DeFi Rekt Report October 2025: $38.6 Million Lost Across 9 Exploits
October 2025 saw a total of $38.63 million lost across nine distinct security incidents in both centralized and decentralized platforms.


The year 2025 started with an unfortunate reminder that Web3 weaknesses are still pervasive and widespread. $62,495,200 was lost during January in 11 reported cases with no funds recovered; a continuation of the concerning trend seen in Q4 2024. While the headline figure is moderate by comparison to the record-breaking raids of previous months, the statistics reveal a shifting threat landscape affecting both DeFi and CeFi platforms across centralized exchanges, GameFi protocols and token projects.
The biggest loss for the month came from Phemex, a centralized exchange, which saw an astonishing $37 million withdrawn from users in the Ethereum Classic (ETC), Binance Smart Chain (BSC) and Tron blockchains. FortuneWheel, a BSC-based GameFi/metaverse project, lost $21 million, once again the fallibility of token-based ecosystems masquerading as entertainment products. While less serious in scope the remaining incidents demonstrated the prevalence of ongoing contract defects, access control issues and rug pulls.
January was characterized by a mix of CeFi breaches and lower-profile DeFi exploits, with incidents fairly distributed across ecosystems. The Phemex breach not only dominated in value lost but also drew attention back to the importance of centralized custodial security especially when involving multiple chains. This was closely followed by FortuneWheel, whose loss appeared to stem from flawed tokenomics and poor access control a hallmark of several GameFi rug pulls from 2024.
Among the other incidents, Moby Trade suffered a $2.5 million exploit on Arbitrum, while Orange Finance on Ethereum lost $840,000. Minor but telling breaches occurred on Solana, BSC and even among NFT projects like The Idols NFT. The dispersion of incidents across chains reinforces the reality that attackers are chain-agnostic, willing to exploit any weakness across any ecosystem.
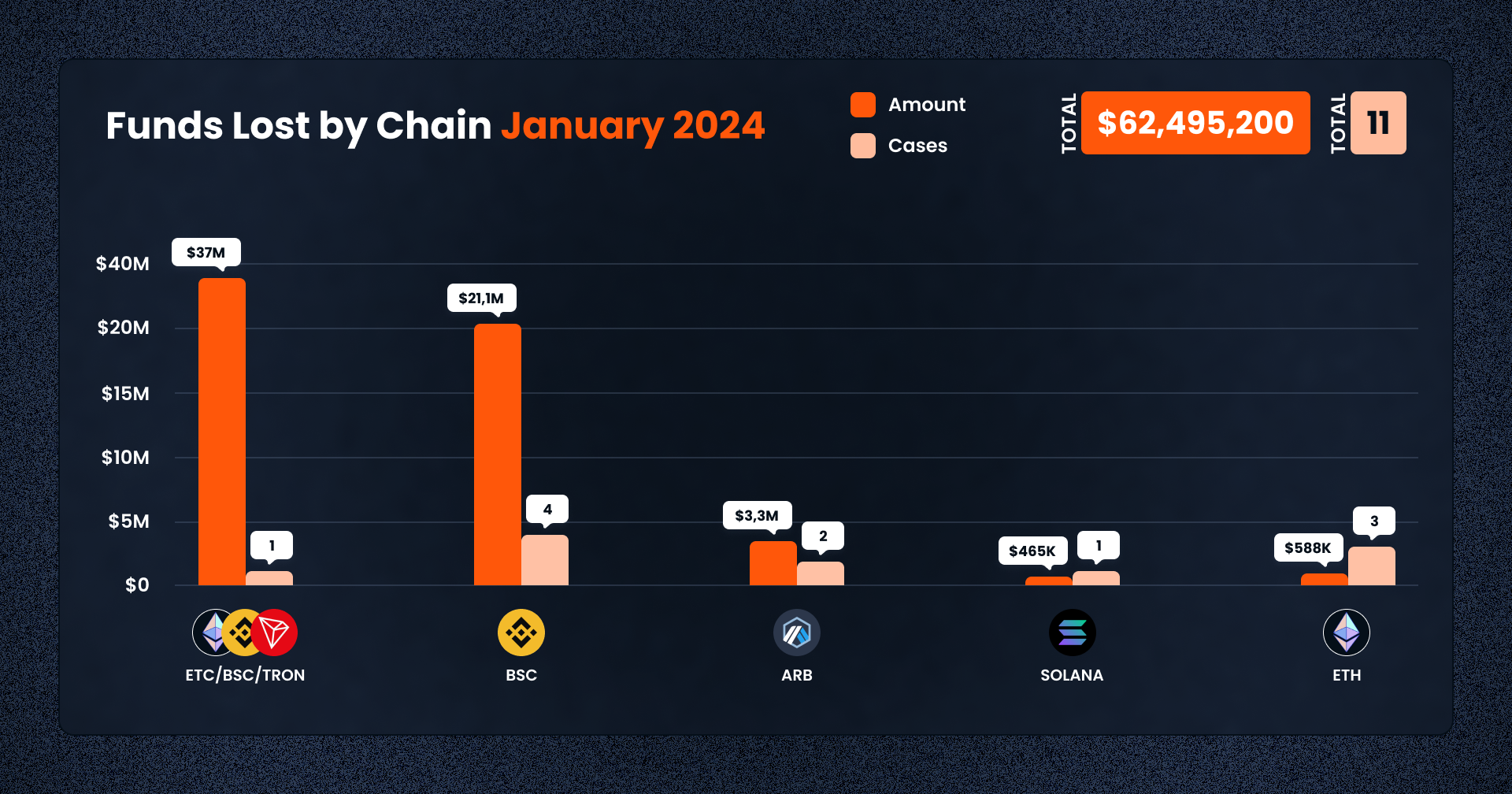
