DeFi Rekt Report October 2025: $38.6 Million Lost Across 9 Exploits
October 2025 saw a total of $38.63 million lost across nine distinct security incidents in both centralized and decentralized platforms.
Here at De.Fi, we have one main enemy: crypto scams. As inventors of the first web3 antivirus, we’ve made it our mission to make simple, accessible, and effective DeFi security tools the norm.
This started with our REKT Database, a free collection of analyses regarding the most infamous hacks and scams in crypto history. Since then, we’ve expanded our comprehensive crypto wallet dashboard to include features that make sure you don’t end up being involved in the REKT Database’s next entry. These features are Scanner and Shield, two of the most powerful free DeFi safety analysis tools.
In this blog, we’ll cover the unique feature set Scanner and Shield bring to the table as well as outline some of the most common DeFi scams they’ll be able to help you avoid.
Looking for a quick summary? Check out the video above from the De.Fi YouTube
With DeFi continuing to expand via new Ethereum L2s and developing L1 networks, many users are adventuring into the deep waters of trading and investing in lesser-known tokens. These tokens can offer potentially huge returns because they allow savvy crypto researchers to get in “early” as opposed to more established coins where there is less of an edge.
But with these handsome rewards comes a trade-off: If you’re thinking about purchasing a new coin, it’s very hard to tell if it’s trustworthy or not. Most people don’t have the technical expertise to check Etherscan and analyze whether or not a coin is a rug pull or honeypot. You can wait and see if others do the work for you, but by the time you see a thread on X confirming that a coin is legit, you may have missed your chance at a solid buy.
What can the average trader do to keep their edge? Enter De.Fi Scanner, the best free smart contract auditor in the DeFi space:
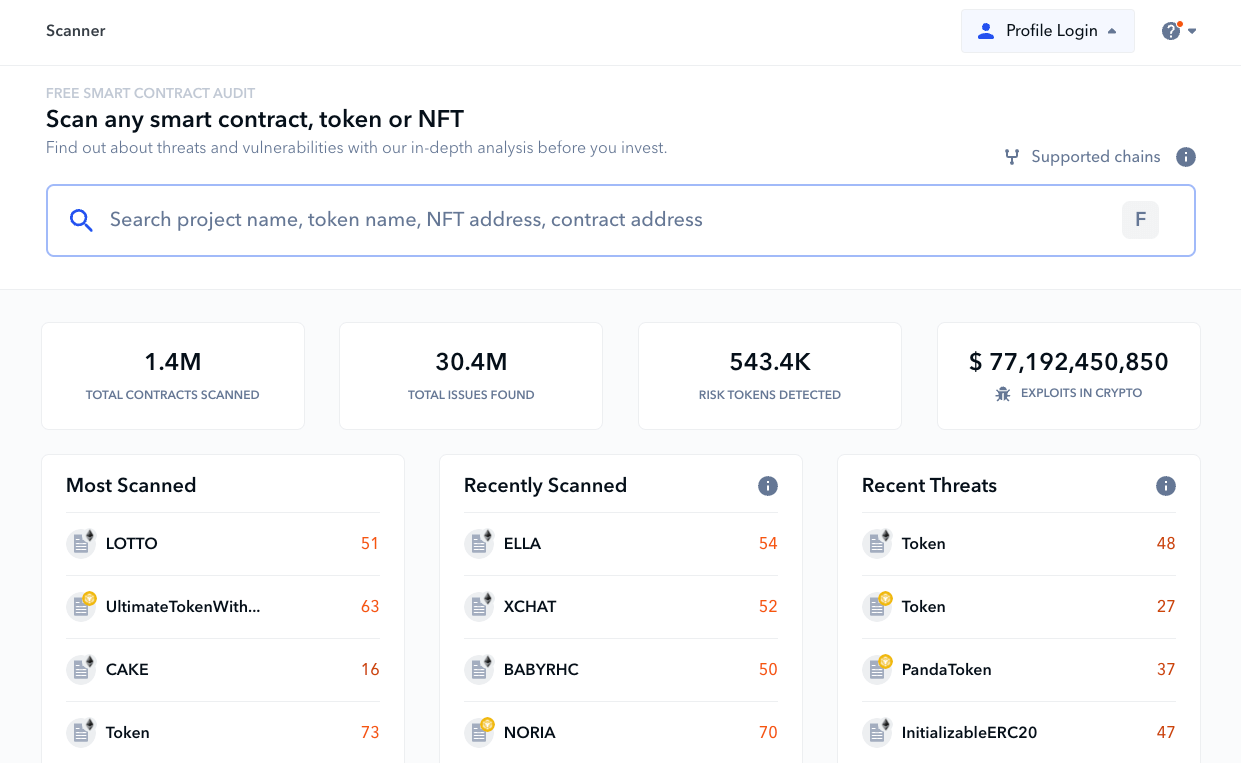
Below are just some of the features that make Scanner so useful for DeFi investors:
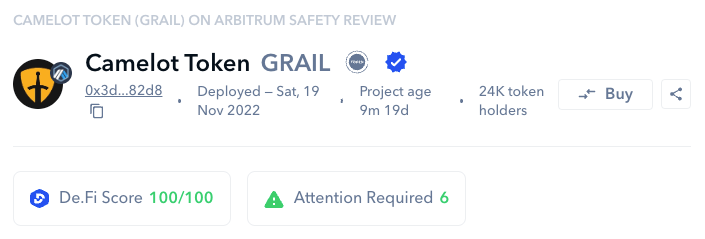
Every Scanner query returns the user with a unique “De.Fi Score.” This gauge offers an all-encompassing assessment for tokens, rooted in a wide array of considerations. From diving into contract details, analyzing developer actions, observing transaction behaviors, and beyond, this score acts as an indicator that can help the user quickly determine relative safety between various tokens. At its core, it fuses data analysis with blockchain nuances, making token evaluation a breeze.
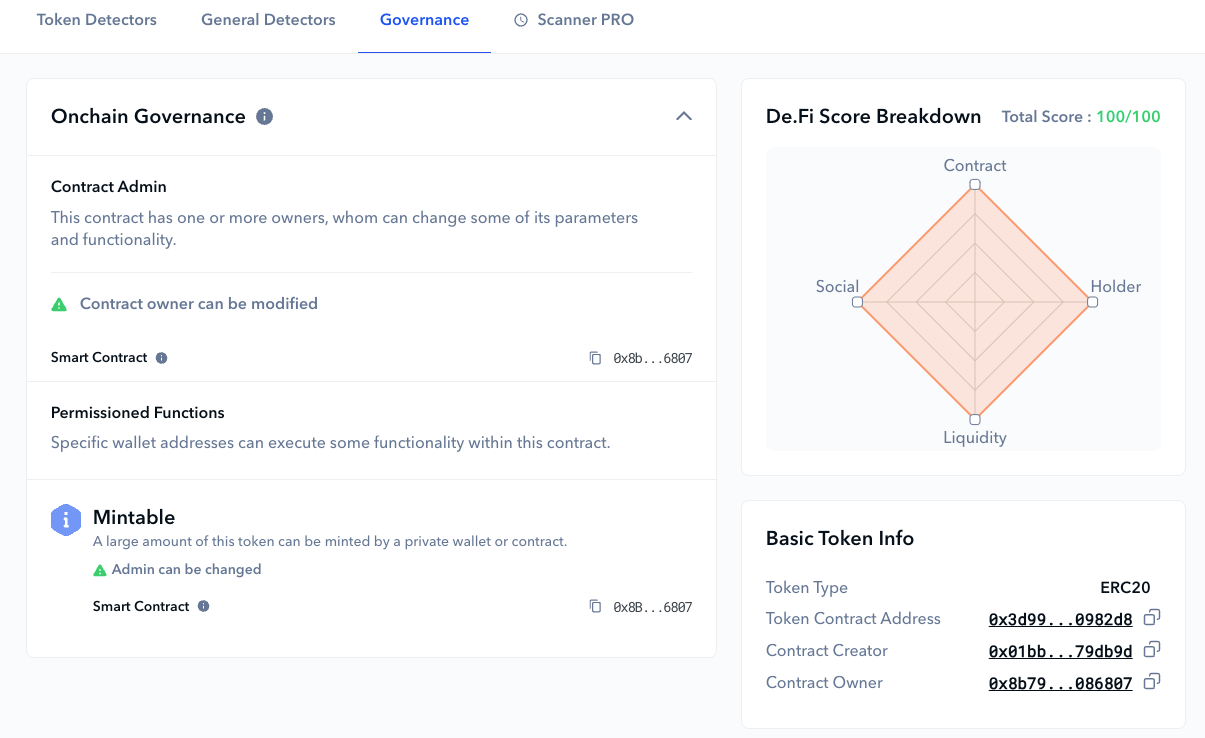
While numerous scanning tools often overlook token governance, Scanner pioneers by delivering an in-depth governance analysis, highlighting essential contract management and specific permissioned function details.
