DeFi Rekt Report October 2025: $38.6 Million Lost Across 9 Exploits
October 2025 saw a total of $38.63 million lost across nine distinct security incidents in both centralized and decentralized platforms.


May 2025 saw both DeFi and CeFi security once again under attack, with $275,953,000 lost across just 8 recorded incidents. This marks the third-highest monthly loss of the year so far, surpassed only by the February Bybit breach and the April SUI ecosystem rug pulls. Alarmingly, no funds were recovered in May, despite the relative concentration of losses in a handful of large-scale attacks. The standout event was the catastrophic $260 million exploit on Cetus, a major DEX operating on the Sui blockchain, which alone accounted for over 94% of total losses.
The month’s exploits were dominated by a few large-ticket events rather than a wide dispersion of minor incidents. Cetus’ exploit on Sui was the clear black swan, with a single contract manipulation wiping out hundreds of millions in TVL. Other notable cases included the $12 million Cork exploit on Ethereum, the $2.16 million Mobius Token exit scam on BSC, and an oracle issue affecting Nitron Demex on Arbitrum. The concentration of these incidents across newer or less battle-tested ecosystems like Sui and Base reflected how security threats impact both emerging and mature chains.
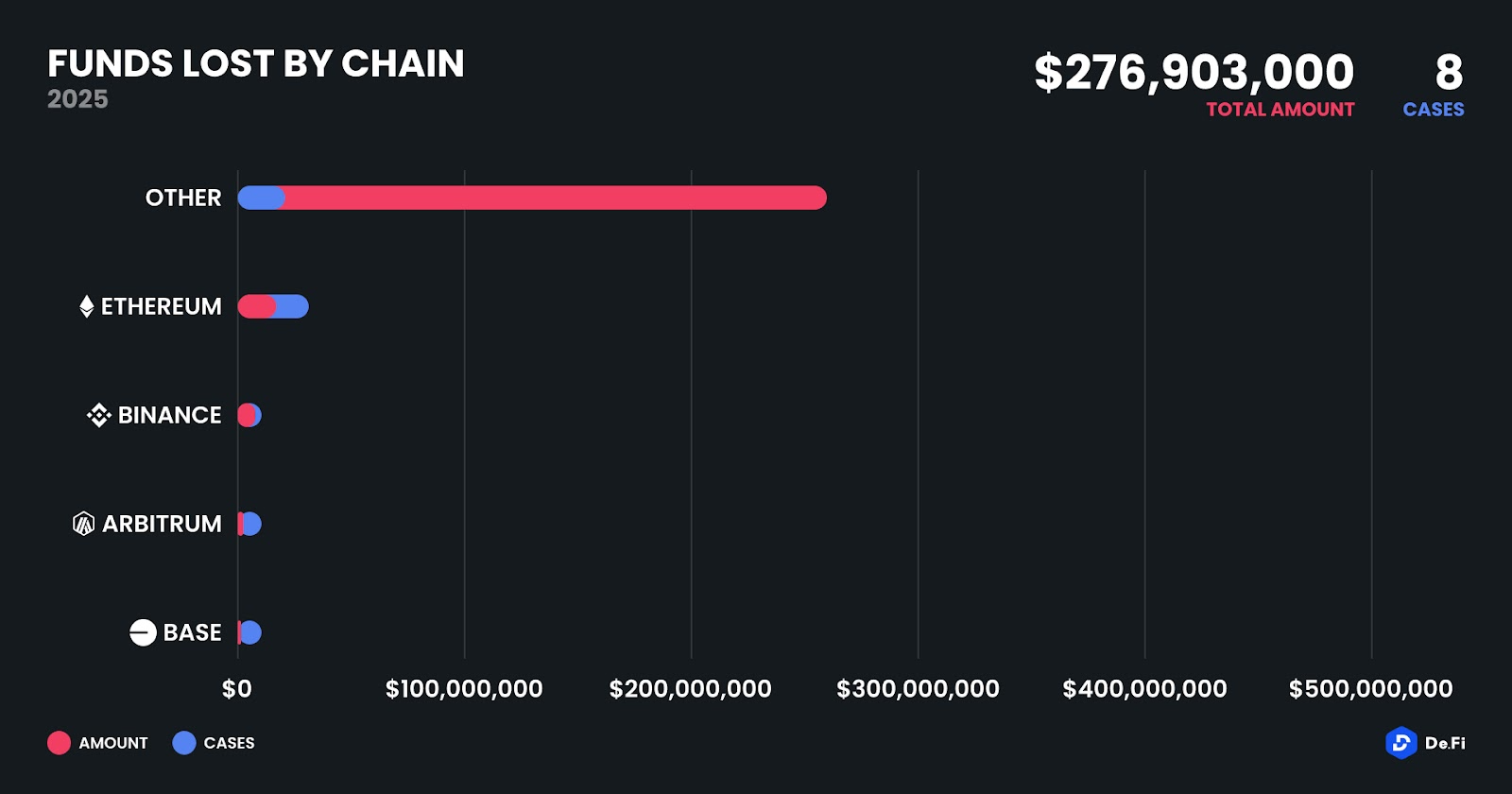
Losses in May were distributed unevenly across several chains, with non-EVM networks taking the brunt. The Sui blockchain suffered a single catastrophic loss via Cetus, resulting in $260 million gone in a matter of minutes. Ethereum followed with three incidents totaling $12.54 million, driven primarily by the Cork and Zunami attacks. Binance Chain and Arbitrum recorded one case each, while Base suffered its first major exploit of the year via Dexodus. In total, 8 incidents spanned across 5 different chains, demonstrating that the attack surface continues to expand alongside chain proliferation.
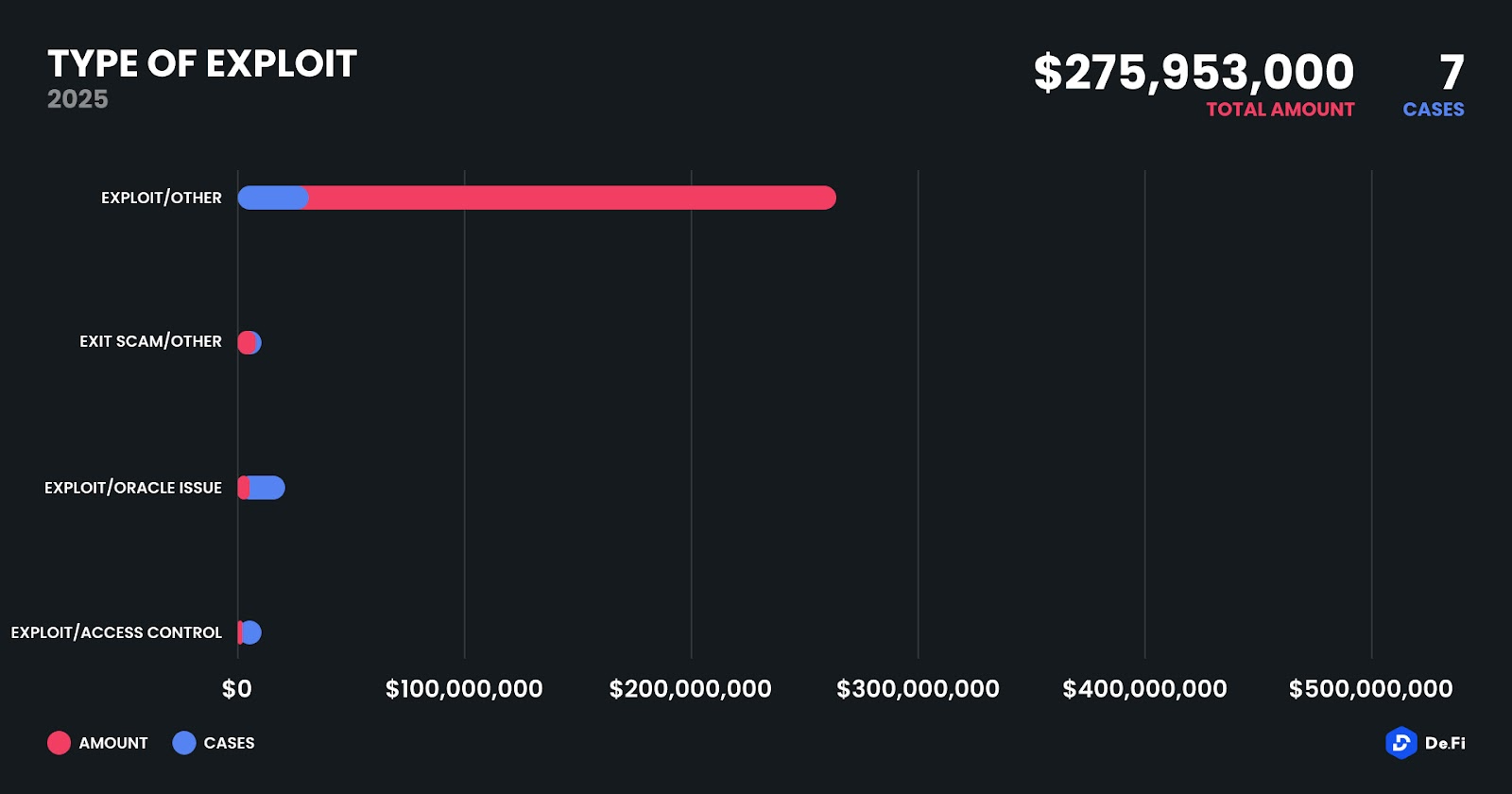
The vast majority of funds lost in May stemmed from classic smart contract exploits, accounting for over $272 million across just three cases. These included vulnerabilities in core trading logic, unchecked inputs, and improperly managed liquidity pools. Exit scams continued to appear, albeit at lower scale, with Mobius Token draining $2.16 million from users in a rug pull masquerading as a “token migration.” Oracle manipulation accounted for $1.25 million, spread across Dexodus and Nitron Demex, and