DeFi Rekt Report October 2025: $38.6 Million Lost Across 9 Exploits
October 2025 saw a total of $38.63 million lost across nine distinct security incidents in both centralized and decentralized platforms.


The third quarter of 2025 marked yet another turbulent period for the DeFi and wider crypto ecosystem, with $434,124,000 lost to exploits, scams, and security failures across both centralized and decentralized platforms. This figure is a marked improvement from Q3 2024, which saw $671 million in losses, but still serves to remind us of the threats facing crypto investors at large. On a more optimistic note, $50 million was successfully recovered through white-hat interventions, legal enforcement coordination, and incident response mechanisms, a marked increase from the $12.2 million recovered in the same period last year.
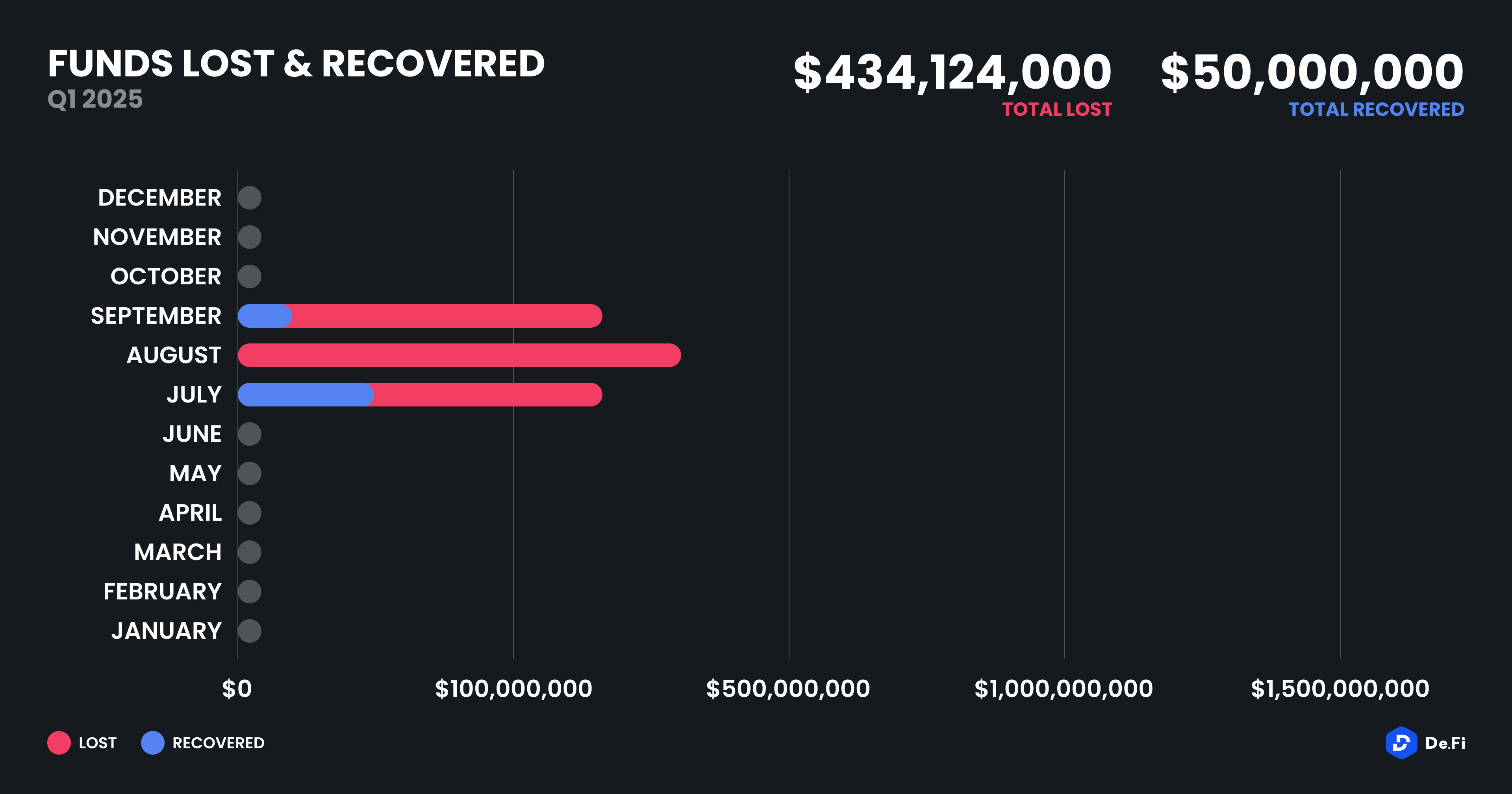
Breaking down the incidents by month, August 2025 topped the chart with $159,727,000 in stolen funds, much of which stemmed from two major access control failures affecting centralized platforms and token issuance protocols. July 2025 saw a comparable $138,045,000 in losses, but also the highest recovery volume, as $37 million was clawed back, likely due to a timely response to phishing attacks and improved KYC-linked traceability on affected CeFi platforms.
Finally, September 2025, though featuring slightly lower total losses at $136,352,000, presented a concerning decline in post-hack recoveries. No material recoveries were recorded during the month, raising concerns about persistent capability gaps among exchanges, law enforcement, and incident response teams.
