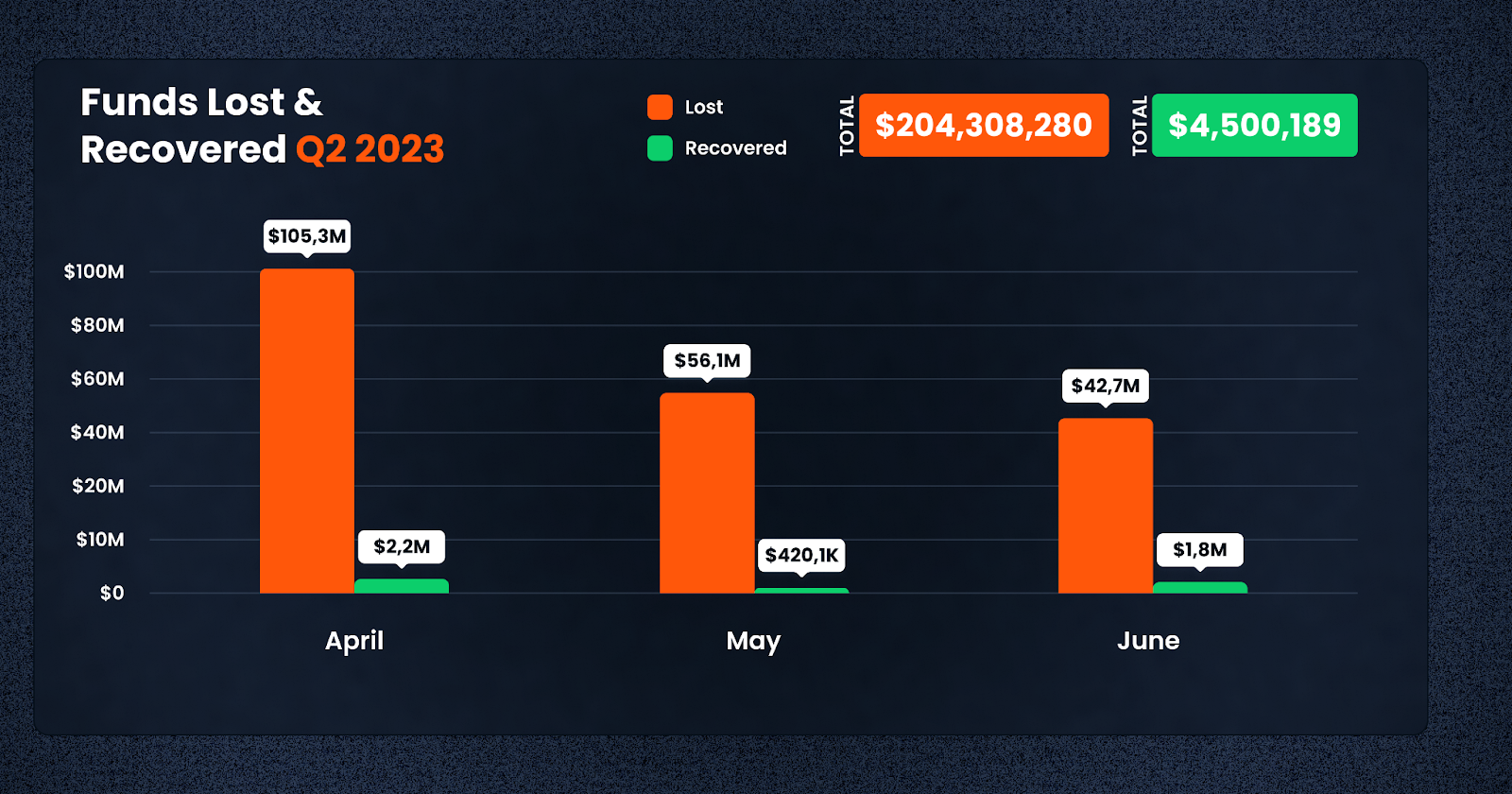
- The total of lost funds in 2023 has reached $667m with $204,308,280 lost in Q2
- Recovered funds YTD stand at $183m, representing 27,5% of the total lost funds
- The frequency of hacks has risen in Q2 2023 in almost 7 times (129 cases), comparing with 17 in Q2 2022
As we move past the halfway mark of 2023, hackers and phishing scammers are upping the stakes. In Q2 of 2023, we saw losses breach the 9-figure mark in the second quarter, bringing us to over half a billion dollars in losses for the year to date.
