DeFi Rekt Report October 2025: $38.6 Million Lost Across 9 Exploits
October 2025 saw a total of $38.63 million lost across nine distinct security incidents in both centralized and decentralized platforms.

Crypto phishing scams are some of the most prevalent attacks in the industry. They are so common that even Ethereum founder Vitalik Buterin’s Twitter account has been subject to a phishing attack due to a hacker gaining access to his profile:
🚨 ALERT 🚨@VitalikButerin Twitter Profile was compromised with a phishing link, posted in the last tweet
— De.Fi 🛡️ Web3 Antivirus (@DeDotFiSecurity) September 9, 2023
⚠️ DO NOT interact with any links until further confirmations from his side pic.twitter.com/PYrA3rzNYq
Due to the severity of these attacks should you fall victim, learning how to recognize a phishing scam and how to protect your DeFi wallet from being compromised is crucial knowledge for every crypto user.
In this blog, we’ll outline what crypto phishing scams are, how they work, and how you can avoid getting REKT with the De.Fi antivirus security suite.
Crypto phishing refers to when bad actors use social manipulation to obtain sensitive information from victims. This can include the sharing of a wallet’s private keys or tricking the user into completing actions like interacting with a malicious smart contract or fake versions of famous dapps.
The most frequent ways scammers execute crypto phishing scams are:
Now let’s take a closer look at the actual technical process behind token approvals and signing messages with your wallet. Because these are the actions phishing attackers try to push users towards, knowing how they work will help you be prepared for mitigating a scam.
One thing that’s important to remember regarding token approvals is that they are relevant not only in the context of phishing but also for all DeFi scam types.
To interact with any dapp, you need to provide token approvals with the right to spend underlying tokens from your balance. In other words, you have to approve a contract operated by the dapp to be a spender of a particular ERC-20 token.
How does this work from a technical perspective? Let’s say you are about to deposit USDC into a vault. A typical deposit function should involve transferring the staking token from your balance to a strategy bound to the vault so that yield can be generated on the deposited amount. This is done by calling the transferFrom() function – a standard function each token based on the ERC-20 standard has.
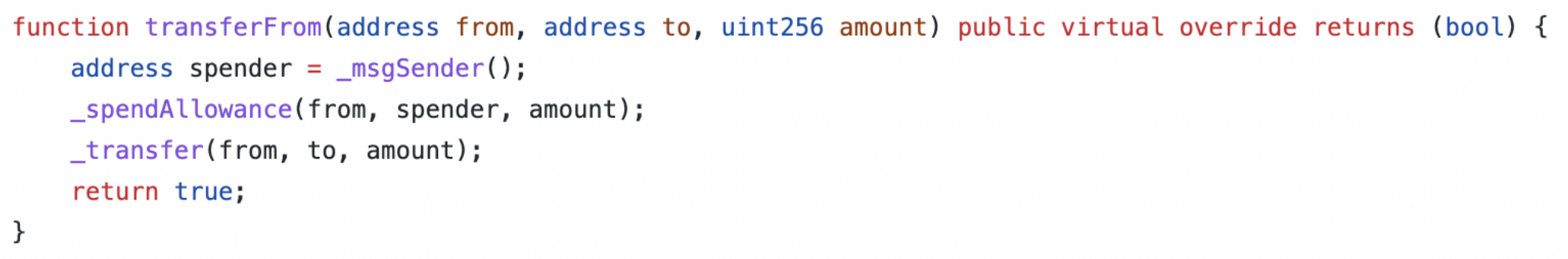
https://github.com/OpenZeppelin/openzeppelin-contracts/blob/master/contracts/token /ERC20/ERC20.sol
But only contracts approved by you can call a token transfer from your balance. Thus, before depositing, swapping, lending, placing buy/sell orders, or calling any other functionality that should send your tokens to a particular target, you have to call the approve() function on the contract of the token.