January’s losses were concentrated in non-EVM and cross-chain activity, but traditional smart contract platforms also remained vulnerable. The largest impact occurred across ETC, BSC and TRON, owing to the Phemex breach amounting to a combined $37 million. BSC additionally took another hit from FortuneWheel, raising its monthly total to over $58 million.
Elsewhere, Arbitrum reported losses from Moby Trade ($2.5M) and Ethereum hosted several small-scale breaches totaling under $1 million, including Orange Finance and The Idols NFT. Solana recorded a $465,000 rug pull from a fake Layer token, while Base and Blast chains
experienced early-year attacks, demonstrating that even newer, optimistic rollups are not immune.
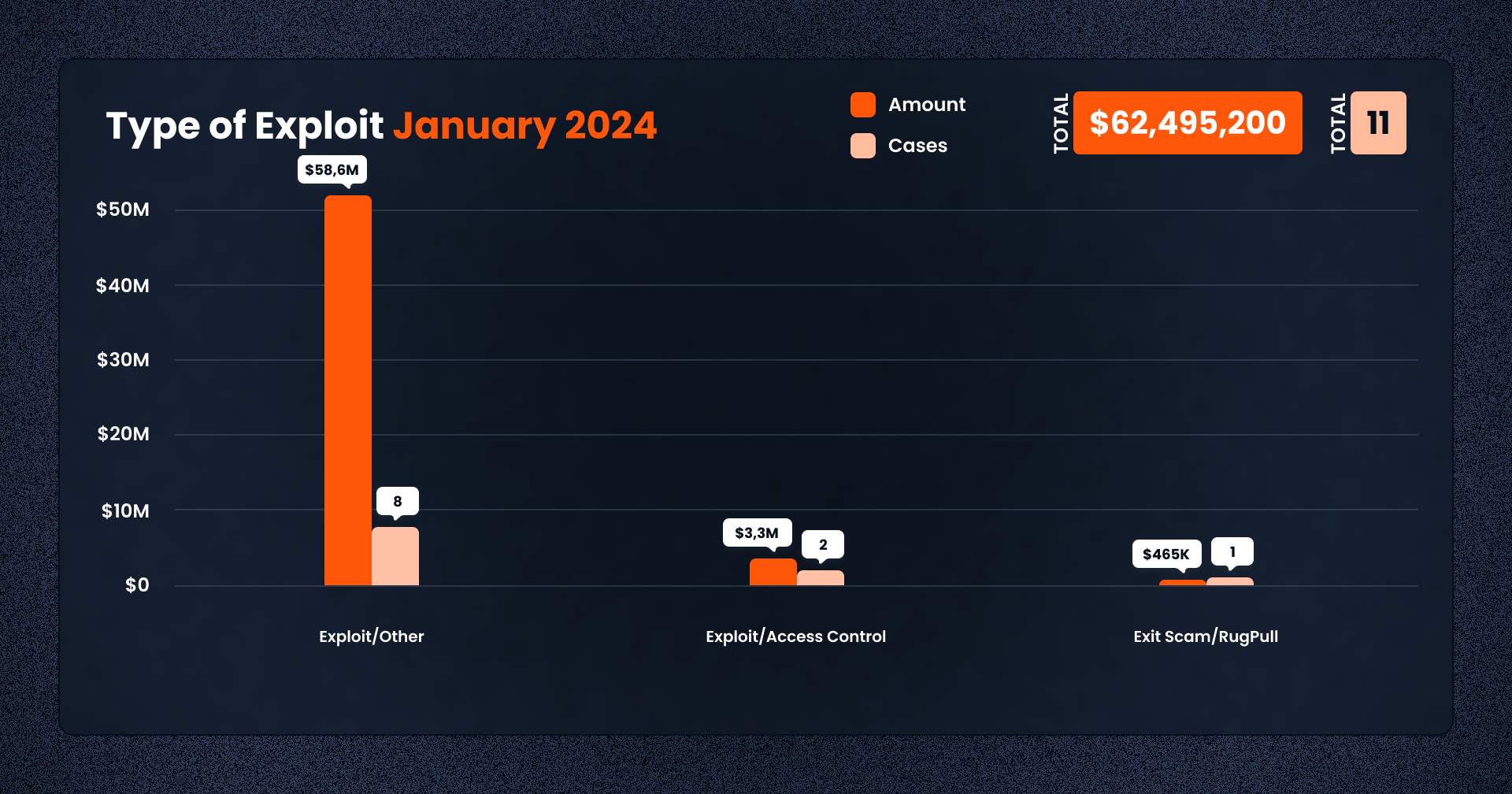
Out of the 11 recorded cases, 8 incidents were classic exploits exploiting smart contract vulnerabilities such as unchecked inputs, faulty logic, or liquidity pool mismanagement. These affected both DeFi and GameFi platforms, including Moby Trade, FortuneWheel and Orange Finance.
Two additional cases were categorized as access control failures, involving weak administrative privileges that allowed attackers to drain funds or mint illegitimate tokens. One rug pull was recorded, namely Fake Layer Token on Solana, reaffirming the trend of opportunistic scams targeting retail participants via airdrops and social engineering.