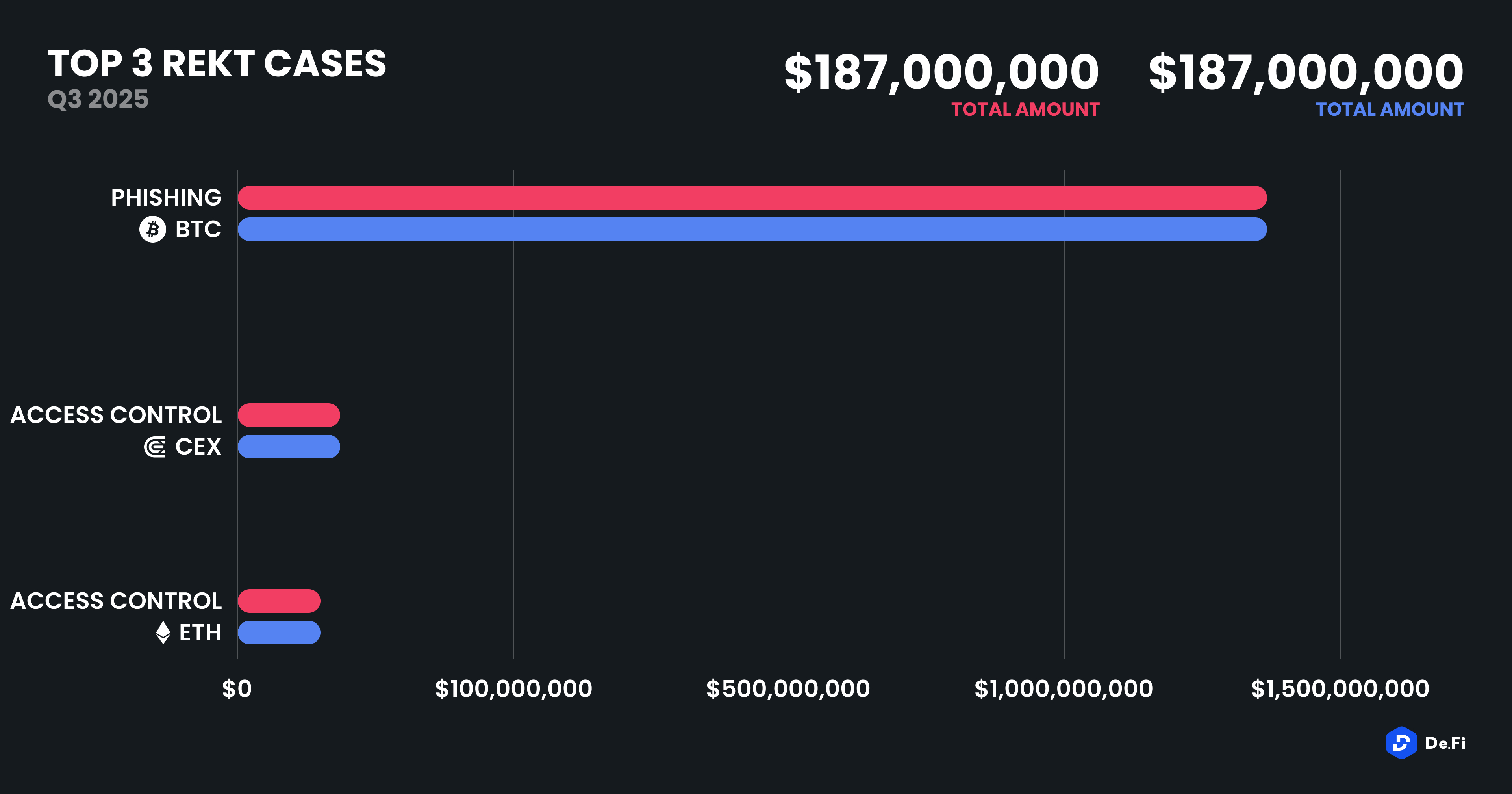
The largest exploit of Q3 was a $91 million phishing scam targeting Bitcoin holders, once again highlighting the rampant nature of social engineering tactics. In this case, the large loss was driven by high-value addresses falling prey to this attack. This was closely followed by the $48 million access control exploit of BtcTurk, a Turkish centralized exchange that had already faced prior security issues. A similarly sized access control incident affected UXLINK on Ethereum, which lost $48 million.
Other noteworthy incidents included a $44 million breach of CoinDCX, another centralized exchange with regional prominence in India, and a $42 million exploit on GMX, a derivatives DEX operating primarily on Arbitrum. The latter is particularly significant because many other perpetuals DEXes across various EVM chains are effectively forks of the original GMX v1 DApp, implying that these DEXes may also be vulnerable to this same exploit.
In total, the top 10 REKT events for Q3 2025 represented $377.9 million, accounting for circa 87% of total funds lost. This repeats the point from our previous analyses that while many smaller exploits occur, large-scale single-event breaches continue to drive industry losses.