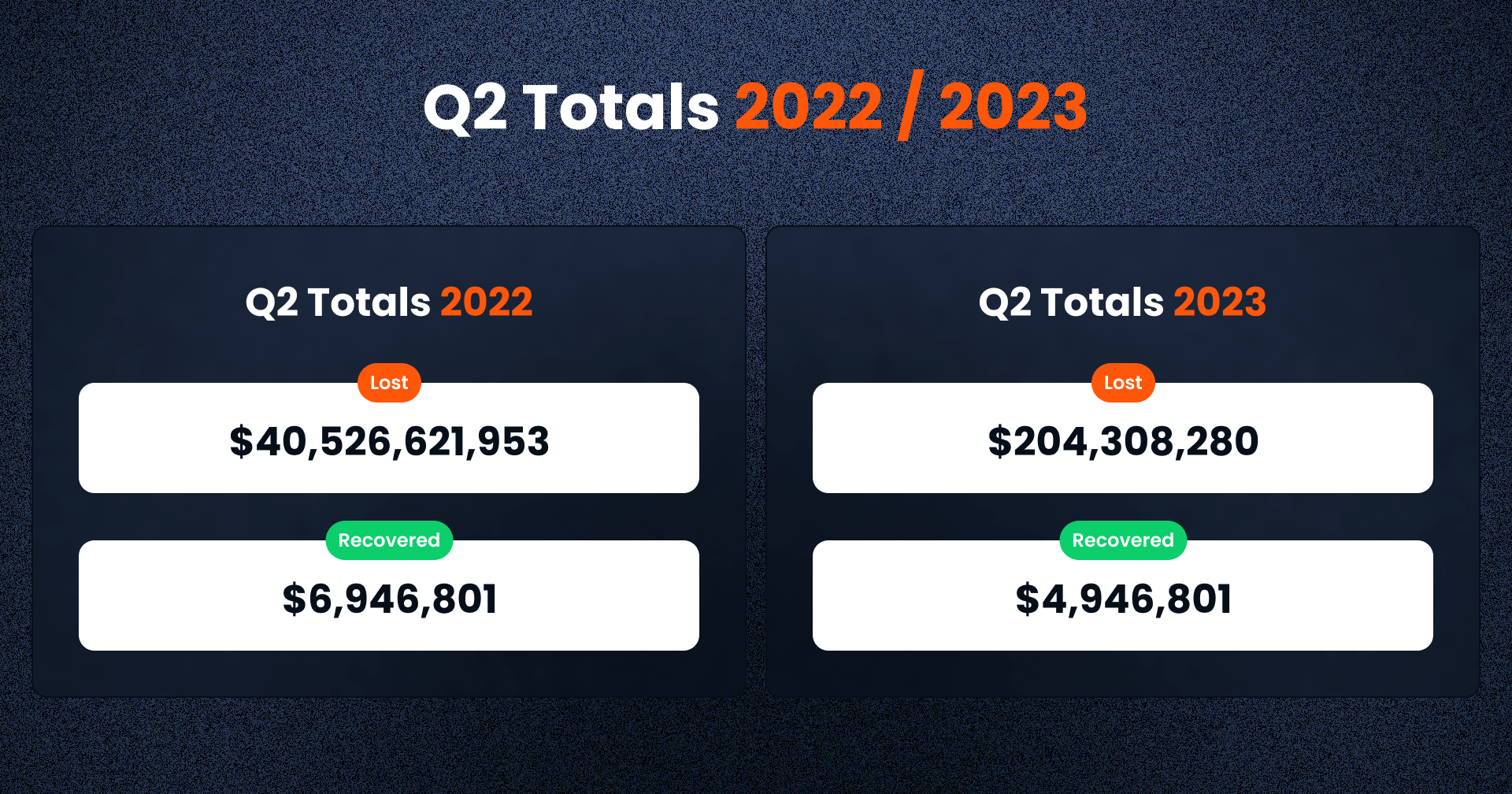
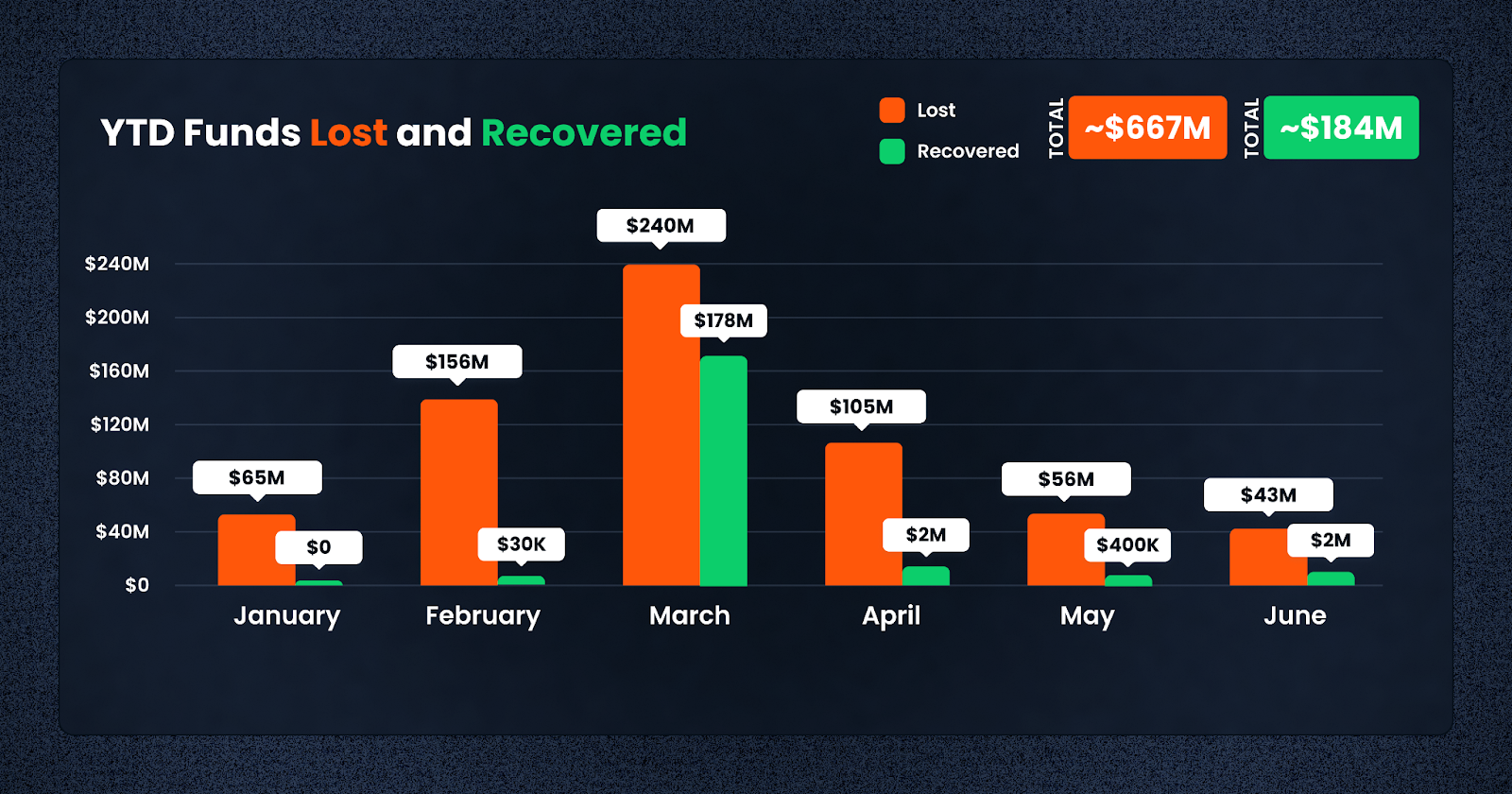
Crypto markets have faced another challenging quarter in Q2, with total losses of $204.3m, marking a significant decrease from the staggering losses of $40.5b in the same quarter last year. In the year to date since January 2023, a total of $666,5m were lost due to various scams and over $183m were recovered.
