DeFi Rekt Report October 2025: $38.6 Million Lost Across 9 Exploits
October 2025 saw a total of $38.63 million lost across nine distinct security incidents in both centralized and decentralized platforms.

DeFi stands for “decentralized finance” but many users often overestimate just how decentralized much of the infrastructure is.
While the core networks that yield farming protocols run on like Ethereum and BNB Chain are sufficiently decentralized and censorship-resistant, the same cannot be said for many DeFi protocols. In fact, some of the most popular DeFi protocols with massive amounts of TVL can often have administrative controls that allow centralized actors to access funds in ways users might not realize.
It’s important to note that many of these administrative controls are safety mechanisms and moderation controls put in place by protocols for good reason. However, it’s also a best practice for users to identify all potential risk factors before participating in DeFi to fully grasp the investments they are making.
One of the common administrative controls used throughout DeFi is MasterChef contracts. In this blog, we’ll cover what these contracts are, the potential risk factors they can enable, and how users can use our DeFi dashboard antivirus features to identify portfolio exposure to centrally controlled smart contracts.
A MasterChef contract is a type of DeFi smart contract that usually governs the liquidity mining functions of a decentralized exchange (DEX). It allows administrators with access to the MasterChef contract to customize exactly what the project’s liquidity pools are able to do.
These liquidity pools are extremely important because they represent the fundamental infrastructure of a decentralized exchange. Liquidity pools allow users to provide capital to the exchange in return for fees and protocol liquidity mining incentives, while also allowing other users of the exchange to seamlessly swap between multiple coins via automated market-making (AMM) technology.
Think of liquidity pools as a “vault” and its corresponding DEX as a bank. All the functions of the bank are dependent on the capital that is deposited in its vault. A MasterChef contract, therefore, is what the operators of a DEX will use to manage their vault.
While MasterChef contracts have become fairly prevalent across DeFi, users should understand that they are not a requirement for operating a DEX. The term MasterChef came into popular use because it was the name of the liquidity pool management contract originally used by the popular Uniswap fork SushiSwap (now Sushi.com) when it first launched in 2020. MasterChef was actually one of the core innovations separating Sushi as a competitor when the exchange launched.
While managing a DEX’s capital reserves is obviously an important job, it is also one that comes with users placing great trust in the operator of the exchange. This was pointed out early on by risk-conscious DeFi users when Sushi first gained momentum:
DeFi farmers, note that if you’re thinking of using @SushiSwap, the MasterChef contract still has its owner key intact and this yields a LOT of power including sucking your LP tokens. Although this is disclosed, this is a huge risk and a lot of trust.
— Reuben Yap (@reubenyap) August 28, 2020
Nonetheless, Sushi was able to capture and maintain capital by being trustworthy with the power of the MasterChef contract. The success of the exchange and its open source nature led to subsequent forks of the codebase, with PancakeSwap, BNB Chain’s dominant DEX, being the most notable.
PancakeSwap and the majority of other Sushi forks kept the innovation of the MasterChef contract, which leads to where we are today where “MasterChef” is no longer tied to Sushi and has become common parlance amongst DeFi users for a DEX contract with management control over LP funds.
As early DeFi farmers pointed out, MasterChef contracts are incredibly powerful and can be used to execute devastating rug pulls when exploited by malicious actors. The variety of backdoors that can be hidden in MasterChef contracts is infinite. Let’s cover the major loopholes applied in this contract type in order to deceive users:
Being able to analyze a MasterChef contract or the permissions granted within a DEX’s overall smart contract code is no easy task. This is why De.Fi developed our free smart contract scanner.