This spread of attack types underscores that, despite growing awareness, basic operational and smart contract vulnerabilities continue to plague both emerging and mature protocols alike.
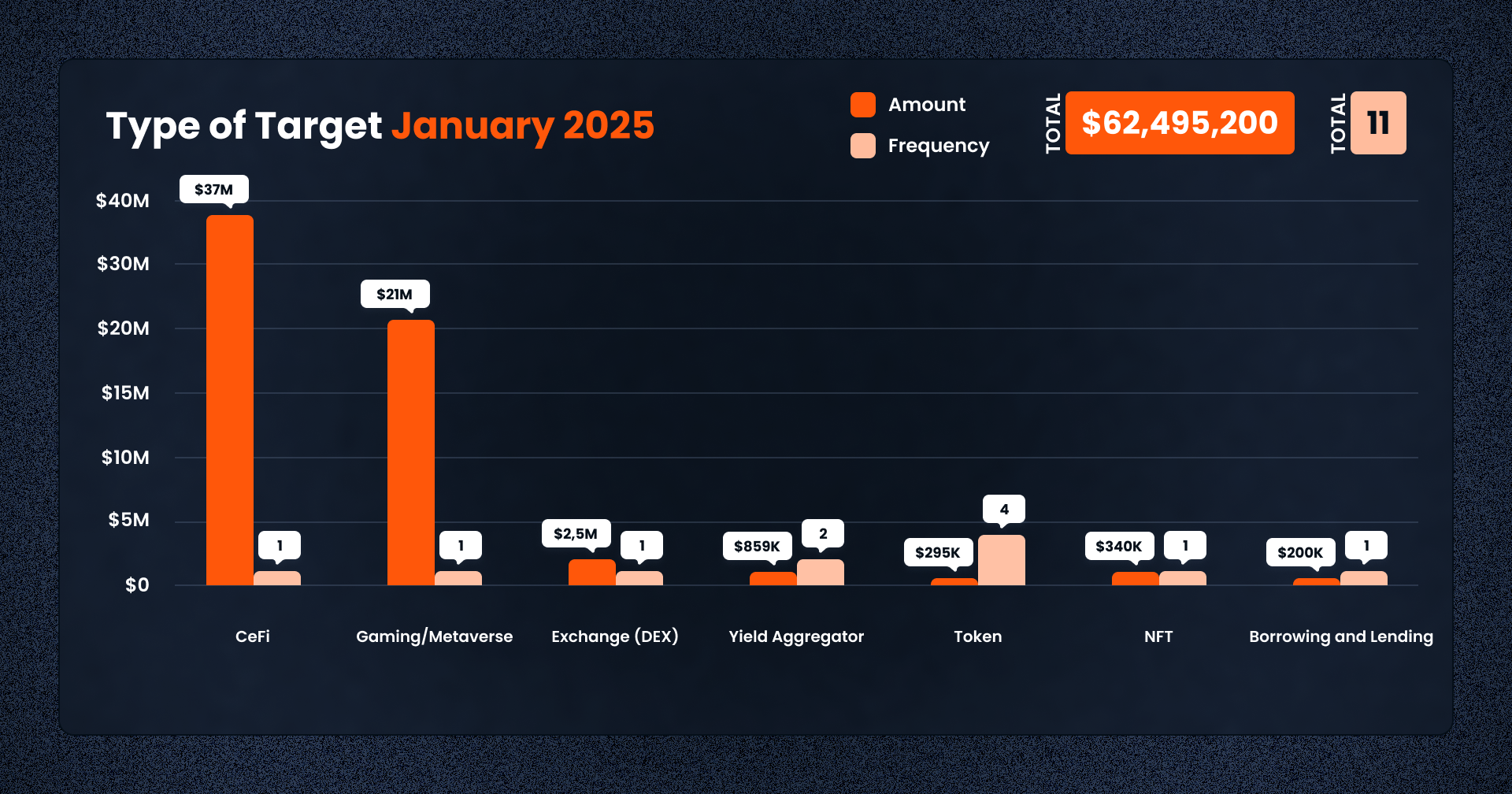
In January, CeFi platforms represented the largest share of value lost, driven solely by the Phemex incident. This is a significant development as previous months were dominated by decentralized exploits. The return of centralized breaches highlights the need for consistent custodial audits and transparency even in semi-regulated environments.
Token-based projects were the most frequently targeted category, with 4 out of 11 incidents falling into this group. These typically involved price manipulation, fake token deployments, or weak multisig governance. GameFi and Yield Aggregators followed with FortuneWheel and Orange Finance, respectively. NFT-related platforms like The Idols NFT also experienced minor breaches, reflecting the ongoing risk in the NFT sub-sector, particularly among abandoned or community-led projects.