Regrettably, only a small fraction of these funds were recovered in Q2- $4.9m to be precise, which is significantly less than the $6.9m recovered in Q2 2022. This worrying trend underscores the complexities in tracing and reclaiming stolen crypto assets.
The good news, however, is that the pace at which funds are being lost has fallen for the third month in a row in June, at $42.7m, compared to $56.1m and $105.3m for May and April respectively.
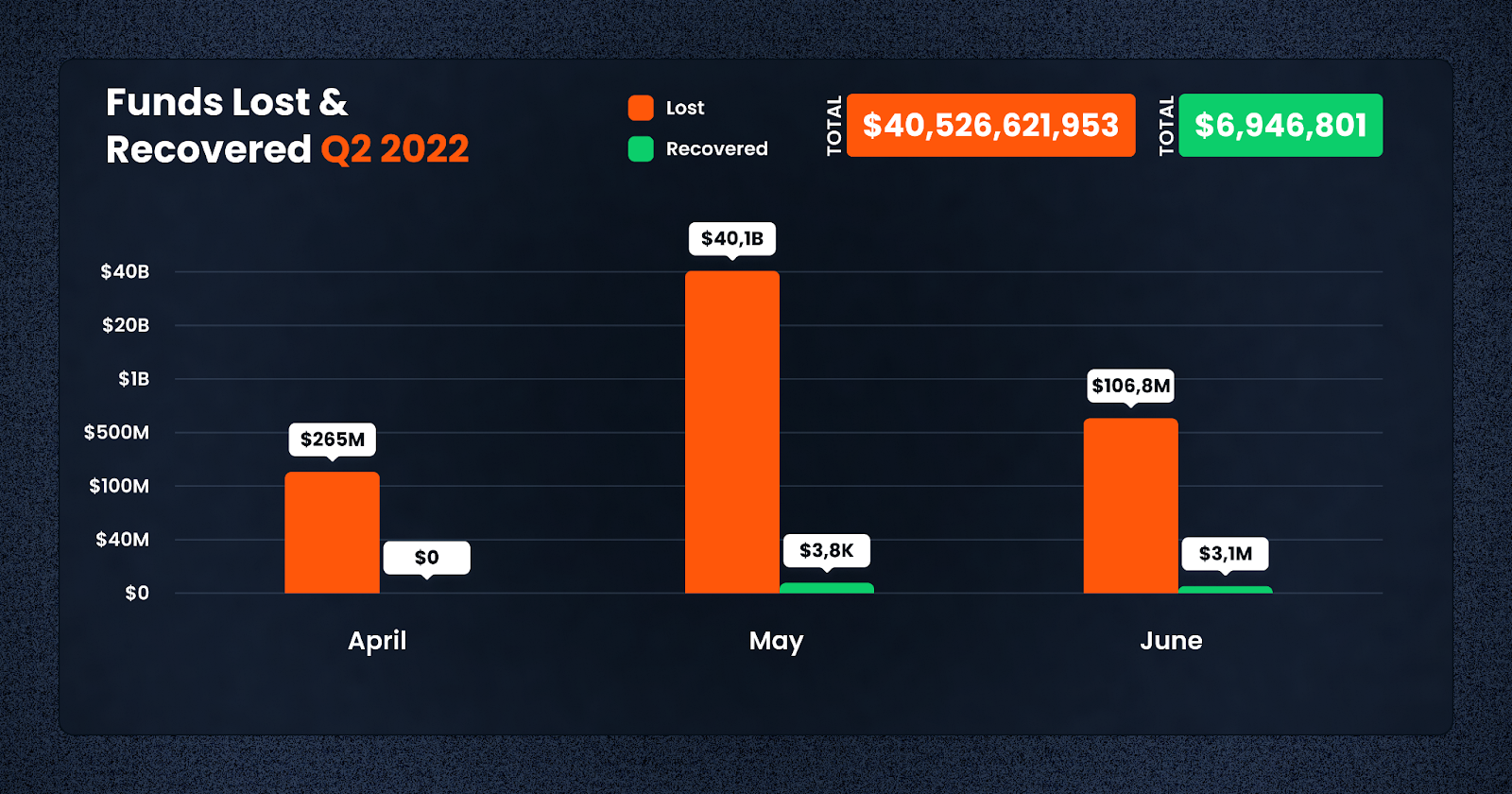
By comparison, in 2022, the losses for Q2 were largely driven by the Terra Luna collapse in May, resulting in a $40.1b loss. By comparison, losses in April and June 2022 were more comparable to the figures in 2023.
DeFi Exploit Trends
This quarter, there were a whopping 110 cases of scams, exploits or unintended losses.