one notable access control failure occurred at Zunami on Ethereum, resulting in a $500,000 breach. The persistence of fundamental security failures, especially in newer DeFi protocols, remains a key concern.
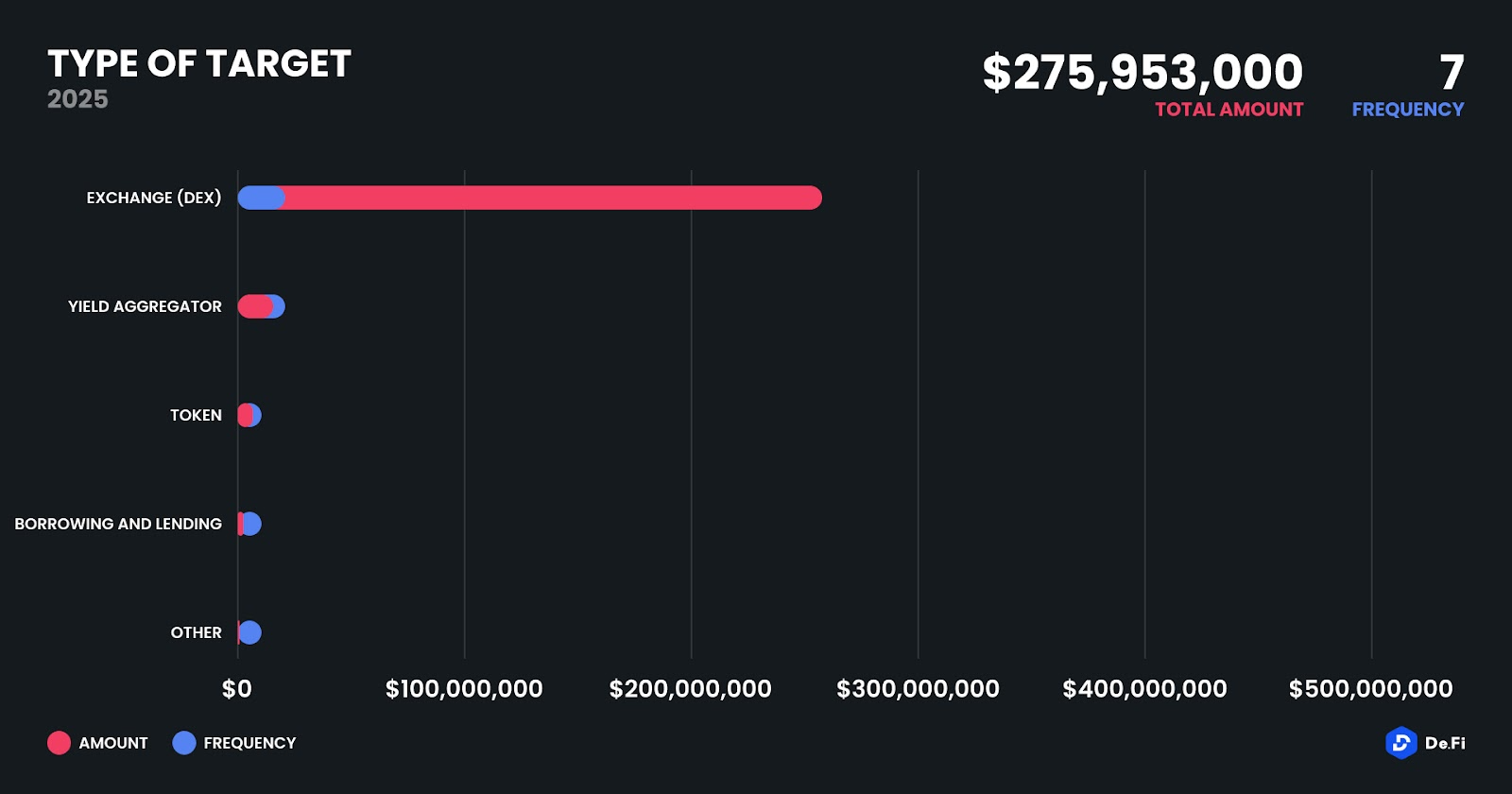
DEXs were once again the hardest hit category, with Cetus and Dexodus contributing to $260.3 million in total DEX-related losses. This underscores the inherent risk in liquidity pool-driven systems, especially in chains with immature audit ecosystems or fast-paced deployments. Yield aggregators such as Cork and Zunami lost a combined $12.5 million, driven by flawed contract upgrades and poorly implemented governance. Meanwhile, token-based projects saw a continuation of smaller-scale rug pulls, as seen with Mobius Token. Lending and borrowing protocols like Nitron Demex on Arbitrum also proved susceptible to oracle exploits, while miscellaneous low-profile projects rounded out the rest.
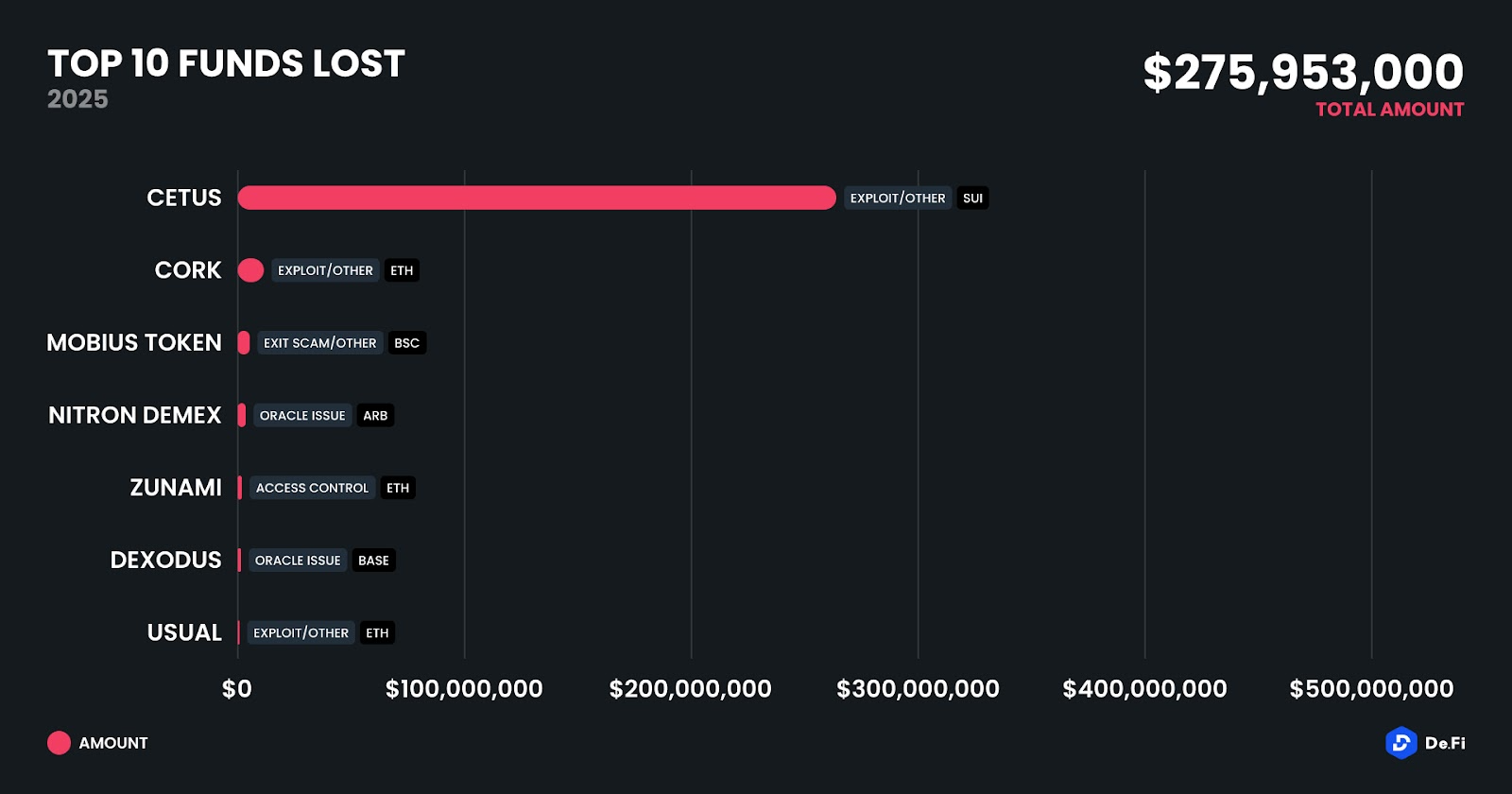
1. Cetus DEX Exploit – $260,000,000
On May 22, 2025, Cetus Protocol, the largest decentralized exchange on the Sui Network, was exploited, resulting in a loss of approximately $260 million. The attack triggered a steep crash in token prices—some falling by over 90%—and prompted the team to halt smart contract operations while investigations were underway.
