DeFi Rekt Report October 2025: $38.6 Million Lost Across 9 Exploits
October 2025 saw a total of $38.63 million lost across nine distinct security incidents in both centralized and decentralized platforms.
Are you puzzled by the term ‘crypto honeypots’ and why it’s a buzzword in the DeFi space? The simple answer is this: honeypots are sophisticated scams that have the potential to quickly steal your funds. Because of this, honeypot checkers are vital to securing any onchain crypto portfolio.
This article will provide you with insights regarding what a honeypot is, why it’s dangerous, and how to use our cutting-edge honeypot detector for a comprehensive analysis of tokenomic risk across ETH, BSC, or most other popular EVM chains.
Navigating the crypto space without a reliable honeypot checker is like walking blindfolded on a minefield. Let’s introduce you to our Scanner free smart contract auditing tool, a revolutionary honeypot detector designed to empower you in your crypto journey.
To use our groundbreaking Scanner tool, the process is as simple as it is effective. It starts with you entering the smart contract address of the token or contract that you want to audit. No matter what token or contract you have in mind, our tool is robust and versatile enough to handle it, as it supports more than 40 different chains. This support extends across a huge array of platforms, giving you a broad spectrum of audit capabilities to ensure no stone is left unturned.
The Scanner performs a thorough audit of your contract in a matter of seconds – yes, seconds. This speed is coupled with an unparalleled depth of analysis to ensure you receive a report that is as quick as it is complete. The audit scrutinizes every nook and cranny of the contract, digging deep into its mechanics, behaviors, and patterns. This detailed report comes at no cost to you. That’s right – our tool is completely free, making it an invaluable companion for any savvy crypto investor.
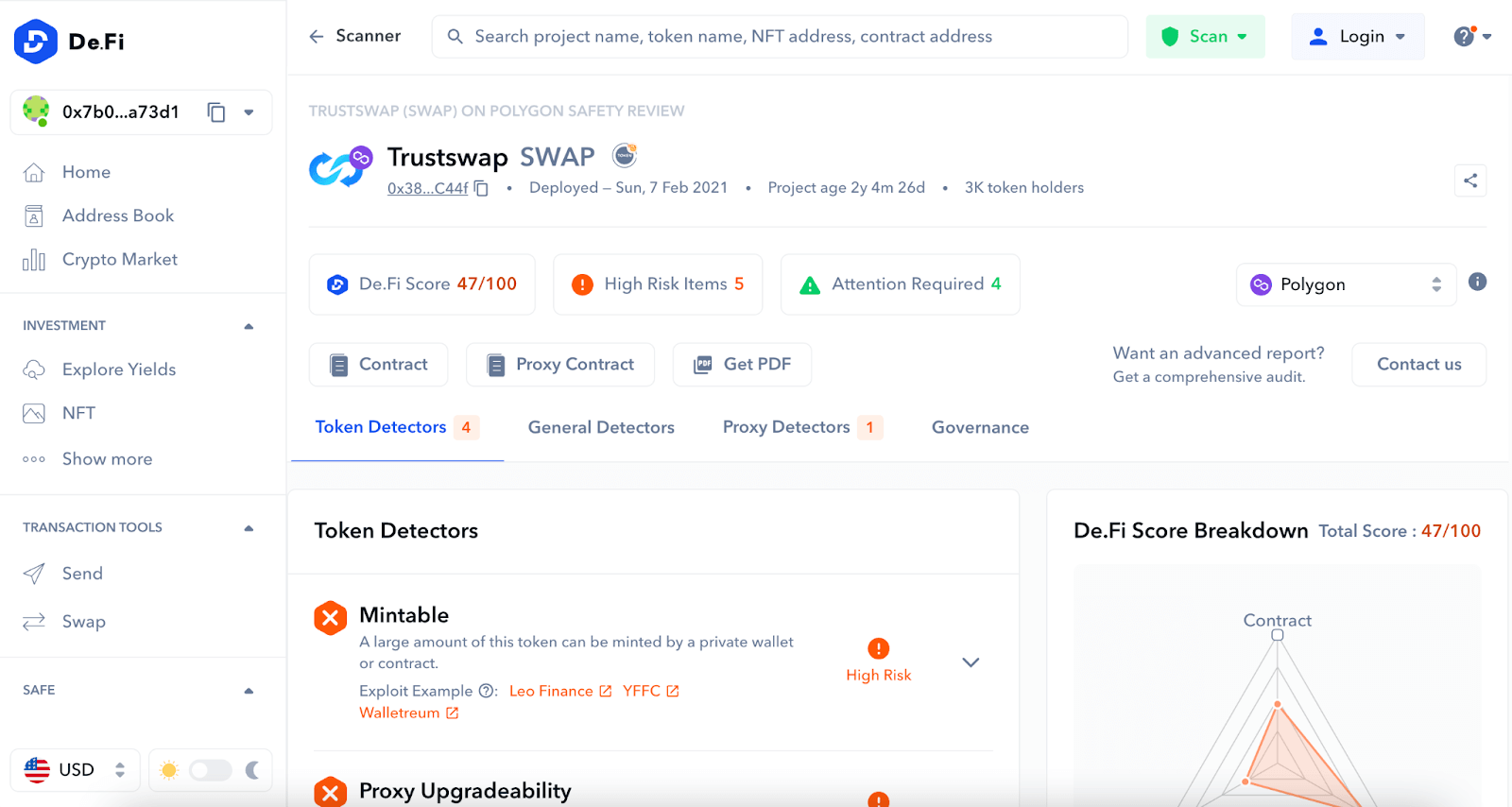
A significant component of this report is the honeypot check. This is a dedicated section that alerts you if your token could potentially be a honeypot. It flags the possibility of your investment being a trap for your funds, thus allowing you to steer clear of potential financial heartache.