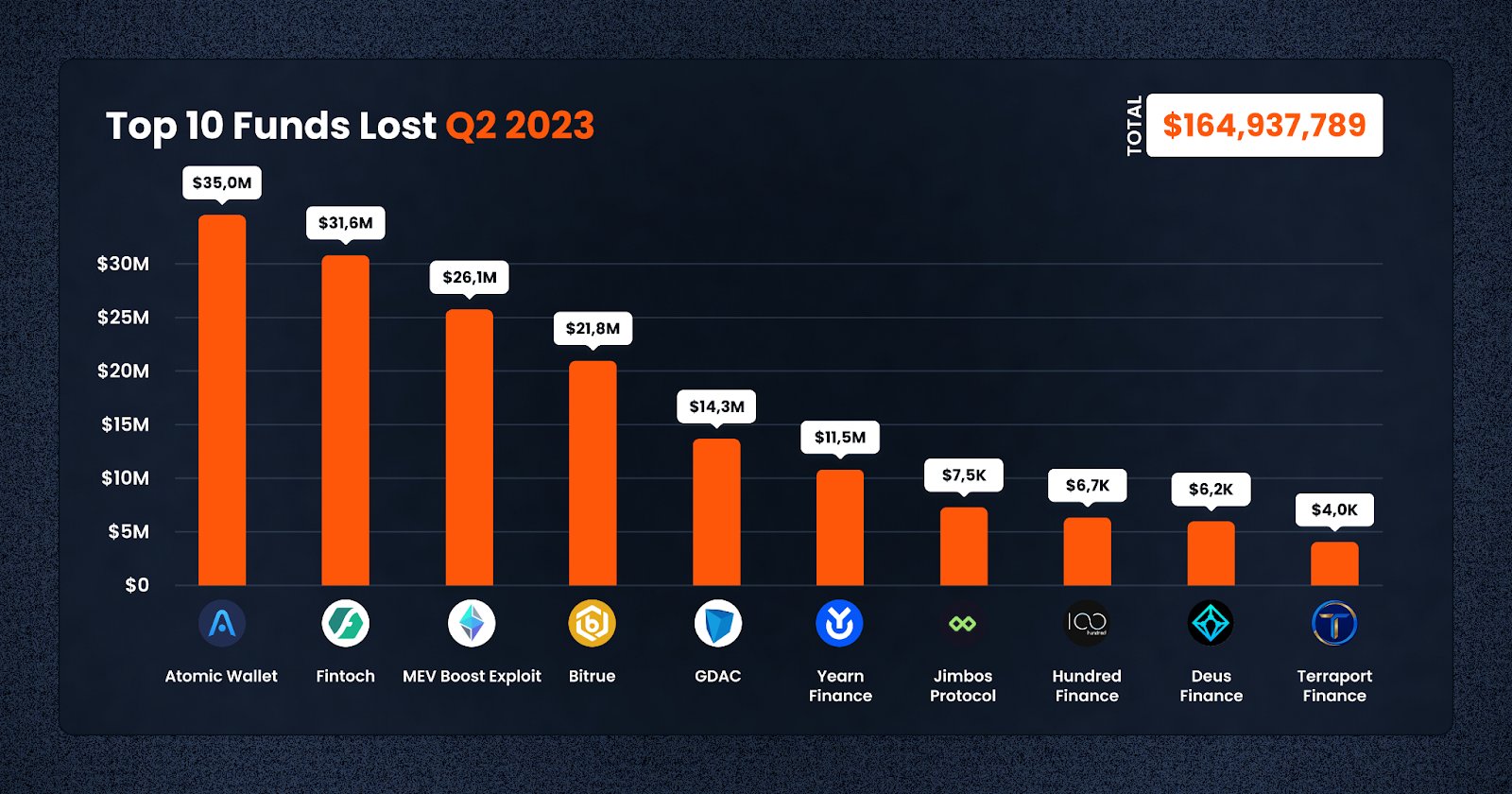
Despite the overall decrease in losses quarter-on-quarter, several high-profile cases have raised concerns. Prominent among them are Atomic Wallet, Fintoch, and MEV Boost Exploit, where a combined total of approximately $92.8m was lost.
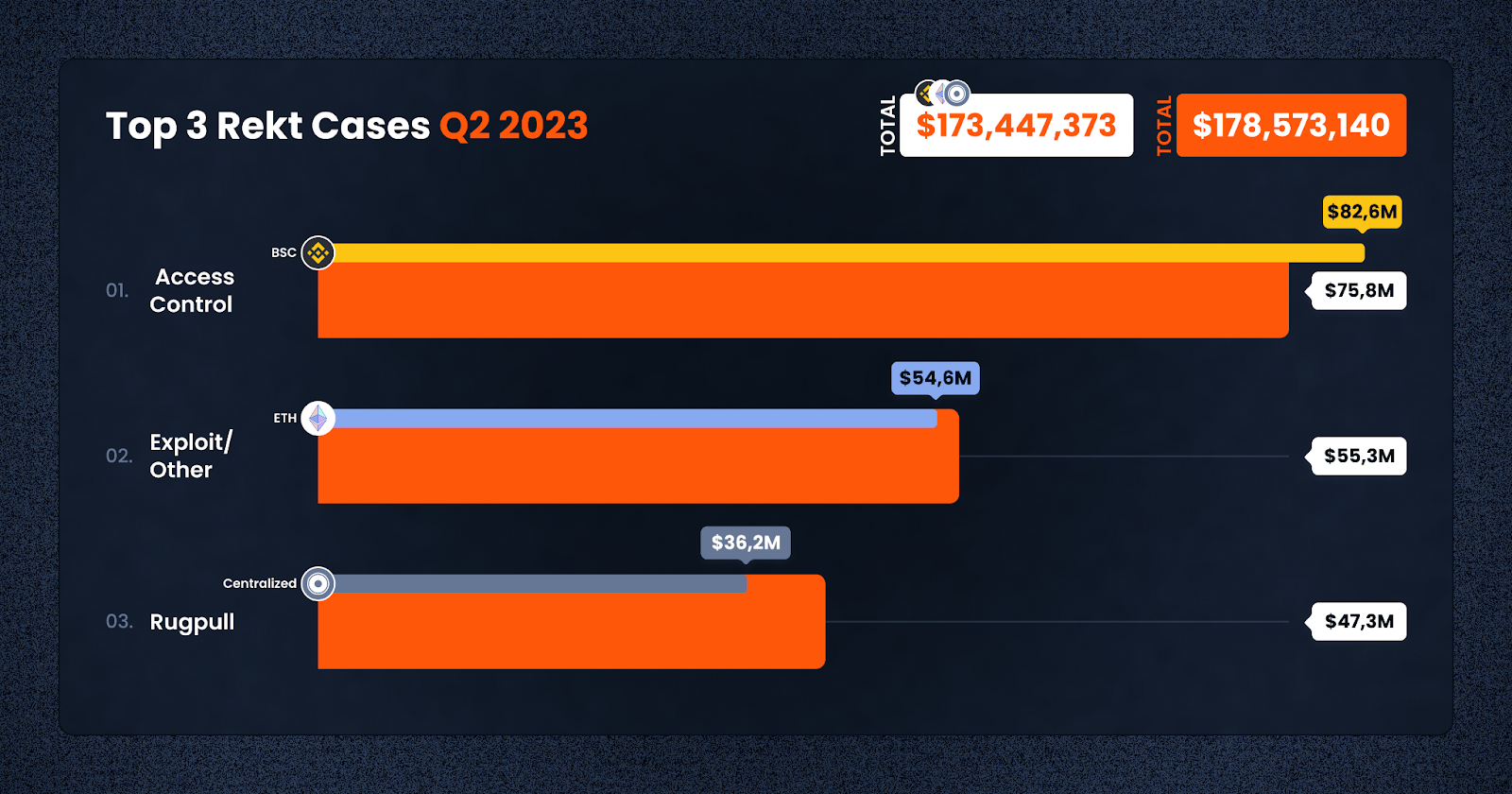
Access control issues made up more than a quarter of all losses at $75.8m. This highlights the ongoing vulnerability in both the CeFi and DeFi sector, as well as the urgency for stronger security measures. Furthermore, we do also see exploits and rug pulls losing users $55.3m and $47.3m respectively, underscoring that smart contract risk and risks posed by bad actors are rampant in equal measure.