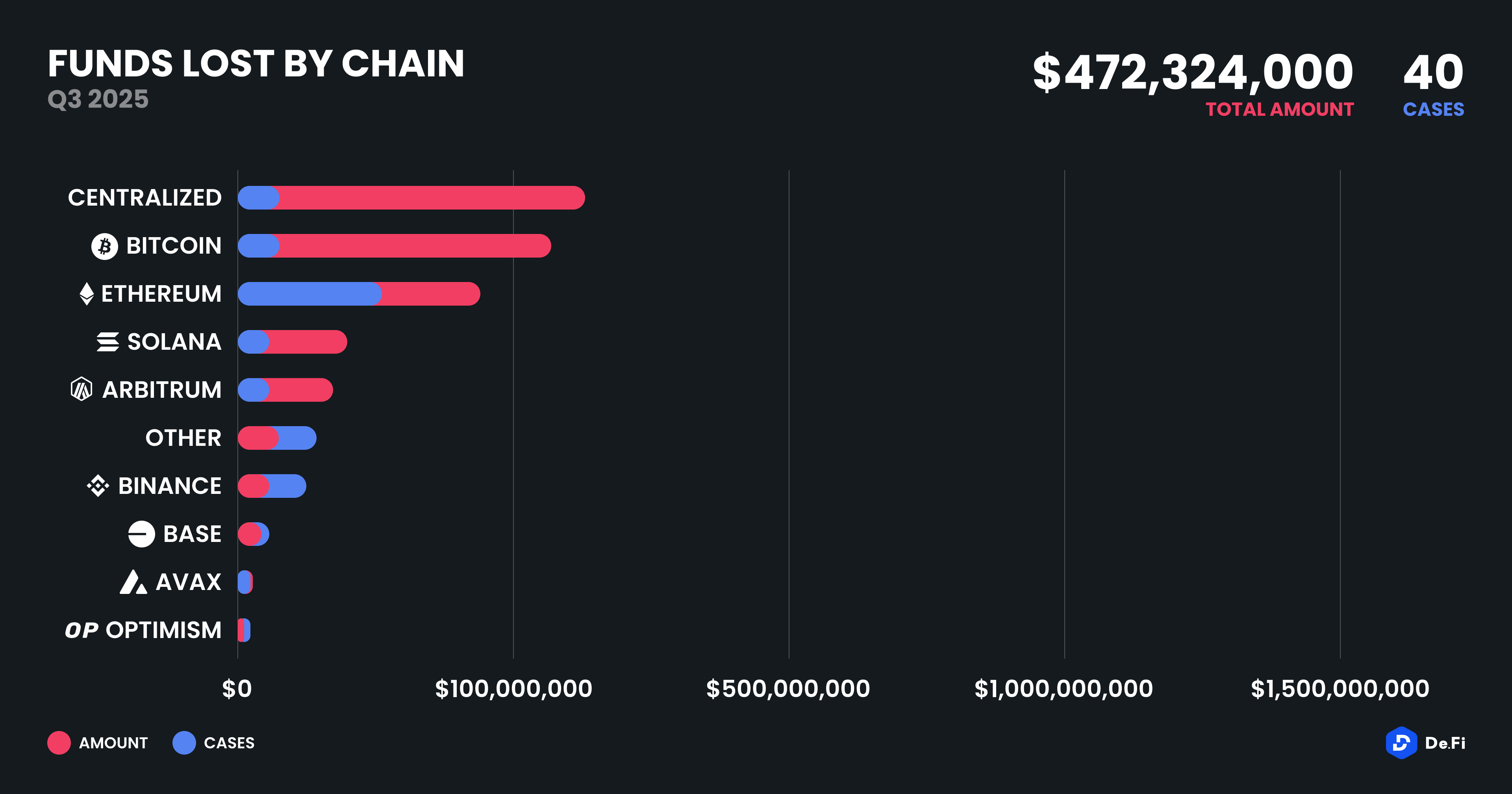
Despite improvements in smart contract auditing and security tooling, Ethereum remained the most frequently targeted chain, with 11 incidents totaling $90.3 million in losses. This is perhaps not surprising, considering that a large portion of DeFi liquidity is locked on Ethereum. However, in terms of monetary impact, Bitcoin took the lead, primarily due to phishing incidents, with total losses crossing $112 million across just three cases. This trend reflects the difficulty of securing custodial and self-custodial assets on chains that lack smart contract native tooling and permissions.
Solana experienced two high-profile losses totaling $46.15 million, confirming its vulnerability to wallet exploits and bridge logic bugs, despite improvements in validator set monitoring and tooling maturity. Arbitrum, Base, Binance Smart Chain, Optimism, Linea, and zkSync Era were all involved in at least one incident, signaling that no major ecosystem remains immune to attack, especially as newer chains ramp up TVL and active user counts without fully stress-testing their security stack.