Our tool goes beyond simply alerting you; it also provides you with the opportunity to examine the underlying code causing the flagged issues. This detailed examination grants you a deeper understanding of your investment, providing you insights into its functionality, behavior, and potential risks.
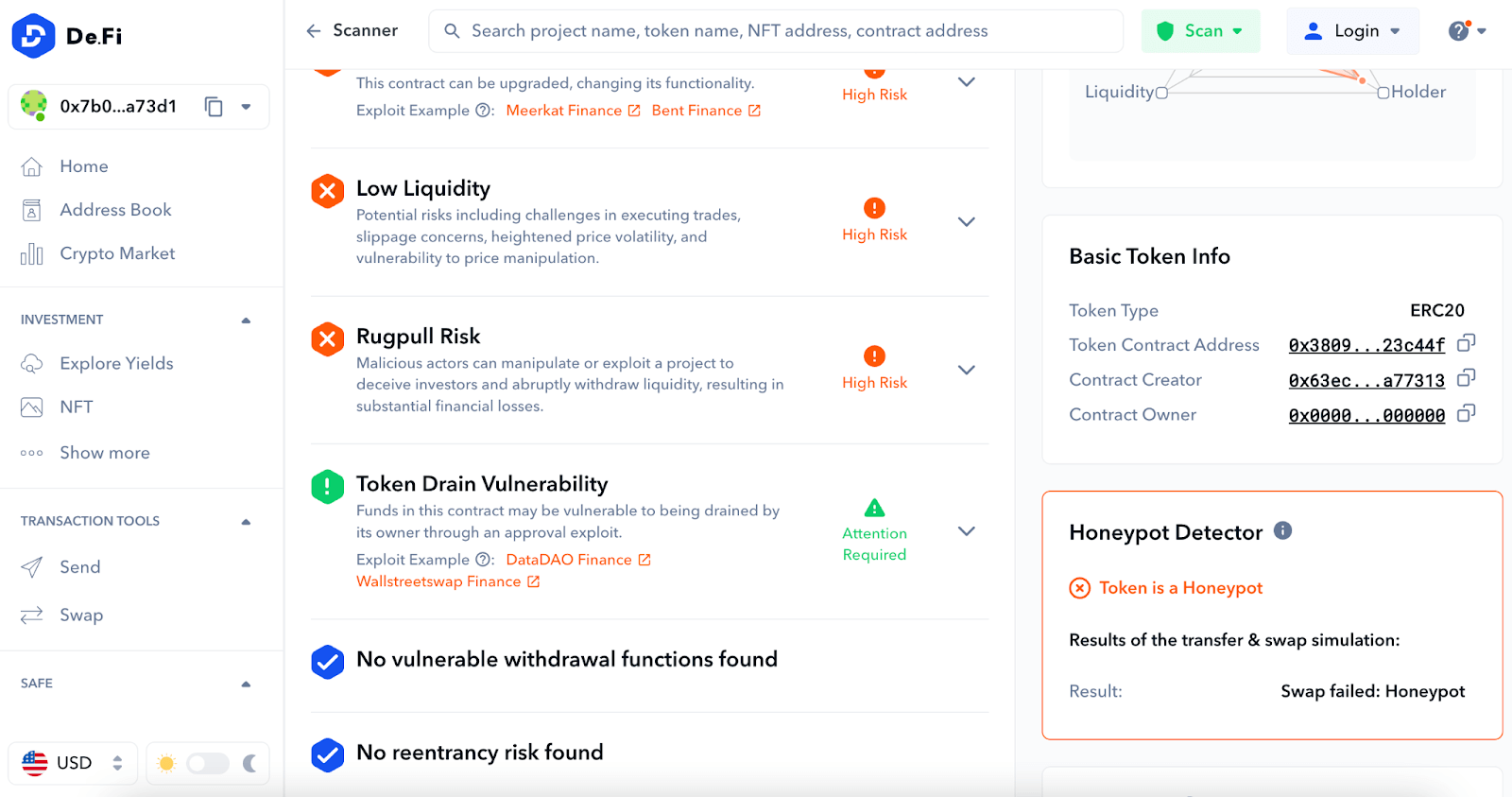
However, our scanner doesn’t stop at just analyzing smart contract risk. It takes a holistic approach to ensure you’re as informed as possible about your potential investment. It delves into tokenomic risk analysis, examining factors like the distribution of token holdings and liquidity.