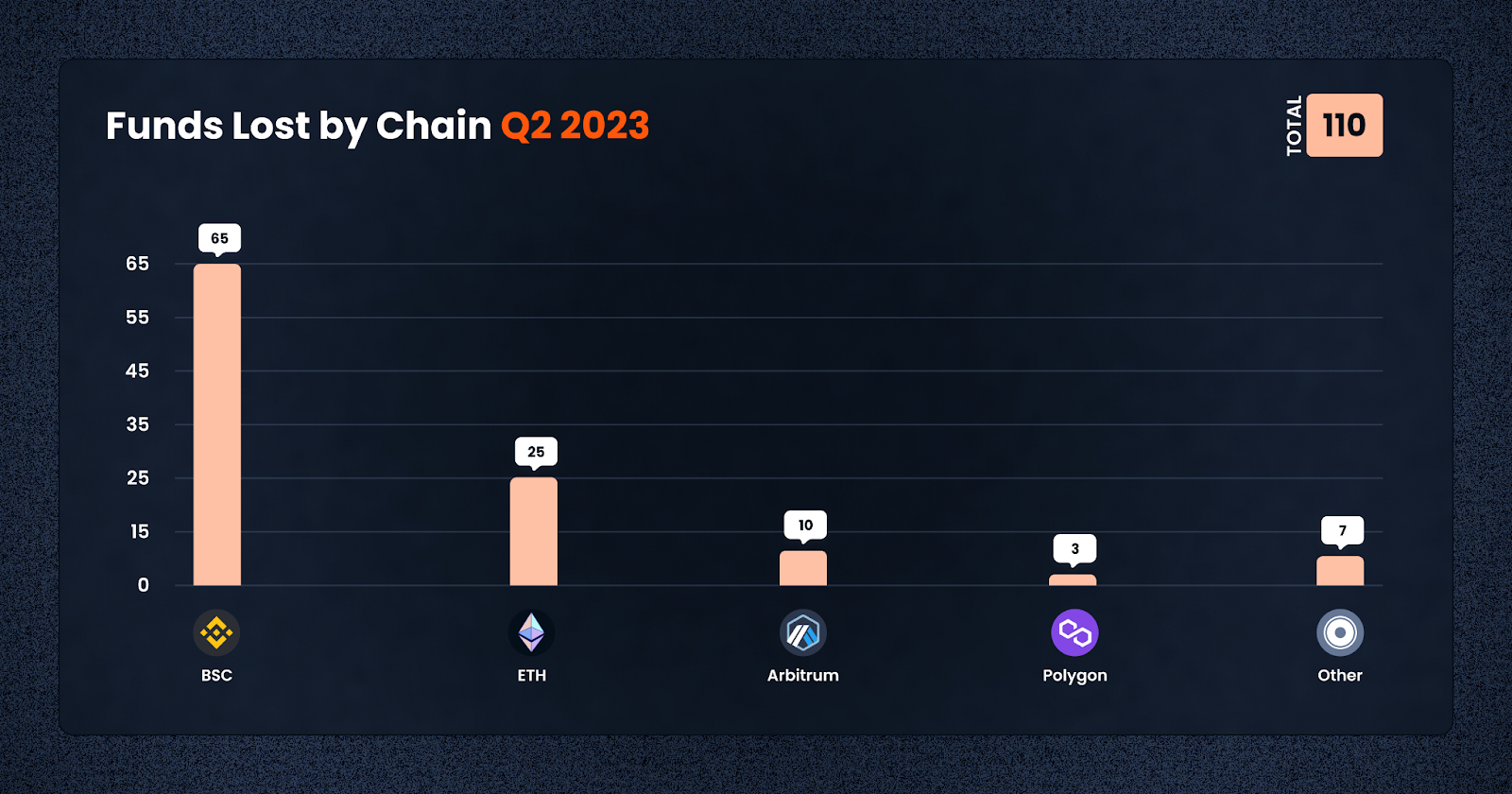
In terms of the blockchain platform, Ethereum (ETH) continues to be a hotspot for fraudulent activities, reporting losses of $82.5m, followed by BNB Smart Chain (BSC) with $57.8m. In terms of frequency, the trophy is still held by the BNB Smart Chain, with 65 cases.
The burgeoning layer 2 platform, Arbitrum, has also attracted attention with 10 cases of losses amounting to $21m.