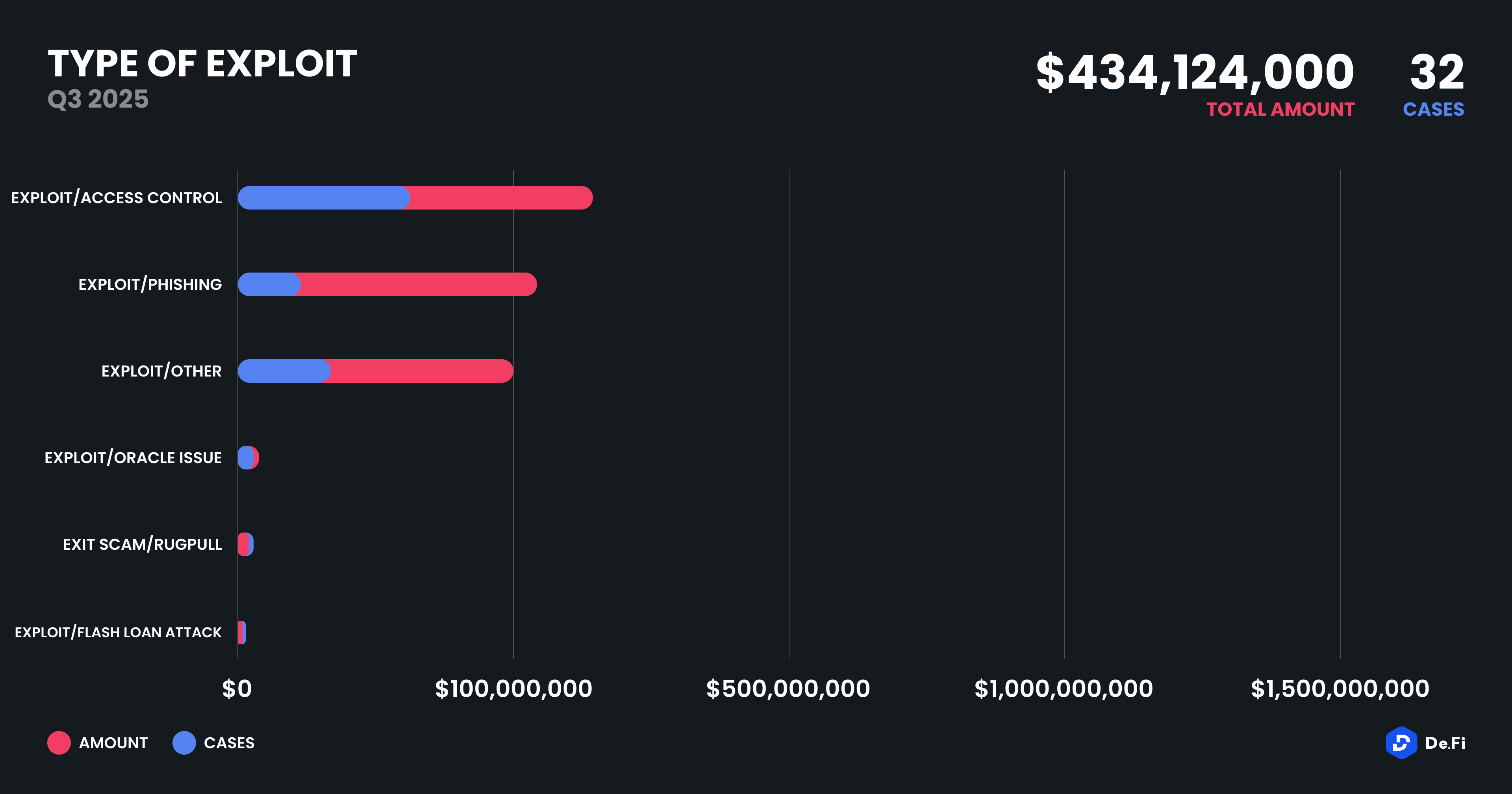
In Q3, access control vulnerabilities were responsible for $188.7 million in losses, spanning 13 incidents. These included both traditional CeFi-style admin key takeovers and DeFi permissioning failures (e.g., token contracts with upgrade or mint rights left exposed). This exploit type has remained consistently dominant across quarters, and yet many platforms continue to rely on multisig setups without robust monitoring or formal verification of governance processes.
Phishing attacks accounted for $121.8 million over five known incidents, showing that human vulnerability remains a massive attack surface. These ranged from spear-phishing via deepfakes and manipulated URLs, to Telegram impersonation schemes targeting token issuers and early-stage project founders.
Other exploit types included “Other” smart contract bugs and governance-related attacks, which together accounted for $104 million in losses. A single flash loan attack this quarter exploited a liquidity pool with insufficient slippage protection, causing $2 million in cascading losses. Meanwhile, oracle manipulation caused $9.4 million in losses, and exit scams, once more common, were limited to $8.25 million this quarter.