Scanner makes it easy to avoid blatant DeFi scams by sorting tokens into three risk categories: “High Risk,” “Medium,” and “Attention Required.” This layered classification allows users to quickly grasp the potential risks linked to specific tokens, acting as an advanced scam detector. This clear arrangement aids users in making savvy choices, letting them match their investments to their comfort with risk.
The versatility of Scanner shines bright with its support for multiple blockchain protocols. As the crypto ecosystem expands, users need tools that cater to a plethora of chains. Scanner stands tall, catering to various chains, and ensuring a broad spectrum of coverage.
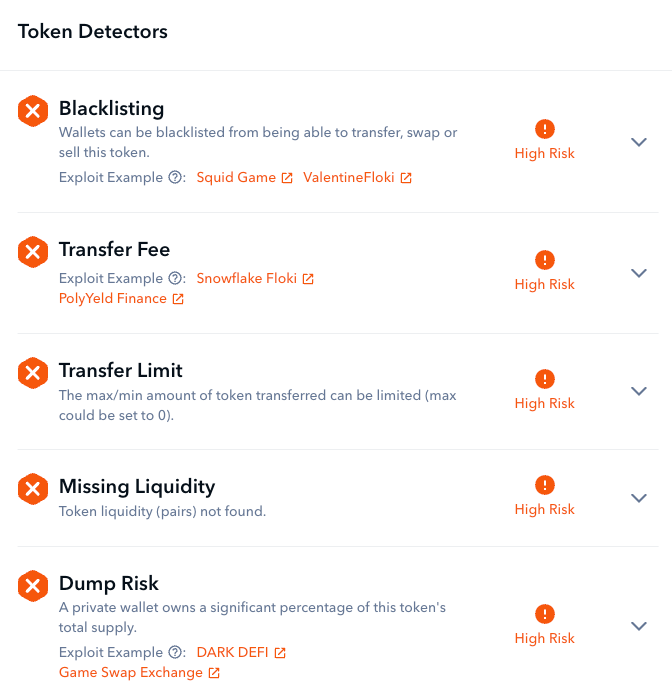
Scanner excels at spotting deceptive maneuvers hidden within smart contract code. Be it novel coin minting methods, suspicious proxy activities, or questionable ownership setups, Scanner provides in-depth knowledge, ensuring users stay shielded from looming dangers.
De.Fi Scanner also offers API functionality to give developers an upper hand when fighting scams. Anyone can weave Scanner’s expertise seamlessly into their app framework. In the fast-paced world of web3, our DeFi API offers the automation edge that you need.
For those who like having a physical copy or want to dive into the nitty-gritty of a token without being online, Scanner offers the ability to grab a detailed report as a PDF. This enhances user flexibility and assists in both record-keeping and in-depth analysis.
While Scanner covers the needs of users who are researching tokens they have yet to interact with, Shield is your one-stop analyzer for checking existing wallet interactions and permissions.