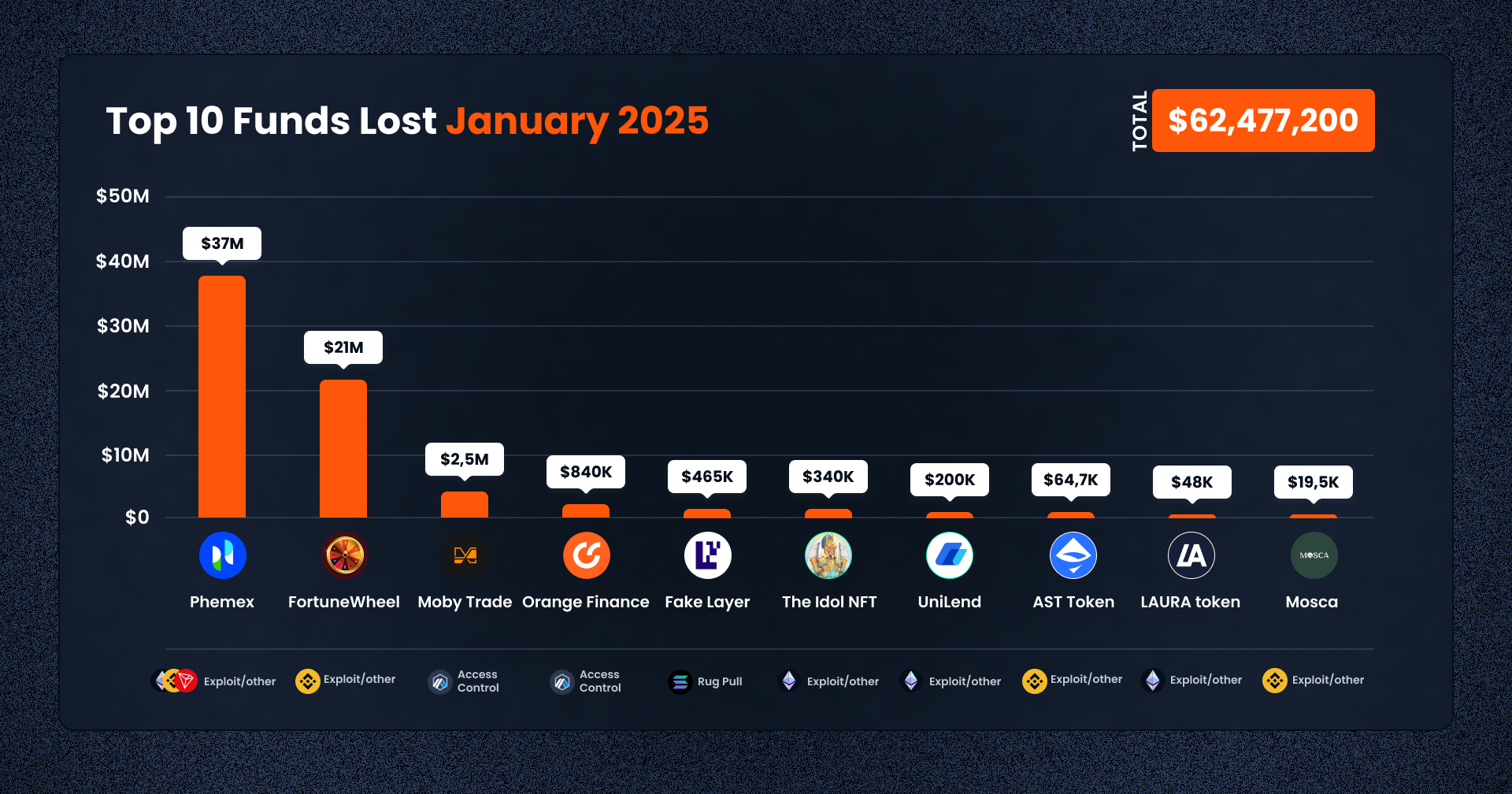
1. Phemex CEX Breach – $37,000,000
On January 23, 2025, Phemex crypto exchange detected nearly $30 million in suspicious outflows from its hot wallets, prompting the exchange to halt withdrawals and launch a security inspection. Subsequent investigations revealed additional breaches across Bitcoin and Tron networks, bringing the estimated total loss to $37 million.
The exploit targeted Phemex’s hot wallets across multiple blockchains, including Ethereum, BNB Chain, Polygon, Arbitrum, Base, and Optimism. Blockchain security firm Cyvers identified 125 suspicious transactions involving digital assets such as stablecoins and tokens, which were swiftly swapped to Ethereum to bypass freezing measures. These funds are suspected to have been laundered through mixing services like Tornado Cash. Despite the breach, Phemex confirmed that its cold wallets remain secure. In response, the exchange suspended withdrawals, kept trading services operational, and announced plans to bolster wallet security while devising a compensation strategy for affected users.