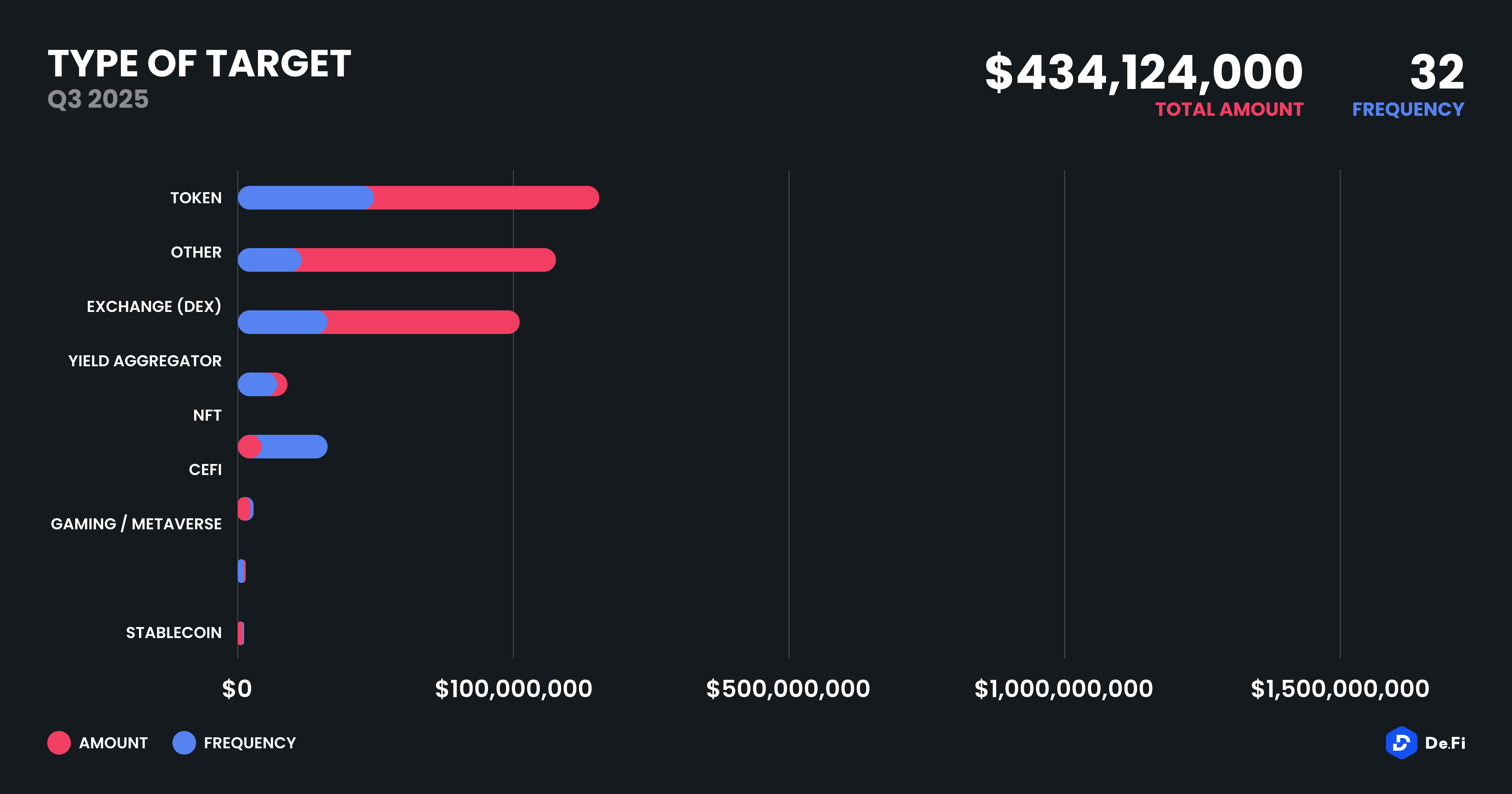
When categorizing losses by type of platform, centralized exchanges (CEXes) were the most severely affected, losing over $134 million across four major incidents. This continues a long-term trend of centralized platforms suffering from internal mismanagement, staff collusion, or external compromise, despite tighter KYC and AML regulations in many regions.
Decentralized exchanges (DEXs) were the next largest category, facing six major incidents that together accounted for $105.4 million in losses. Many of these stemmed from logic bugs or improper handling of liquidity migration events.Yield aggregators accounted for $9.73 million in losses across six separate cases, typically tied to reward emission calculation bugs or improperly gated strategy access. Lending protocols suffered $18.7 million in three cases, while bridge and NFT infrastructure projects were also attacked, albeit at lower volumes of $3.6 million and $730,000, respectively.
The total of $50 million recovered in Q3 2025, largely from incidents in July, represents a significant uptick in remediation effectiveness. Coordinated responses between white-hat researchers, centralized exchanges, chain analytics firms, and legal enforcement bodies enabled the freezing or return of funds in multiple cases. The use of on-chain negotiation tools (such as hacker bounties and partial refunds) also played a role in recovering funds post-exploit.
However, the sharp drop-off in recoveries in September, despite multiple major incidents, reveals that many projects still lack a formal incident response plan. The recovery ecosystem remains reactive and fragmented, with outcomes largely dependent on attacker behavior or the availability of KYC-linked endpoints (e.g., centralized exchange withdrawal addresses).
Looking forward, protocols and exchanges must treat security as an operational core function, not an afterthought. With cross-chain interoperability, real-world asset tokenization, and on-chain derivatives all growing rapidly, the complexity of attack surfaces is only increasing. Governance automation, role-based permissioning, and third-party security certifications may become standard industry practice in the quarters ahead, but for now, vigilance, transparency, and community trust remain the most potent defense.