Types of Exploit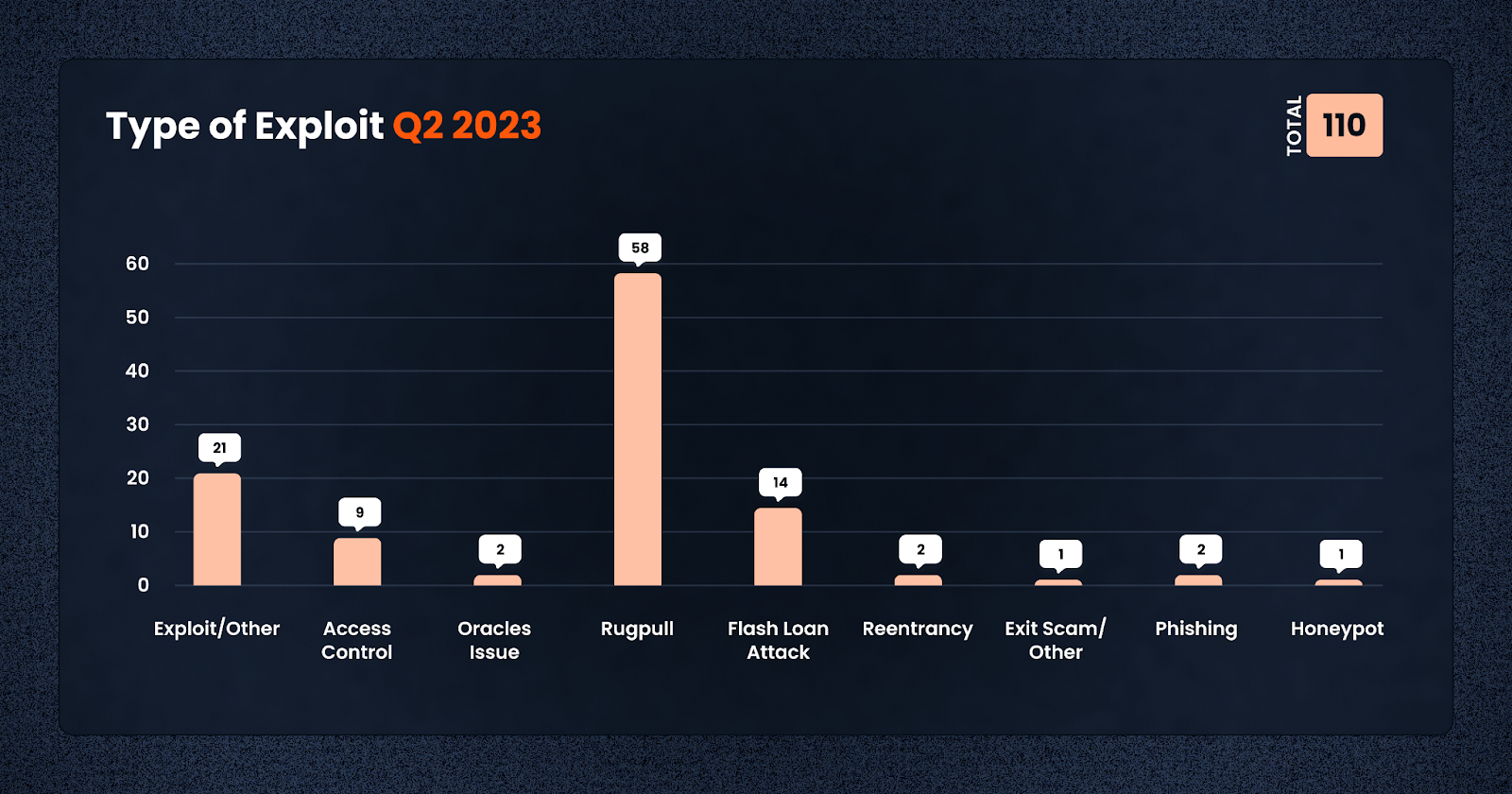
Exploit types varied, with 21 cases linked to other forms of exploits, 55 cases of rugpull, and 14 cases of flash loan attacks. This indicates that the crypto sector continues to face a broad range of security threats that require diverse and sophisticated responses.
Attack Vectors
In terms of attack vectors, Tokens remained the most popular targets, accounting for a whopping 67 cases. Other popular targets include DEXes at 12 cases and Lending Protocols at 9 cases. The burgeoning NFT space also saw 4 cases, underlining the expanding reach of crypto fraud.
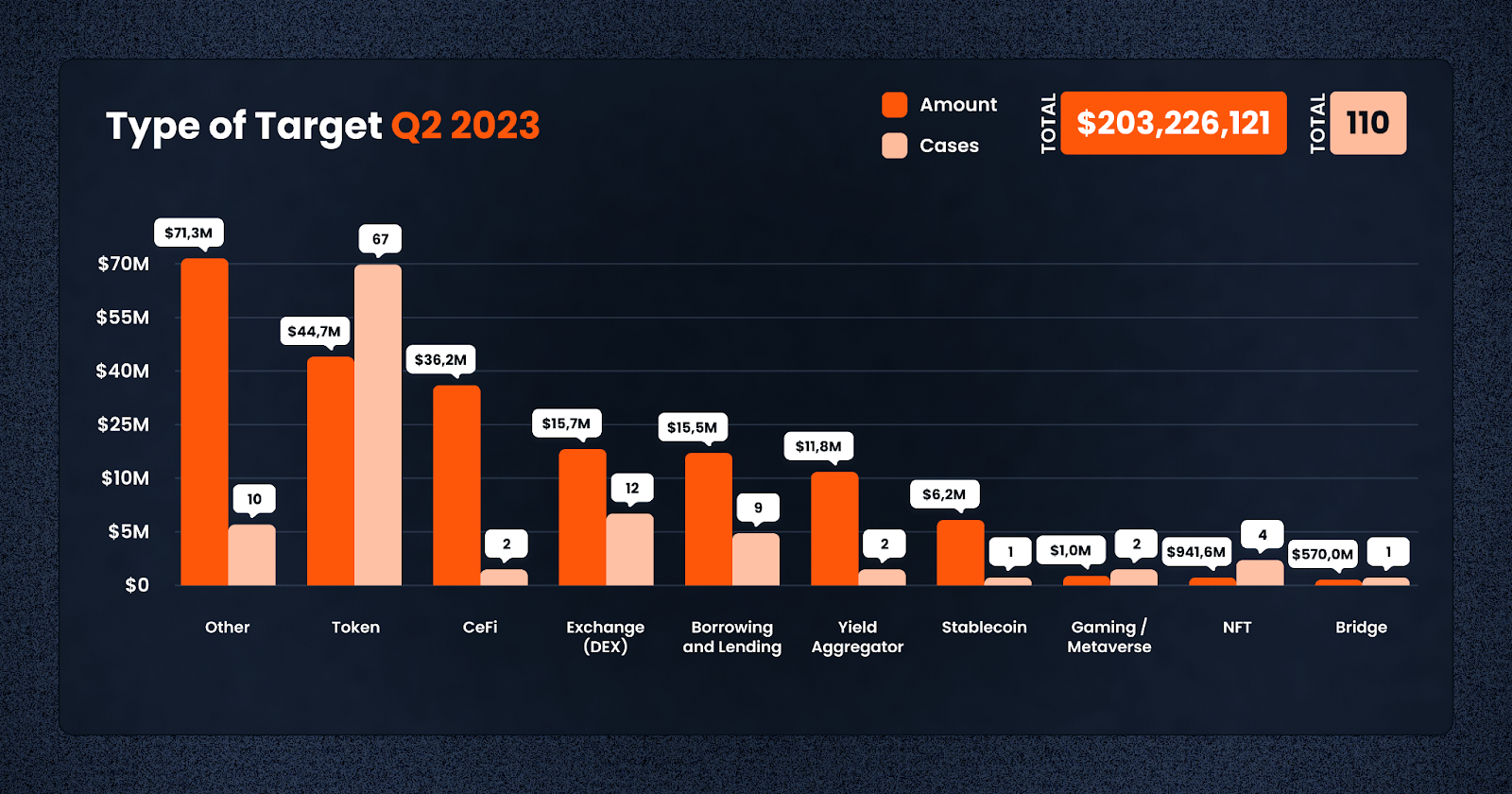
Lending and Borrowing platforms, DEXs, Yield Aggregators, and Centralized Finance (CeFi) platforms were the most severely hit in terms of the amount lost. While the number of cases was relatively small, the significant amounts involved highlight the potentially catastrophic consequences of security breaches in these sectors.
In Q2, recovery of funds remains an area for improvement. The recovered amount of $4.5 million is dwarfed by the total losses, indicating the need for stronger measures to trace and recover stolen funds.
Top Cases This Quarter

On that note, let’s take a brief look at the top cases this quarter.
1. Atomic Wallet — $35m Lost (Access Control, June 4)
A recent exploit has led to the theft of approximately $35 million worth of various tokens. Atomic Wallet, known as a multichain DeFi wallet, fell victim to a breach that allowed hackers to gain unauthorized access and make off with a significant amount of digital assets.
The stolen tokens encompassed a range of popular cryptocurrencies, including Bitcoin (BTC), Ether (ETH), Tether (USDT), Dogecoin (DOGE), Litecoin (LTC), Binance Coin (BNB), and Polygon (MATIC). Of particular note, Tron-based USDT appeared to be the most heavily targeted, with an estimated 7,950,000 USDT stolen, according to on-chain analytics. The stolen funds were predominantly converted into native coins, such as ETH, and held across multiple externally owned addresses (EOAs).
While Atomic Wallet’s official tweet stated that the impacted users represented less than 1% of their monthly active users, it is worth highlighting that the top five users alone lost a staggering total of approximately $17 million. Some affected users reported that their cryptocurrency was stolen following a recent software update, while others claimed to have been impacted despite not having updated to the latest version, as mentioned in messages from Atomic Wallet’s official Telegram channel.