2. FortuneWheel GameFi Exploit – $21,000,000
On January 10, 2025, the FortuneWheel smart contract on Binance Smart Chain (BSC) was exploited due to a lack of access control in its swapProfitFees function. This vulnerability allowed an attacker to manipulate token prices and drain nearly $21,000 USD.
The core issue lay in the swapProfitFees function, which was designed to facilitate token swaps through PancakeSwap. However, the function lacked proper access control, allowing anyone to invoke it. The attacker exploited this flaw by first swapping a large amount of WBNB for LINK to manipulate the pool’s price. They then called the vulnerable function to swap LINK back to WBNB, profiting from the skewed pricing. This sequence of operations enabled the attacker to extract funds from the contract and ultimately caused significant financial losses.
3. Moby Trade Exploit (Arbitrum) – $2,500,000
On January 8, 2025, Moby Trade suffered a $2.5 million hack on the Arbitrum network due to a compromised private key, which allowed an attacker to upgrade the protocol’s smart contract and execute unauthorized withdrawals. However, white hat hacker Tony Ke exploited a flaw in the attacker’s contract and successfully recovered $1.5 million, reducing total losses to $1 million.
The attack stemmed from a leaked private key controlling Moby Trade’s proxy contract, enabling the attacker to modify the smart contract and use the emergencyWithdrawERC20 function to steal USDC, WETH, and WBTC. The attacker swapped the stolen funds into ETH and transferred them to external addresses. However, Tony Ke, an MEV researcher, identified an oversight in the attacker’s contract—a missing access control mechanism on the upgrade function. Using this vulnerability, Ke executed a counter-exploit to retrieve $1.5 million in USDC, which was returned to the protocol. Unfortunately, the remaining $1 million in WETH and WBTC could not be recovered in time. In response, Moby Trade suspended operations and assured users of compensation while investigating the breach.
4. Orange Finance Exploit (Ethereum) – $840,000
On January 8, 2025, Orange Finance lost approximately $0.84 million when an attacker gained control of the project’s admin key, upgraded its contracts, and diverted funds to their own wallet.
By compromising the admin key, the attacker obtained full privileges over the Orange Finance smart contracts. Using these privileges, they deployed an upgraded contract version that allowed them to siphon user funds from multiple vaults (including the Stryke vault and a now-closed Stable vault) into their own address. As soon as the exploit was discovered, Orange Finance warned users that the compromised contracts were no longer valid and advised them to revoke all approvals related to the platform.
5. Fake Layer Token Rug Pull (Solana) – $465,000
On January 21, 2025, a fake SOLAYER token crashed to nearly zero within three hours after a community alert was raised. Scammer’s profit could be estimated as 1,938 WSOL (~$465,000).
The attacker leveraged a fake SOLAYER contract (LAYERruDbdbxZTT4cfFZPRLEoG4cGwn8HpwpgTToWDg) to mislead investors into purchasing worthless tokens. After artificially inflating the token’s perceived value, the attacker made a single significant “rug transaction,” liquidating 17 trillion of these fake tokens in exchange for nearly 2,000 WSOL. Once the attacker’s large sell order cleared, the token’s price plummeted by almost 100% in a matter of hours.
6. The Idols NFT Breach (Ethereum) – $150,000
On January 14, 2025, The Idols NFT (@TheIdolsNFT) on Ethereum lost around $340,000 in stETH.
The vulnerability stemmed from a self-transfer scenario where _beforeTokenTransfer triggered _claimEthRewards(_from) and then _claimEthRewards(_to), both referencing the same address. When the sender’s NFT balance was just one, their reward snapshot was deleted, resetting the record of claimed rewards. As a result, the attacker’s next reward calculation considered an unclaimed snapshot (treated as zero), repeatedly granting the full stETH share all over again. By performing multiple self-transfers in a row, the attacker continually reset their reward snapshot, ultimately siphoning off roughly $340,000 worth of stETH.
7. UniLend (Еthereum) – $200,000
On January 13, 2025, UniLend V2 (@UniLend_Finance) on Ethereum was hacked for approximately 61 stETH (~$200K).