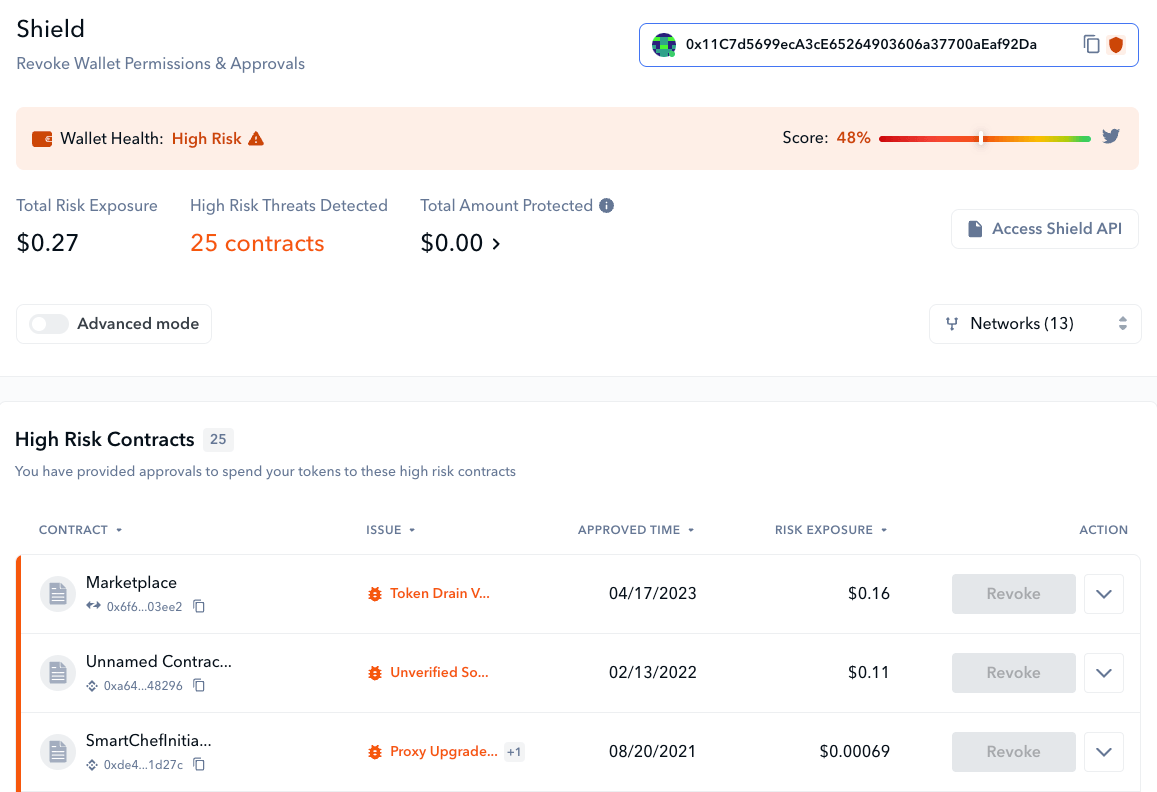
Thinking about checking out Shield? You should know about the following features:
The flagship feature of De.Fi Shield is our approval check. By reviewing the smart contracts you’ve engaged with, we can inform you about any lingering approvals you’ve given and assess the risks associated with such permissions.
Contracts that could potentially be exploited are prominently highlighted in our High Risk Contracts section, accompanied by a concise description of the potential problem. If you choose to “Revoke” from within our app, any past approval will be quickly set to 0, disallowing the contract from transferring any tokens on your behalf:
Thanks to our DeFi dashboard’s wealth of data, we can also analyze the individual tokens in a wallet. We spotlight those that might be susceptible to threats in our High Risk Tokens section. We provide a rationale for their classification and detail your exposure to such tokens. Using the “Swap” option, you can effortlessly and securely exchange these vulnerable tokens out of your wallet directly within the De.Fi app.