To aid in the investigation, victims have been urged to provide information through a Google Docs form that Atomic Wallet is utilizing. The wallet provider is actively working with on-chain experts to recover the stolen funds, and so far, approximately $1.2 million worth of assets have been successfully rescued from the hackers.
Block Data Reference
Attacker Address Example:
https://etherscan.io/address/0x26208699df4896f09b83993e7c8baad647421b21
https://tronscan.org/#/address/TV92VkrHpim1MN58GNC5RfUWVUmNTPRwGA
Affected Address Example:
https://etherscan.io/address/0x8568ab3AF2E3A1cF3c93dFbCe0D8A3CEE1AcB3dd
Involved Addresses list:
https://www.chainabuse.com/report/b181be45-51a7-446b-83ae-8408c9103bb5
2. Fintoch — $31.7m Lost (Rugpull, May 22)
In the second most significant exploit witnessed this quarter, the Fintoch team orchestrated a rug pull on May 22, 2023, on the Binance BNB Smart Chain. This caused losses amounting to approximately $31.7 million USDT.
The exploit unfolded when the DFintoch project deployed the FintochSTO contract using the deployer address. During the deployment process, 100,000 FTH tokens were minted, and these newly created tokens were subsequently sent to an externally owned address “0xfce4d”. However, on May 22, 2023, a suspicious transfer of 34,341 FTH tokens occurred from address “0xfce4d” to address “0xec1a”.
The rug pull scheme further unfolded as 20,000 FTH tokens were swapped for a staggering sum of 31,666,317 USDT. This conversion was executed using the “swapForUSDT()” function.
The ill-gotten funds, now in the form of USDT, were subsequently moved to another externally owned address. To facilitate the movement of the funds across different blockchains, the scammers employed Multichain and SWFT as bridging mechanisms.
This rug pull executed by the Fintoch team serves as a stark reminder of the risks and vulnerabilities present within the cryptocurrency space. Users and investors must exercise caution, perform due diligence, and remain vigilant when engaging with new projects, especially those lacking in transparency and credibility.