For instance, the top 10 token holders analysis is a critical examination that highlights the distribution of tokens among the top holders, providing insights into the potential for market manipulation. Similarly, the liquidity analysis sheds light on the liquidity health of the token, offering crucial information that can impact your decision to invest.

In the rapidly evolving world of DeFi, honeypots are an increasingly prevalent and insidious type of scam. The term “honeypot token” can seem strange, even appealing, but don’t be fooled.
A honeypot in DeFi is essentially a cleverly disguised trap. On the surface, these tokens bring an allure of profitability, often accompanied by promises of high returns and rapid growth. This appeal is a lure designed to draw in investors looking for quick profits. Once investors buy into these seemingly attractive tokens, the grim reality becomes apparent.
Unlike legitimate tokens, honeypot tokens have a devious catch – there’s no way out. Scammers design honeypot smart contracts in such a way that your funds are essentially trapped. Selling or trading these tokens is impossible due to their design which leaves your investment stuck indefinitely.
That’s where a robust and reliable honeypot checker comes into play. It’s an essential tool that safeguards your hard-earned investments from falling into such nefarious traps. With the advent of our advanced honeypot detector, and specifically, the honeypot detector for Ethereum (ETH), detecting and avoiding honeypots on ETH has become simpler, more efficient, and safer than ever before.
This level of protection extends beyond ETH. Whether you’re dealing with Binance Smart Chain (BSC), Base, Arbitrum, Optimism, Polygon, AVAX or any other Ethereum Virtual Machine (EVM) compatible chain, our honeypot detector is an invaluable ally. It helps to shield you from the potential dangers lurking in the world of DeFi scams.
When navigating the DeFi landscape, understanding and identifying potential pitfalls is as important as spotting opportunities. In addition to honeypots, several other red flags are frequently encountered in tokens and contracts. These issues may pose serious threats to the safety and profitability of your investments. It’s therefore critical for DeFi users to be aware of them. Here are the five most common issues you might encounter beyond a token being a honeypot.
When contract creators renounce ownership, they can no longer make changes to the contract. While this is sometimes seen as a positive, demonstrating that the project can’t be altered maliciously, it can also be problematic. For instance, if an exploit or bug is discovered in the contract, there’s no way to fix it.
This occurs when an external contract hijacks the control flow, leading to malicious re-entries. It’s a common vulnerability that can result in the theft of funds from the contract.
Front-running occurs when an attacker gains knowledge of a transaction in the mempool (the holding area for pending transactions) and places their transaction first with a higher gas fee, influencing the outcome of the original transaction.
Some tokens retain the ability to mint new tokens after the initial supply has been set and distributed. This function can lead to inflation and dilution of token value.
Although delegate call has legitimate uses, such as upgrading contracts, it can also be exploited to alter contract logic and state, leading to security issues.
The Scanner tool automatically looks for these common issues, alongside detecting honeypots. Its audit process evaluates contracts for these common red flags, providing a comprehensive analysis of potential vulnerabilities. By identifying these risks before investing, users can avoid falling victim to crypto hacks & scams.
Worried you’re NGMI? Wondering how to keep your capital safe until the next bull run? Enhance your web3 safety and protect your assets with De.Fi. We provide a range of valuable tools and resources. De.Fi offers comprehensive solutions to help users navigate the decentralized finance landscape securely, such as Scanner and our De.Fi Shield, your personal web3 revoke permissions tool & antivirus.
We help investors make informed decisions and avoid potential pitfalls. De.Fi equips users with the knowledge and insights needed to protect their funds, understand smart contracts, and stay updated on the latest security practices. Visit our YouTube channel and explore our tools to bolster your web3 safety and ensure a secure crypto experience.
October 2025 saw a total of $38.63 million lost across nine distinct security incidents in both centralized and decentralized platforms.
The third quarter of 2025 marked yet another turbulent period for the DeFi and wider crypto ecosystem, with $434,124,000 lost to exploits, scams, and security failures across both centralized and decentralized platforms.
June 2025 witnessed another alarming month for Web3 security, with a total of $114,768,000 lost during 11 separate attacks
May 2025 saw both DeFi and CeFi security once again under attack, with $275,953,000 lost across just 8 recorded incidents
April 2025 witnessed a large escalation in exploit volume and value, with a massive $5,919,684,000 being stolen in 10 confirmed events.
Q1 2025 marked one of the worst quarters in blockchain exploit history, with total recorded losses topping $2,052,584,700 across 37 incidents
© De.Fi. All rights reserved.