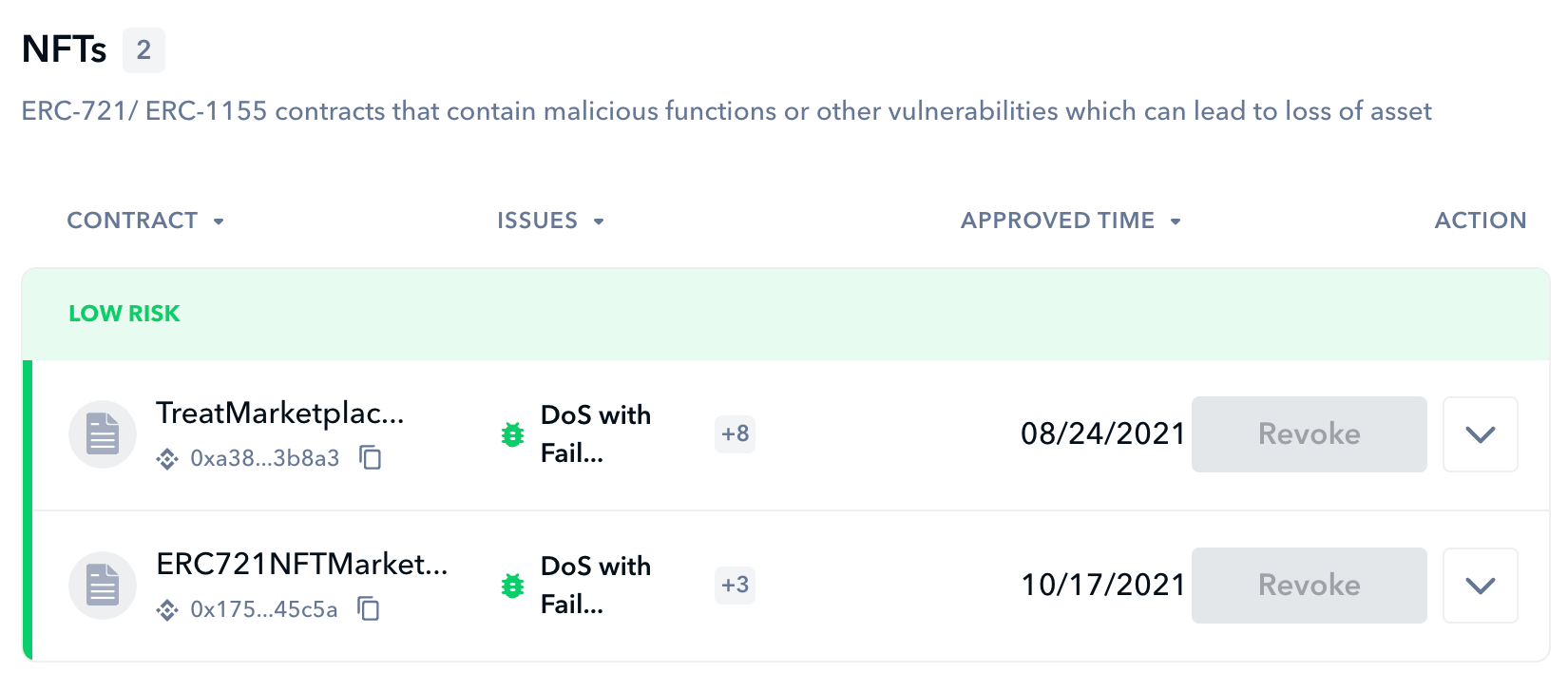
Much like our contract approval assessments, the Shield page will distinctly indicate any NFTs (either ERC-721 or ERC-1155 contracts) in your wallet(s) that have lingering approvals for potentially vulnerable exchange, trading, or marketplace contracts. Using the “Revoke” feature, you can effortlessly rescind these approvals.
Our default interface highlights the most pressing security concerns. However, activating Advanced Mode lets you explore a broader spectrum of issues pinpointed by our Shield, enhancing your wallet’s protection.
For tailored insights, you can filter through issues to display only those that concern you. Plus, with Advanced Mode on, you can modify token approvals instead of just revoking, helping manage past unlimited allowances.