The attacker exploited a flaw in Cetus’s token swap mechanism by introducing spoofed tokens and manipulating the AMM curve’s price calculations. These malicious tokens were used to artificially inflate pool reserves and trading prices, allowing the attacker to drain real assets from liquidity pools at distorted valuations. The exploit bypassed standard token validation mechanisms, indicating weaknesses in the protocol’s input verification and curve logic. The attacker’s wallet was observed holding a range of valuable tokens post-exploit, and laundering efforts were underway through various swaps and transfers.
2. Cork Yield Aggregator Exploit – $12,000,000
On May 28, 2025, Cork Protocol suffered a severe smart contract exploit resulting in the theft of approximately 3,760 wstETH (~$12 million).
The attacker exploited a vulnerability in Cork Protocol’s wstETH:weETH market, taking advantage of faulty exchange rate logic in the smart contract. According to security auditor Dedaub, the exploit was executed by manipulating the exchange rate via fake token issuance, allowing the attacker to mint or withdraw more value than should have been possible. The attack was initiated from a wallet funded by a likely third-party service provider, and the exploited funds — approximately $12M in wstETH — were immediately swapped for ETH. The malicious contract involved in the attack was deployed just prior to the exploit. Cork Protocol, which has backing from a16z and OrangeDAO, is actively investigating the incident and has paused all other markets to prevent further loss.
3. Mobius Token Exit Scam – $2,160,000
On May 11, 2025, Mobius Token (MBU) on Binance Smart Chain suffered a suspicious incident involving an unverified contract, resulting in a loss of approximately $2.16 million. The nature of the event suggests it could be an exploit or a potential rug pull. The attacker exploited an unverified contract that contained a critical miscalculation—an unintended surplus 1e18 multiplier—leading to massive inflation of MBU token supply. With only 0.001 BNB, the attacker minted over 9.7 quadrillion tokens due to faulty pricing logic. These tokens were immediately swapped for USDT, netting over $2.1 million. Since the contract was unverified and deployed just days before the incident, combined with prior activity from the same funded wallet, the event raises strong suspicion of a premeditated rug pull rather than a purely technical exploit.
