exchanges and then laundered through Tornado Cash to obscure their trail. The exploit occurred across multiple chains, primarily Ethereum and BNB Chain. Following detection by Cyvers and other monitoring tools, Nervos paused ForceBridge and acknowledged “abnormal activity,” initiating an internal and external investigation. The protocol’s security flaws—likely in access control or message verification within the bridge—remain under review.
5. MEV Bot Exploit – $2M
On June 25, 2025, multiple attacks on BNB Chain targeted unidentified, closed-source contracts—likely MEV arbitrage bots—resulting in a combined loss of approximately $2 million. Despite speculation, Venus Protocol was not involved.
Attackers exploited a flaw in the victim contracts’ validation logic, which only checked if the caller was authorized, but failed to restrict what functions could be invoked. This allowed malicious actors to use authorized contracts to directly call sensitive functions and drain assets like vTokens. The attack targeted bots such as printMoney and was executed through a series of crafted calls exploiting poor internal permission handling.
6. Silo Exploit – $545K
On June 25, 2025, Silo Finance lost approximately $545,000 due to an exploit in a testing-phase smart contract for an unreleased leverage feature. Core protocol contracts, including vaults and markets, remained unaffected, with only DAO-owned funds lost.
The attacker exploited a vulnerability in the openLeveragePosition function of an experimental smart contract deployed for testing. This function allowed user-controlled inputs, which the attacker manipulated to drain funds. The attacker funded their wallet through Tornado Cash and executed the exploit before the contract was paused. Hypernative Labs detected the malicious code 3 minutes before execution, and Silo promptly responded by isolating the module, reassuring users that no external funds were at risk.
7. MetaPool Exploit – $400K
On June 17, 2025, Meta Pool on the Ethereum network suffered a loss of approximately $400,000 due to a vulnerability in the minting logic of its mpETH pool. The attack also involved MEV frontrunner Yoink, who replicated and executed the exploit immediately after the original attacker.
The exploit originated from Meta Pool’s failure to override or restrict the inherited mint() function from OpenZeppelin’s ERC4626Upgradeable standard. This public, non-payable function allowed users to mint mpETH without actually providing ETH, violating the protocol’s 1:1 backing invariant. The attacker first used a flash loan to drain the liquidUnstakePool of available mpETH, ensuring that the internal swap logic would be bypassed. They then invoked mint() to mint over 9700 mpETH for free and swapped part of it for ETH, securing a profit of roughly 56.35 ETH (~$142K). An MEV bot named Yoink also front-ran the exploit, taking a share of the proceeds. Meta Pool has since disabled mpETH transfers and committed to ongoing communication and governance updates.
8. Hacken Protocol Access Breach – $250K
On June 21, 2025, the Hacken bridge was exploited due to a leaked private key associated with a minting role, leading to the unauthorized minting of 900 million HAI tokens and causing approximately $250,000 in losses. The HAI token price collapsed by around 99%, and the team responded by revoking access, pausing the bridge, and committing to a token migration that excludes the attacker’s funds.
The exploit occurred after a human error during a bridge architecture update exposed a private key with minting permissions; the attacker used this to mint 900 million HAI tokens on both Ethereum and BNB Chain. They sold the tokens primarily on BNB Chain, causing a rapid price collapse due to limited liquidity. The core deployer wallet was not compromised, allowing the team to quickly halt operations, but the absence of a multisig setup left the system vulnerable to this single point of failure.
9. Anome Exploit – $120K
June 10, 2025 – DeFi project Anome on Base was exploited for approximately $120K due to a flawed token valuation mechanism that allowed massive over-borrowing.
An attacker exploited Anome by purchasing a massive amount (1e20) of Bnome tokens for just 0.2 ETH, then supplying them to contract 0x7144. Due to faulty price validation or lack of checks on the token’s true value, the attacker was able to borrow Anome USD repeatedly, draining around 44 ETH (~$120K) in value. The stolen funds were quickly funneled through Tornado Cash to obfuscate the trail.
10. Tailverse Token Exploit – $88K
June 2, 2025 – Tail Metaverse staking contracts were exploited for approximately $88K, primarily through manipulation of NFT-based reward logic. The attacker dumped inflated $tailverse tokens for USDT.
The vulnerable staking contract at 0xf633…ae8 allowed repeated reward collection using the same NFT-like token. The attacker deposited the token, claimed rewards, withdrew it, transferred it to a new wallet, and repeated the loop, effectively farming excessive tailverse tokens. These tokens were later dumped on a USDT pair, leading to ~$88K in losses. Two contracts were affected, and the main exploit address is 0xd1c58…ed76.
June 2025 added another dark page to what was already an unruly year for blockchain security. While the number of incidents itself was modest, the cost of a few high-profile compromises, particularly the Nobitex one, pumped up the total loss for the month to nearly $115 million. The ubiquity of access control flaws and continuous CeFi and smaller DeFi platform targeting attest that the Web3 ecosystem remains structurally exposed to both novel and traditional threats. Lacking a recovery recorded this month and increasing cross-chain engagement, the case for mandatory audits, enhanced on-chain permissions, and sound governance structures grows by the day.