Looking to learn more about DeFi scams in general and what sort of exploits you may run into? For in-depth research, we highly recommend our REKT Database of crypto hacks and scams. There, you’ll find a breakdown of every significant event since 2011, with written descriptions by our expert engineers.
To give you a brief overview in the meantime, here are some of the most common threats that Scanner and Shield should be able to protect you from.
In DeFi, a honeypot is a deceptive trap, presenting tokens with the appeal of high returns and rapid growth to entice investors. However, once investors are hooked, the true nature emerges. Honeypot tokens are cunningly designed to trap funds, making selling or trading them impossible and leaving investments stranded indefinitely.
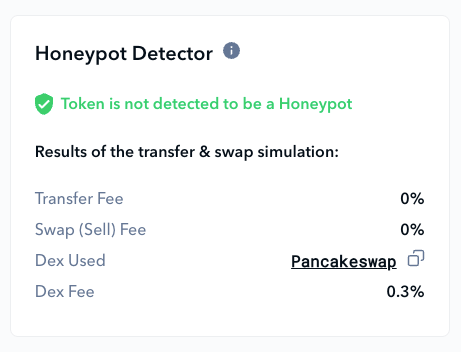
Scanner’s built-in honeypot checker
One of the core selling points of crypto for many people is that tokens are supposed to have a set supply. While this is true for many larger, more established coins like Bitcoin and Ethereum, standard DeFi ERC-20 tokens can have functions to mint more coins within their code.
Malicious minting happens when a token is deployed, a liquidity pool is created, and buyers are attracted to the token. After these buyers begin to purchase (believing the project to be a legitimate investment with a fixed supply), the exploiter will use the function within the token’s contract to mint a huge amount of tokens, then dump them into the liquidity pool completely obliterating the price. This is a truly devious DeFi scam and why you should always be wary of tokens that have questionable minting functionality built in.
In DeFi, traders are dependent on liquidity mining pools for them to swap tokens back and forth. While this is generally secure in practice, for many riskier coins, there may only be one or two large providers of liquidity backing a pool. With this in mind, another common DeFi scam tactic is for the exploiter to withdraw their liquidity pool funds once a token’s value has spiked. This renders the token worthless and unsellable for holders.
One of the more blatant scam tactics that malicious actors will use is to simply hold a huge supply of a token within their own wallet. While this should be an obvious warning sign of foul play to many users, it is surprisingly common for traders to look past the warning sign that a large portion of the coin supply is held by a single wallet, trusting that the whale wallet won’t sell their outsized share of tokens. These amounts don’t even have to be huge to the average trader. Owning even 5% of the token supply might be enough to cause significant volatility in the token price if there is only minimal liquidity.
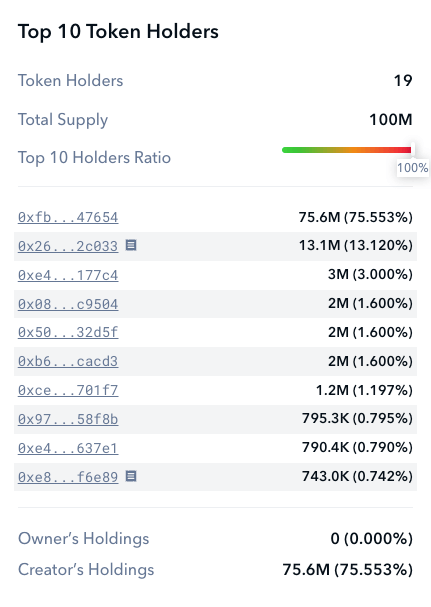
Scanner will make sure you know when token holders look suspicious
Still, it’s crucial to understand that numerous genuine projects maintain wallets with a significant portion of the supply, having committed to retaining these tokens for designated durations or for certain objectives. Context plays a vital role when assessing potential DeFi scam indicators, and a high wallet supply percentage doesn’t necessarily predict adverse results.