The attacker exploited UniLend V2’s flawed sequence in redeemUnderlying, where LP tokens were burned and collateral was transferred before the pool’s token balances were updated. By depositing a large amount of USDC, the attacker secured an artificially high “lendBalance” calculation due to outdated health factor checks and rounding issues in getShareValue. Consequently, they withdrew their deposited USDC while retaining stETH collateral, netting approximately 61 stETH (~$200K) in the process.
8. AST Token Exploit (BSC) – $64,700
On January 21, 2025, the AST token on the Binance Smart Chain (BSC) was exploited, resulting in a loss of approximately $64,700 in USDT.
The exploit targeted a vulnerability in the AST token’s _transfer function during liquidity removal scenarios on PancakeSwap. When liquidity was removed, the logic incorrectly reduced the pair’s AST balance twice, creating an abnormally low reserve. This imbalance allowed the attacker to manipulate the automated market maker’s pricing formula, enabling them to swap a small amount of AST for a disproportionately large amount of USDT. The attacker repeatedly triggered this scenario by transferring small LP tokens to initiate liquidity removal, ultimately draining approximately $64.7K USDT, which was then funneled through Tornado Cash.
9. LAURA token Exploit (Ethereum) – $48,000
On Jan 8, 2025, the LAURA token contract was exploited for around $48,000 due to a flawed removeLiquidityWhenKIncreases function.
The hacker first swapped significant WETH for LAURA and contributed LAURA and WETH liquidity to the Uniswap pool, raising the constant product (x * y = k). They then invoked the contract’s removeLiquidityWhenKIncreases() function, which failed to correctly handle the heightened K and thus allowed the attacker to remove more tokens than they deposited. Finally, the attacker traded back into WETH once the pool was misaligned, walking away with a net profit of approximately $48,000.
10. Mosca Token Exploit (BSC) – $19,500
On January 8, 2025, the Mosca smart contract on Binance Smart Chain was exploited due to flawed balance resets in the exitProgram function. The attacker took advantage of improperly cleared user balances, repeatedly withdrawing tokens and resulting in a total loss of about $19,500.
The vulnerability stemmed from the withdrawAll function, which calculates a user’s withdrawal amount by summing user.balance, user.balanceUSDT, and user.balanceUSDC. After the withdrawal, only user.balance was set to zero, leaving user.balanceUSDT and user.balanceUSDC intact. An attacker increased their balance in USDC, joined the contract’s reward queue, and then repeatedly invoked exitProgram to withdraw tokens multiple times. Each call exploited the non-zero USDT/USDC balances that were never reset, ultimately allowing the attacker to accumulate roughly $19,500 in stolen funds.
January 2025 kicked off the year with a broad spectrum of exploits totaling $62.5 million worth of losses not covered. The month was topped by two extremely prominent breaches, Phemex and FortuneWheel, which together accounted for over 90% of the month’s loss. Despite the comparatively lower number of occurrences compared to previous months the diversity of protocols used, from CeFi custodians to DeFi aggregators and NFT platforms, confirms that no type can stay immune from being exploited.
With no recoveries and several chains affected the crypto space enters 2025 with urgent lessons to advance. Cross-chain activity, GameFi speculation and still-evolving access controls are still profitable targets for malicious actors. As protocols ramp up innovation in the next year they will have to do so with enhanced operational security, frequent auditing and rapid response procedures to avoid being the next entry into the REKT Report.
October 2025 saw a total of $38.63 million lost across nine distinct security incidents in both centralized and decentralized platforms.
The third quarter of 2025 marked yet another turbulent period for the DeFi and wider crypto ecosystem, with $434,124,000 lost to exploits, scams, and security failures across both centralized and decentralized platforms.
June 2025 witnessed another alarming month for Web3 security, with a total of $114,768,000 lost during 11 separate attacks
May 2025 saw both DeFi and CeFi security once again under attack, with $275,953,000 lost across just 8 recorded incidents
April 2025 witnessed a large escalation in exploit volume and value, with a massive $5,919,684,000 being stolen in 10 confirmed events.
Q1 2025 marked one of the worst quarters in blockchain exploit history, with total recorded losses topping $2,052,584,700 across 37 incidents
© De.Fi. All rights reserved.