October 2025 saw a total of $38.63 million lost across nine distinct security incidents in both centralized and decentralized platforms.
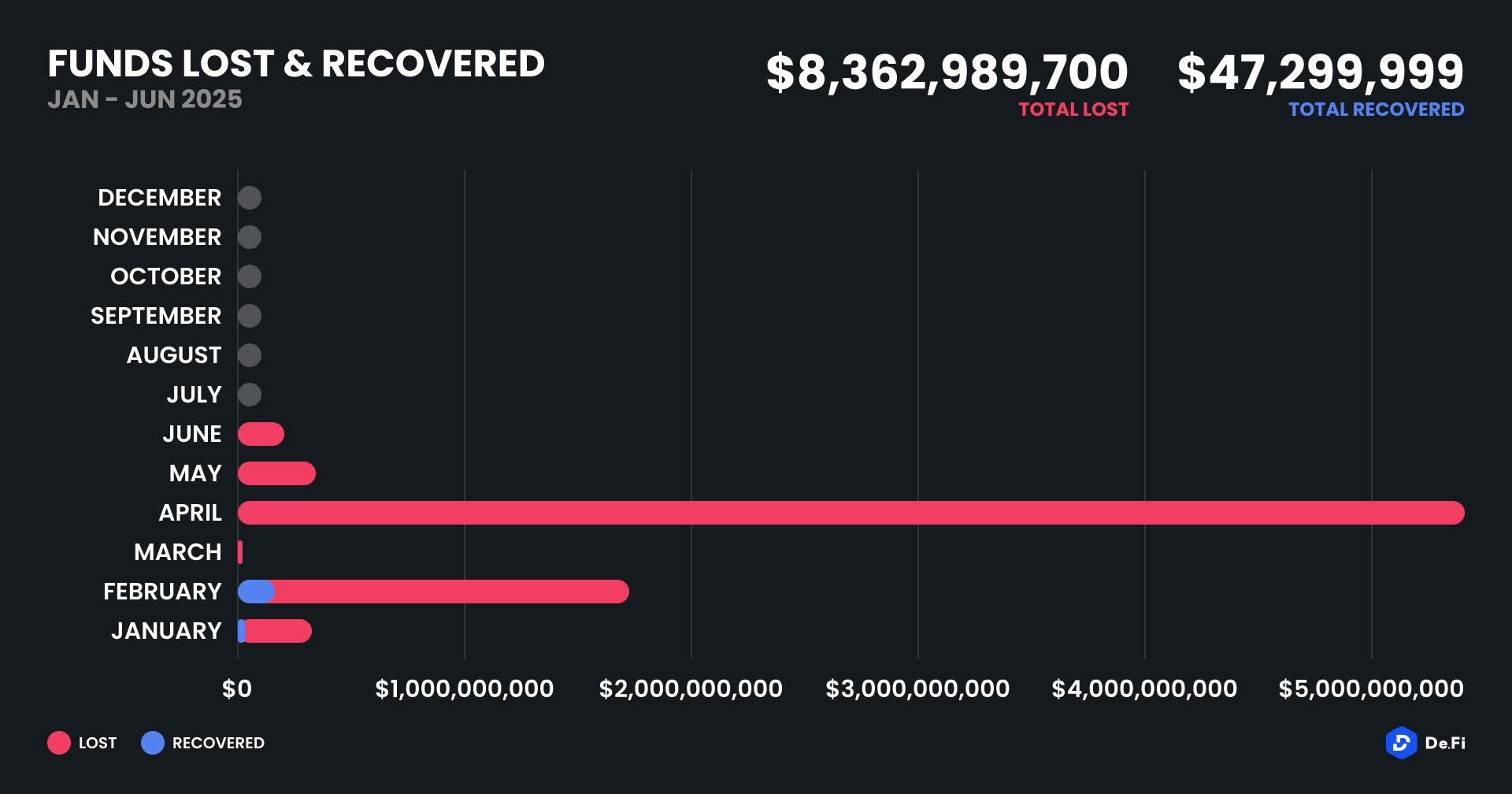
The third quarter of 2025 marked yet another turbulent period for the DeFi and wider crypto ecosystem, with $434,124,000 lost to exploits, scams, and security failures across both centralized and decentralized platforms.
June 2025 witnessed another alarming month for Web3 security, with a total of $114,768,000 lost during 11 separate attacks
May 2025 saw both DeFi and CeFi security once again under attack, with $275,953,000 lost across just 8 recorded incidents
April 2025 witnessed a large escalation in exploit volume and value, with a massive $5,919,684,000 being stolen in 10 confirmed events.
Q1 2025 marked one of the worst quarters in blockchain exploit history, with total recorded losses topping $2,052,584,700 across 37 incidents
© De.Fi. All rights reserved.