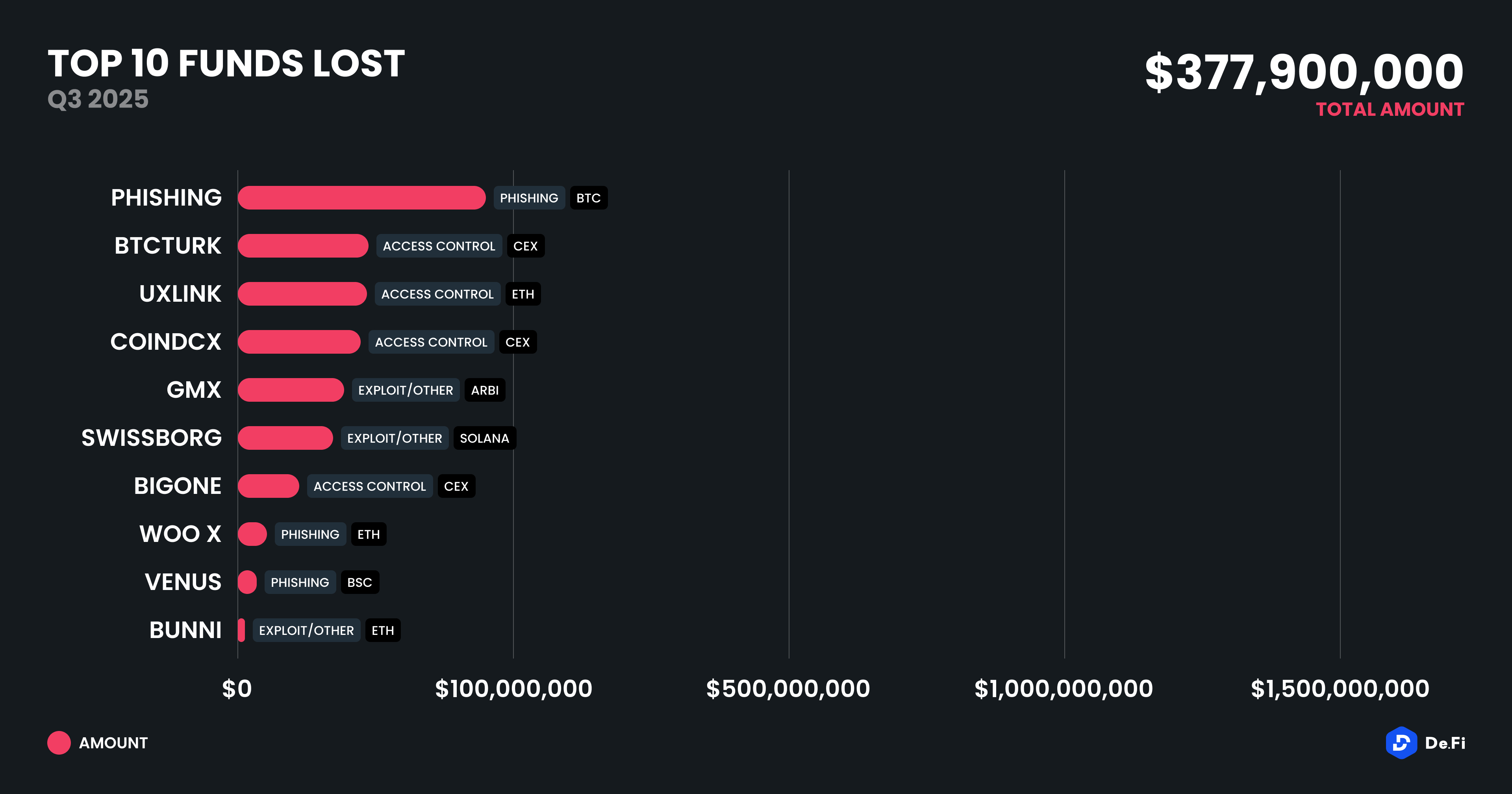
1. BTC Phishing – $91,000,000 (Phishing)
On August 19, 2025, a victim lost 783 BTC ($91 million) in a social engineering scam where threat actors impersonated exchange and hardware wallet customer support representatives. The theft occurred exactly one year after the $243 million Genesis Creditor theft, with the stolen funds beginning to be laundered through privacy-focused services including Wasabi wallet.
The attack was executed through sophisticated social engineering tactics where the perpetrators impersonated legitimate customer support personnel from both cryptocurrency exchanges and hardware wallet companies. The victim was manipulated into providing access credentials or performing actions that compromised their Bitcoin holdings, resulting in the unauthorized transfer of 783 BTC valued at approximately $91 million. Following the theft, the threat actors immediately began implementing money laundering techniques, including “peeling” transactions to break up the large sum into smaller amounts and making deposits to Wasabi wallet, a privacy-focused Bitcoin mixing service designed to obscure transaction trails. The timing of this theft is particularly notable as it occurred exactly one year after the massive $243 million Genesis Creditor theft, suggesting possible coordination or symbolic significance to the attackers.
2. BtcTurk – $48,000,000 (Access Control)
On August 14, 2025, Turkish cryptocurrency exchange BtcTurk suffered a suspected hack with reports indicating approximately $48-50 million in digital assets were stolen from their hot wallets. The exchange halted cryptocurrency deposits and withdrawals citing a “technical issue,” while trading and local currency operations remained active.