DeFi users can use Scanner to run automated audits on projects, tokens, NFTs, or even liquidity pool contract addresses. Simply enter the contract address you would like to analyze and Scanner will produce a security report in a matter of minutes highlighting any potential risk issues you should be aware of:
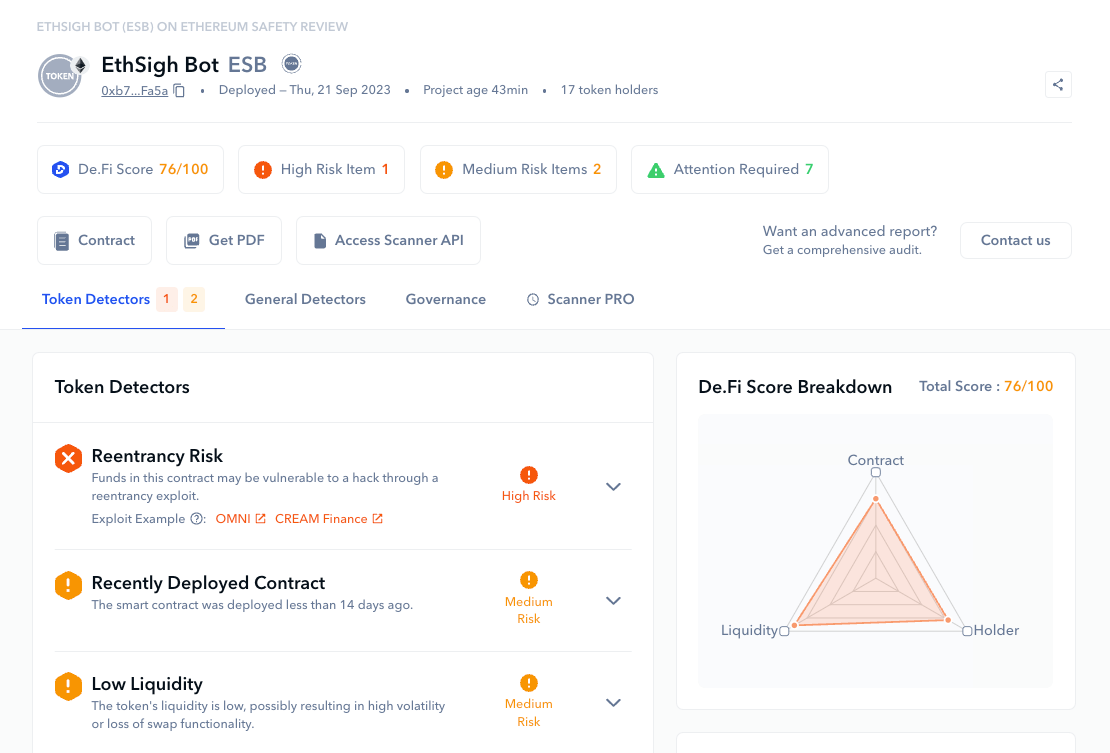
Scanner is part of our De.Fi Security Suite which also includes Shield, a wallet permissions check and revoke tool. This can be used to ensure that you have not interacted with potentially malicious smart contracts in the past. If you have, revoking permissions takes only a few clicks.
Users can also freely access a treasure trove of security analysis via our Audit Database. It’s web3’s largest database of DeFi project audits with over 9000 security reports from blockchain experts. If you’re considering interacting with a DeFi protocol, chances are you can find a security report within our database.
For the latest security news, don’t forget to follow our De.Fi Security X profile. We’ll keep you notified of any security incidents as they happen, giving you the time you need to respond appropriately. Educate yourself and stay safe with De.Fi!
October 2025 saw a total of $38.63 million lost across nine distinct security incidents in both centralized and decentralized platforms.
The third quarter of 2025 marked yet another turbulent period for the DeFi and wider crypto ecosystem, with $434,124,000 lost to exploits, scams, and security failures across both centralized and decentralized platforms.
June 2025 witnessed another alarming month for Web3 security, with a total of $114,768,000 lost during 11 separate attacks
May 2025 saw both DeFi and CeFi security once again under attack, with $275,953,000 lost across just 8 recorded incidents
April 2025 witnessed a large escalation in exploit volume and value, with a massive $5,919,684,000 being stolen in 10 confirmed events.
Q1 2025 marked one of the worst quarters in blockchain exploit history, with total recorded losses topping $2,052,584,700 across 37 incidents
© De.Fi. All rights reserved.