4. Nitron Demex Oracle Manipulation – $950,000
On May 16, 2025, Demex’s lending platform Nitron was exploited through an oracle manipulation attack, leading to a loss of approximately $950,559. The exploit affected only the Nitron markets, while spot and perpetual trading on Demex remained unaffected.
The attacker manipulated the price oracle for the deprecated dGLP vault, which had low TVL due to prior user withdrawals. By donating fsGLP to the vault, they artificially inflated its redemption rate. This manipulated value was then propagated across Nitron markets via the Demex oracle. Using the falsely elevated price of dGLP as collateral, the attacker borrowed real assets and withdrew them for profit. The root causes included a misused audited contract not intended for oracle use, failure to implement a price cap safeguard, and the omission of zeroing out LTV and supply caps after the vault was deprecated.
5. Zunami Protocol Access Breach – $500,000
Zunami Protocol announced the attack, on Twitter on May 15, 2025. Losses totaling around $500,000 were incurred when the collateral for ZENUSD and ZENETH was exhausted. The funds were laundered via Tornado Cash.
6. Dexodus Oracle Exploit – $300,000
On May 26, 2025, Dexodus Finance was exploited for approximately $291,000 through a price manipulation attack targeting its leveraged perpetuals module. The vulnerability stemmed from accepting outdated Chainlink oracle data via the performUpkeep() function, allowing the attacker to profit from stale pricing within a single transaction.
The attacker submitted a valid but stale Chainlink price report to performUpkeep(), opening a long position at an artificially low price of ~$1,816. Within the same transaction, they closed the position using a fresh price of ~$2,520, extracting nearly $300,000. The exploit was made possible due to missing freshness checks and weak replay protection in the verify() function, which failed to ensure the recency of the price report. Since Chainlink Data Streams can remain valid for up to a month, the absence of real-time data validation in high-frequency trading scenarios proved critical. Dexodus Finance acknowledged the flaw, has paused the affected contracts, and committed to refunding users.
7. Usual Token Contract Exploit – $43,000
On May 27, 2025, Usual’s USD0++ Investment Vault was exploited through an arbitrage opportunity, leading to a $43,000 loss from the vault itself. The main protocol remained unaffected, with no user funds lost and no pause on the Usual Core Protocol.
The exploit stemmed from a capped mechanism used to unwrap USD0++ into USD0 during deposits into the investment vault. The attacker manipulated this limitation to arbitrage the conversion process, extracting $43,000 from the vault. Since only the vault’s internal funds were impacted and user balances remained untouched, the protocol confirmed that the exploit did not compromise user safety. The affected vault has been isolated and will be reenabled after mitigation steps are implemented.
May 2025 was defined by a small number of high-value exploits, with just 8 incidents resulting in a staggering $275.9 million in losses and no recovery. The overwhelming weight of the Cetus exploit on Sui skewed the data heavily, but the diversity of issues – from exit scams to oracle exploits – confirms that Web3 security remains brittle across layers and ecosystems. As new chains like Sui and Base continue to attract TVL, they also attract opportunistic attackers exploiting immature security tooling and audit ecosystems. With three consecutive months of 9-figure losses, the call for better standards, real-time threat monitoring, and coordinated recovery protocols has never been louder.
October 2025 saw a total of $38.63 million lost across nine distinct security incidents in both centralized and decentralized platforms.
The third quarter of 2025 marked yet another turbulent period for the DeFi and wider crypto ecosystem, with $434,124,000 lost to exploits, scams, and security failures across both centralized and decentralized platforms.
June 2025 witnessed another alarming month for Web3 security, with a total of $114,768,000 lost during 11 separate attacks
May 2025 saw both DeFi and CeFi security once again under attack, with $275,953,000 lost across just 8 recorded incidents
April 2025 witnessed a large escalation in exploit volume and value, with a massive $5,919,684,000 being stolen in 10 confirmed events.
Q1 2025 marked one of the worst quarters in blockchain exploit history, with total recorded losses topping $2,052,584,700 across 37 incidents
© De.Fi. All rights reserved.