Cybersecurity firm Cyvers detected unusual activity across multiple blockchain networks including Ethereum, Avalanche, Arbitrum, Base, Optimism, Mantle, and Polygon, with stolen assets being moved to consolidation addresses and swapped for other cryptocurrencies. BtcTurk confirmed that unusual activity was detected in their hot wallets during inspections conducted on August 14, 2025, prompting them to temporarily suspend cryptocurrency deposits and withdrawals as a precautionary measure. The attacker began systematically swapping stolen assets to Ether using services like MetaMask Swaps. The exchange assured users that most assets are held in secure cold wallets and that user funds remain unaffected. BtcTurk has informed authorities and implemented additional security measures while conducting a detailed investigation. This incident marks the second major breach for BtcTurk, following a June 2024 hack that resulted in approximately $55 million in losses from unauthorized hot wallet withdrawals.
3. UXLINK – $48,000,000 (Access Control)
On September 22, 2025, UXLINK, a decentralized social project, suffered a multi-signature wallet exploit resulting in over $21.7 million in stolen assets. The attacker gained unauthorized minting rights and issued an additional 1 billion UXLINK tokens, causing the token price to plummet 70%. In an unusual twist, the original hacker later lost approximately $48 million worth of UXLINK tokens to a secondary phishing attack.
The attack began with a security breach of UXLINK’s multi-signature wallet system where the attacker used delegateCall to remove administrator privileges, called addOwnerWithThreshold to gain control, and transferred approximately $11.3 million in various assets including $4 million USDT, $500,000 USDC, 3.7 WBTC, and 25 ETH. The attacker then gained minting rights and issued 1 billion additional UXLINK tokens on Arbitrum, severely diluting the token supply. UXLINK responded by coordinating with major exchanges to freeze suspicious deposits and initiated a token swap plan while developing compensation measures for affected users. In a rare “hacker-on-hacker” crime, the original attacker subsequently fell victim to an Inferno Drainer phishing attack, losing approximately 542 million UXLINK tokens (worth about $48 million) to secondary criminals.
4. CoinDCX – $44,000,000 (Access Control)
July 19, 2025 — Indian exchange CoinDCX suffered a $44 million exploit due to a server breach targeting an internal liquidity account; user funds were not affected and operations continue normally.
The breach occurred at 4 a.m. IST on July 19 when an attacker gained unauthorized access to a CoinDCX liquidity provisioning account used on a partner exchange. The company attributed the incident to a sophisticated server-level compromise, not a smart contract flaw. Funds were routed through Tornado Cash and bridged between Solana and Ethereum before being dispersed across several wallets. The attacker initially masked their activity with a small Tornado Cash transfer, later conducting larger outflows. Although CoinDCX delayed disclosure by ~17 hours to conduct internal analysis, it has since confirmed full reimbursement from its treasury and is collaborating with CERT-In and blockchain forensics firms. A Recovery Bounty Program is being launched, and affected wallets were identified by ZachXBT and Arkham.
5. GMX – $42,000,000 (Exploit/Other)
On July 9, 2025, GMX v1 was exploited for approximately $42 million due to a vulnerability that allowed a malicious contract to manipulate internal accounting and withdraw more funds than it should have. The attack affected the GLP pool on Arbitrum; other GMX deployments were not impacted. GMX has paused relevant operations and offered a bounty for the return of funds.
The attacker abused PositionManager.executeDecreaseOrder() by using a smart contract as the _account parameter, which triggered ETH refunds with no gas limit, enabling reentrancy. Within the callback, the attacker opened large short positions, causing getAum() in GlpManager.sol to register unrealized losses and inflate the protocol’s Assets Under Management (AUM). This inflated AUM was then used to redeem GLP tokens at an overvalued rate, draining ETH, USDC, and WBTC from the vault. This loop was executed multiple times, resulting in ~$42M in total losses. The GMX team confirmed the issue was limited to v1’s GLP vault on Arbitrum, paused related functions, and initiated a bounty program for fund recovery.
6. SwissBorg – $41,500,000 (Exploit/Other)
On September 8, 2025, Swiss crypto platform SwissBorg lost approximately $41.5 million worth of Solana (SOL) tokens when hackers compromised partner API provider Kiln, affecting their SOL Earn program. Around 193,000 SOL tokens were stolen, impacting less than 1% of users, with SwissBorg immediately allocating its SOL treasury to cover user losses and maintain normal operations.
The breach originated from a compromised API at Kiln, a third-party staking infrastructure provider used by SwissBorg’s SOL Earn program. The attackers exploited vulnerabilities in Kiln’s systems to gain unauthorized access and move approximately 193,000 SOL tokens without triggering internal security alarms at SwissBorg. Since Kiln operates as a backend service provider, the malicious activity went undetected initially as it appeared to be legitimate staking operations. SwissBorg’s core systems remained secure throughout the incident, with the vulnerability existing solely within the third-party integration. The platform responded rapidly by allocating its own SOL treasury holdings to fully reimburse affected users, emphasizing that the company’s strong financial health allows it to absorb the loss without impacting other services. SwissBorg has engaged forensic experts, white-hat hackers, and coordinated with exchanges to freeze suspicious transactions while investigating fund recovery options.