Pausing in the transfer() and transferFrom() functions can make the token non-transferrable for all users with one click. The contract admin/owner can set a state under which any function containing a requirement for this state will be blocked from execution. Doing this can effectively leave all buyers of a specific token out in the cold and unable to swap back to a more valuable coin.
A similar tactic is called “Blacklisting”. This restricts specific users from invoking a particular function by adding blacklisted addresses to a prohibited list. When discussing scams that could make ERC-20 tokens unsellable, it’s crucial to consider blacklisting within the transfer() function.
Transfer fees on ERC-20 transfers can be a potential scam vector as well. If such a fee exists and can be set to 100%, users might lose tokens during transfers. Generally, a transfer fee of up to 5% is deemed acceptable. However, even fees below 5% can disrupt a protocol’s functionality or expose it to vulnerabilities.
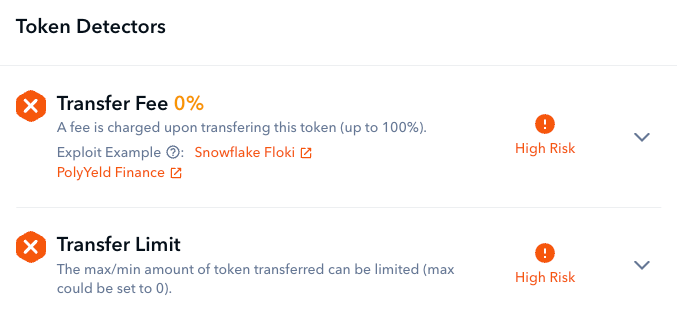
Examples of high-risk transfer warnings
Another method hackers use to regulate user transfers is by placing caps on the number of tokens that can be transferred. It’s crucial to monitor both the maximum and minimum thresholds of whatever token you are buying. If the upper limit is pegged at 0 or the lower limit is excessively high, transfers get entirely halted, rendering the token unsellable.
Smart contract code on a blockchain is immutable, leading some developers to use upgradable proxies. Essentially, two contracts are deployed: one for information storage and gateway functions, and another for execution logic. Users interact with the proxy contract. When devs want to update logic, they deploy a new ‘implementation’ contract linked to the existing proxy, keeping its address unchanged and transparent to users. However, this adaptability poses risks, as contracts can be maliciously altered, leading to potential scams.
These scam contracts, often also referred to as “wallet drainers”, are one of the most harmful DeFi scams because they don’t just impact the coin you are buying: they could wipe out your entire portfolio in seconds. Once permissions are granted, they can completely empty the wallets of affected individuals, stealing native coins, ERC-20 tokens, and NFTs.
If you are connecting a wallet to a website in web3 and granting permissions, double check that you are on a legitimate site and not a domain that looks similar but is not actually correct. For example, hackers might use a domain like “sushicrypto.net” and make it look like the reputable “sushi.com” to steal the funds of unwitting users.
Whether you’re a seasoned yield farmer looking for the highest liquidity mining APYs or an industry beginner trying to build capital by farming retrodrops, DeFi has the tools you need to up your game.
Control your digital assets with our full suite of products and stay up-to-date with our non-stop content. Check the blog and YouTube weekly for the latest news, follow us on Twitter, and join our Telegram to make sure you never miss a beat.
October 2025 saw a total of $38.63 million lost across nine distinct security incidents in both centralized and decentralized platforms.
The third quarter of 2025 marked yet another turbulent period for the DeFi and wider crypto ecosystem, with $434,124,000 lost to exploits, scams, and security failures across both centralized and decentralized platforms.
June 2025 witnessed another alarming month for Web3 security, with a total of $114,768,000 lost during 11 separate attacks
May 2025 saw both DeFi and CeFi security once again under attack, with $275,953,000 lost across just 8 recorded incidents
April 2025 witnessed a large escalation in exploit volume and value, with a massive $5,919,684,000 being stolen in 10 confirmed events.
Q1 2025 marked one of the worst quarters in blockchain exploit history, with total recorded losses topping $2,052,584,700 across 37 incidents
© De.Fi. All rights reserved.