Block Data Reference
Transaction deploying FintochSTO contract: https://bscscan.com/tx/0x3ef479ba75e07ad04f02b5a5f4df476bbbc83bb5d15fdcd2acd1955a4e87fce6
Transaction transferring 34,341 FTH to address 0xec1a: https://bscscan.com/tx/0xee053bf3c429603319d352979e09b207103a08ebf5f42aa0ddd22a9d67f004d6
SwapTx:
https://bscscan.com/tx/0xa5e64161928ee40f6af02a32fc5c1fb9efa05cca6b91d88326279329b71c7ea2
3. MEV Boost — $26.1m Lost (Other, April 2)
The MEV-Boost Relay software, utilized in PoS Ethereum for Proposal/Builder separation, fell victim to an exploit that led to a substantial loss of $26.1 million USD.
The exploit was executed by a malicious validator who took advantage of a vulnerability within the MEV-Boost Relay, subsequently draining funds from five MEV bots.
The attack vector initiated with the exploiter triggering MEV bots to purchase pre-prepared tokens from UniV2 pools. The malicious validator then executed transactions, effectively front-running the bots. When the MEV bots attempted to capitalize on their profits, the attacker manipulated the block by setting both the parent root and state root to zero. Consequently, the altered block, despite being correctly signed by proposers, became unaccepted by the network. This allowed the attacker to extract revealed transactions from deconstructed bundles and claim liquidity from unfortunate MEV bots included in that specific block. The exploited contracts suffered losses of approximately $26.1 million, involving tokens such as WETH, WBTC, USDT, and DAI.
Following the incident, a patch was swiftly rolled out to address the vulnerability. The updated version of mev-boost-relay now refuses to return transactions if blocks are not successfully sent into networks. Additionally, a one-second delay has been implemented before responding with any transaction data, adding an extra layer of protection.
Further investigation into the incident unveiled evidence suggesting that three externally owned addresses (EOAs) funded just 25 days prior were utilized by the malicious actors during the planning and preparation of various token pools. Among the five affected bots, three had their entire balances drained due to automated strategies that worked against them when purchasing tokens, without considering the potential price impact.
It is noteworthy that the stolen funds had been accumulated by the MEV bots over an extended period, as they profited from front-running users. The affected bots themselves fell victim to front-running, rendering this case a counter-exploit, making it particularly noteworthy within the realm of security breaches.
Block Data Reference
Attacker address:
https://etherscan.io/address/0xf489bd7bc0589ae10c6dd7f39eb429f3aace746e
Malicious block:
https://etherscan.io/txs?block=16964664
Contract holding funds:
https://etherscan.io/address/0x3c98d617db017f51C6A73a13E80E1FE14cD1D8Eb
https://etherscan.io/address/0x5B04db6Dd290F680Ae15D1107FCC06A4763905b6
https://etherscan.io/address/0x27bf8f099Ad1eBb2307DF1A7973026565f9C8f69
Draining transaction example:
https://etherscan.io/tx/0xa34d79cbe9aef1bf07692885b353d85912523dfc4662611d33dd09ff6c319c85
4. Bitrue — $21.9m Lost (CeFi, April 14)
Bitrue Exchange, a notable player in the cryptocurrency world, was the victim of a significant security breach on April 14th, leading to the loss of approximately $21.88 million worth of various digital assets from its hot wallet. This considerable sum was stolen in just six transactions over a brief period of four hours, marking it as one of the most substantial single thefts in the sector to date.
The attacker accessed Bitrue’s hot wallet due to an access leak and quickly withdrew the Exchange’s assets into their own private wallet through six transactions within four hours. The stolen tokens, including 318 $ETH, 137,000 $QNT, 46,396,307 $GALA, 172,550,065,266 $SHIB, 756,149,367 $HOT, and 310,071 $MATIC, were then exchanged for $ETH using Uniswap, converting approximately 18,610,517 $USD.
The remaining stolen assets, valued at 3,271,972 $USD, such as $SHIB and $HOT, are still held at the attacker’s address.
Block Data Reference
Attacker address:
https://etherscan.io/address/0x1819ede3b8411ebc613f3603813bf42ae09ba5a5
Affected Hot Wallet Address:
https://etherscan.io/address/0x34d88cee9ed273fc540cd1c219369b26e736731a
Example Swap Transaction:
https://etherscan.io/tx/0x49b03ca12b107c1d84b88634ce90615613b9065cc53be090198f047876d18436
5. GDAC — $14.3m Lost (Flash Loan, April 9)
South Korean cryptocurrency exchange GDAC suffered a significant hack that occurred on April 9th.
The attacker exploited the GDAC hot wallet, stealing an estimated $14.32 million worth of various cryptocurrencies and transferring them to an unknown wallet. Notably, this sum represents about 23% of GDAC’s total assets currently under custody.
The stolen assets included 60.8 Bitcoin (BTC), 350.5 Ether (ETH), 220,000 Tether (USDT), and 10 million WEMIX (WEMIX). The exchange’s monitoring system quickly flagged this activity, leading to an immediate emergency response. As part of its immediate countermeasures, GDAC suspended all deposit and withdrawal services, blocked related servers, and informed the police about the incident.
Additionally, the exchange sought technical assistance from the Korea Internet & Security Agency (KISA) and reported the incident to the Financial Intelligence Unit (FIU). GDAC is working closely with asset issuers, other exchanges, and DeFi managers, urging them to freeze the stolen assets.
GDAC reassured its users, stating that it’s collaborating with various organizations to handle this unfortunate event. The exchange’s swift response and cooperative approach with industry players and authorities highlight the constant challenges faced in maintaining the security of digital assets in the rapidly evolving crypto world.
Conclusion
To sum up, while Q2 saw a decrease in the overall losses compared to the same period last year, the diversity of exploits and attack vectors highlight the persistent and evolving challenges in crypto security. As the sector continues to grow, ongoing efforts to strengthen security measures and increase recoveries will be essential.
The considerable financial setbacks experienced this quarter highlight the importance of enhanced risk assessment and caution in DeFi investments. It is essential for investors to familiarize themselves with potential threats and establish safeguards for their investments. At De.Fi, we recognize the need to assist in navigating the complex and ever-changing DeFi landscape. Therefore, we pledge our commitment to providing our users with essential tools to make educated decisions within this industry.