7. BigONE – $28,000,000 (Access Control)
On July 16, 2025, BigONE exchange suffered a security incident involving unauthorized access to their hot wallet, resulting in approximately $28 million in stolen cryptocurrency across multiple blockchains. The exchange confirmed that all user assets remain safe and that BigONE will fully bear all losses from the incident.
The attacker gained unauthorized access to BigONE’s hot wallet infrastructure and drained funds across four major blockchains. The distribution of stolen assets includes $14 million in Bitcoin, $7 million in various cryptocurrencies on Ethereum and BNB Chain (with funds consolidated via cross-chain bridge to Ethereum), $7 million in TRX on Tron, and $500,000 in SOL on Solana. The attack appears to be a traditional hot wallet compromise rather than a smart contract exploit, with the attacker systematically draining funds from multiple blockchain networks. BigONE has temporarily suspended trading and deposits, with withdrawals to resume after security upgrades are implemented.
8. WOO X – $14,000,000 (Phishing)
On July 24, 2025, crypto trading platform WOO X experienced a cybersecurity breach affecting 9 user accounts, resulting in approximately $14 million in unauthorized withdrawals. The incident was contained within hours, and WOO X committed to fully covering all losses while temporarily pausing withdrawal services for additional security measures.
The exploit originated from a targeted phishing attack that compromised a team member’s device, allowing the attacker to gain access to WOO X’s development environment. Despite multiple security measures limiting access, the exploiter had sufficient time to coordinate a series of unauthorized withdrawals from the affected user accounts. The attack began at 13:50 UTC+8 with the first withdrawal request, with subsequent requests coming in gradually until the exploit was discovered and halted at 15:40 UTC+8. The incident was quickly contained, with many withdrawal attempts blocked by the platform’s security systems. WOO X completed a full forensic review and restored all affected account balances from their company treasury within 24-48 hours, confirming that no WOO tokens were stolen or sold during the compensation process.
9. Venus – $13,000,000 (Phishing)
On September 2, 2025, a Venus Protocol user fell victim to a phishing attack involving a malicious Zoom client, losing approximately $13 million after signing a transaction that granted the attacker delegate approval. Venus Protocol paused operations within 20 minutes of detection and successfully recovered all stolen funds within 13 hours through a coordinated liquidation strategy.
The attack began when the victim was compromised through a malicious Zoom client that gave attackers privileges on their machine. The attackers exploited this access to trick the victim into signing a phishing transaction that approved the attacker as a valid Venus delegate, allowing them to borrow and redeem on the victim’s behalf. The attacker executed a complex multi-step exploit: sourcing 285.72 BTCB via flash loan, repaying the victim’s 306.89 BTCB debt, transferring approximately $13M in deposits (19.826M USDT, 3,744 wBETH, 311,571 FDUSD, ~15k USDC, and ETH) to their contract, borrowing $7.14M USDC against the victim’s remaining BNB collateral, and repaying the flash loan with stolen assets. Venus Protocol responded rapidly by pausing core actions within 20 minutes, conducting thorough security reviews, and implementing a recovery plan through community governance. The team executed a coordinated liquidation strategy that seized 100% of the attacker’s collateral, transferred stolen assets to a receiver wallet, and cleared the attacker’s debt while transferring it to the receiver, successfully recovering all funds.
10. Bunni – $8,400,000 (Exploit/Other)
On September 2, 2025, Bunni DEX, a decentralized exchange built on Uniswap v4, suffered a multi-chain exploit that drained approximately $8.4 million in cryptocurrency. The attack targeted the BunniHub contract system with $2.3 million stole
The attacker exploited vulnerabilities in Bunni’s custom Liquidity Distribution Function (LDF), which replaces Uniswap’s standard logic to optimize returns for liquidity providers. By executing trades of very specific sizes, the exploiter manipulated the LDF curve and triggered faulty rebalancing calculations within the protocol’s adaptive mechanisms. This caused the system to miscalculate liquidity provider share ownership, creating opportunities for gradual fund drainage. The exploit specifically targeted how Bunni handles liquidity rebalancing across price ranges on its Uniswap v4-based infrastructure using the “hooks” feature. The attack occurred in two phases: an earlier exploit on Unichain network and a subsequent attack on Ethereum’s mainnet targeting the BunniHub contract. Bunni’s team immediately suspended all contract operations and urged users to withdraw funds while investigations continue.
October 2025 saw a total of $38.63 million lost across nine distinct security incidents in both centralized and decentralized platforms.
The third quarter of 2025 marked yet another turbulent period for the DeFi and wider crypto ecosystem, with $434,124,000 lost to exploits, scams, and security failures across both centralized and decentralized platforms.
June 2025 witnessed another alarming month for Web3 security, with a total of $114,768,000 lost during 11 separate attacks
May 2025 saw both DeFi and CeFi security once again under attack, with $275,953,000 lost across just 8 recorded incidents
April 2025 witnessed a large escalation in exploit volume and value, with a massive $5,919,684,000 being stolen in 10 confirmed events.
Q1 2025 marked one of the worst quarters in blockchain exploit history, with total recorded losses topping $2,052,584,700 across 37 incidents
© De.Fi. All rights reserved.