See the approve() call within the Solidity code below:
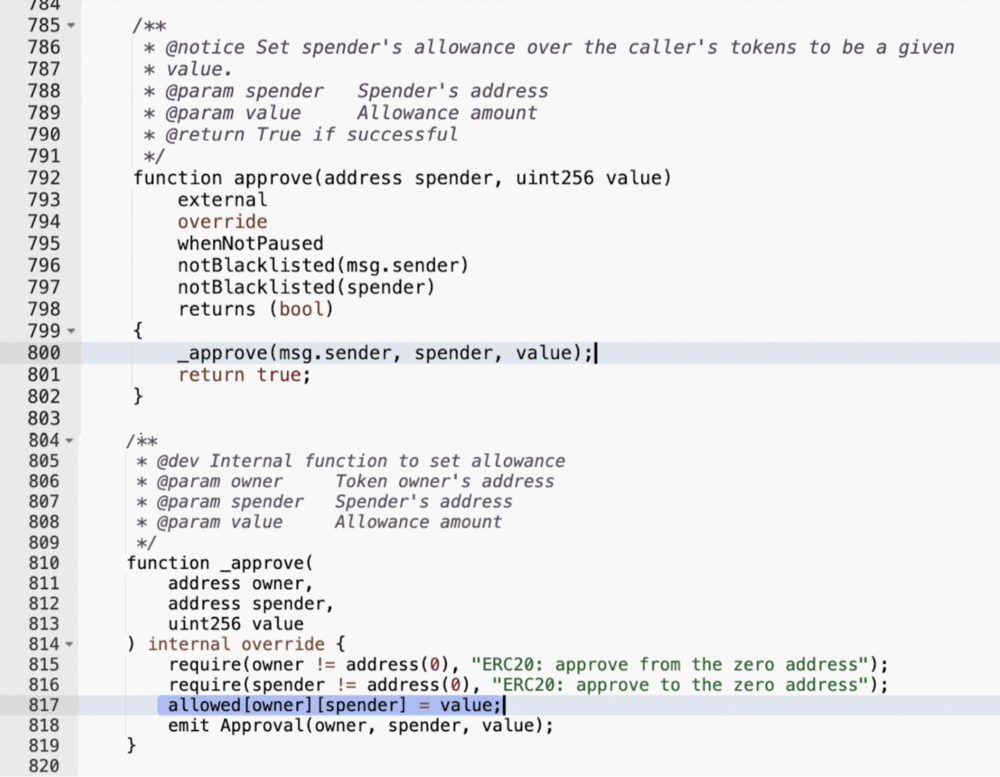
https://etherscan.io/address/0xa2327a938febf5fec13bacfb16ae10ecbc4cbdcf#code
In the image above, the owner parameter would be your address. “Spender” is the dapp contract that should call transferFrom() later on when deposit() is called.
To manually check if you’ve approved a contract to spend your tokens, you can open the Read section of the ERC-20 token contract and input your address and the dapp contract address into the view function “allowance”. It will show you the approved token amount:
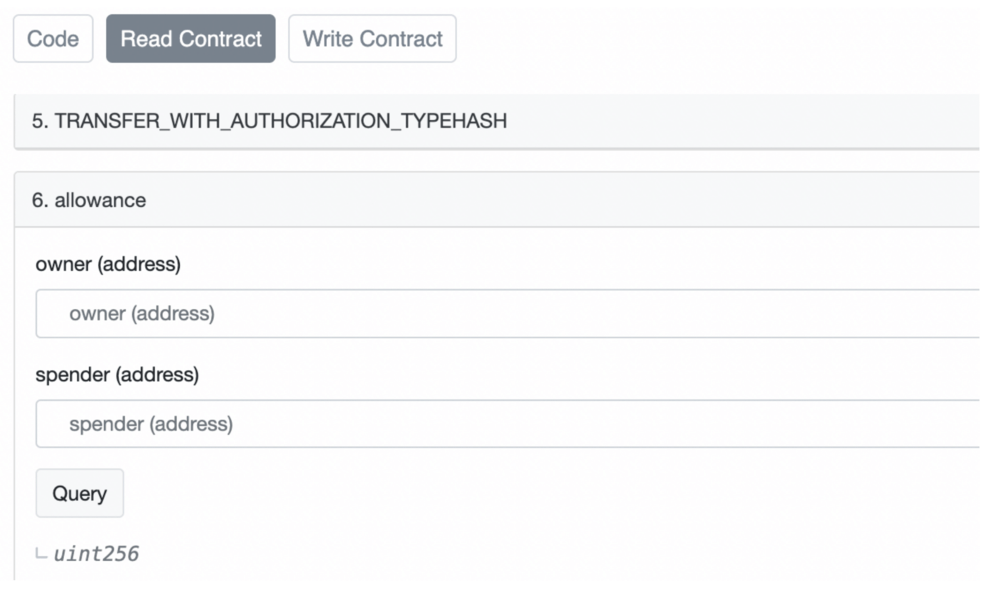
https://etherscan.io/token/0xa0b86991c6218b36c1d19d4a2e9eb0ce3606eb48#readProxyContract
Now you can see that contracts with your approvals for specific tokens have control over your balance of those tokens.
Even worse, most dapps prefer to request unlimited token approvals from users so that they don’t have to call approve() repeatedly. While this is convenient and gas efficient, doing this leaves users exposed to a high level of risk.
If you’ve approved a malicious contact to be an unlimited spender of a token, your entire balance will likely be wiped out nearly instantly after the approval is confirmed.
There are also risks from having unlimited token approvals in place for a contract that has a vulnerability and can get hacked. Hackers may find a way to transfer all tokens from users who have previously approved their balances to the breached contract.
With all this said, we strongly recommend keeping an eye on all approved contracts your wallet has collected. And doing so is just a few clicks away via our DeFi dashboard.
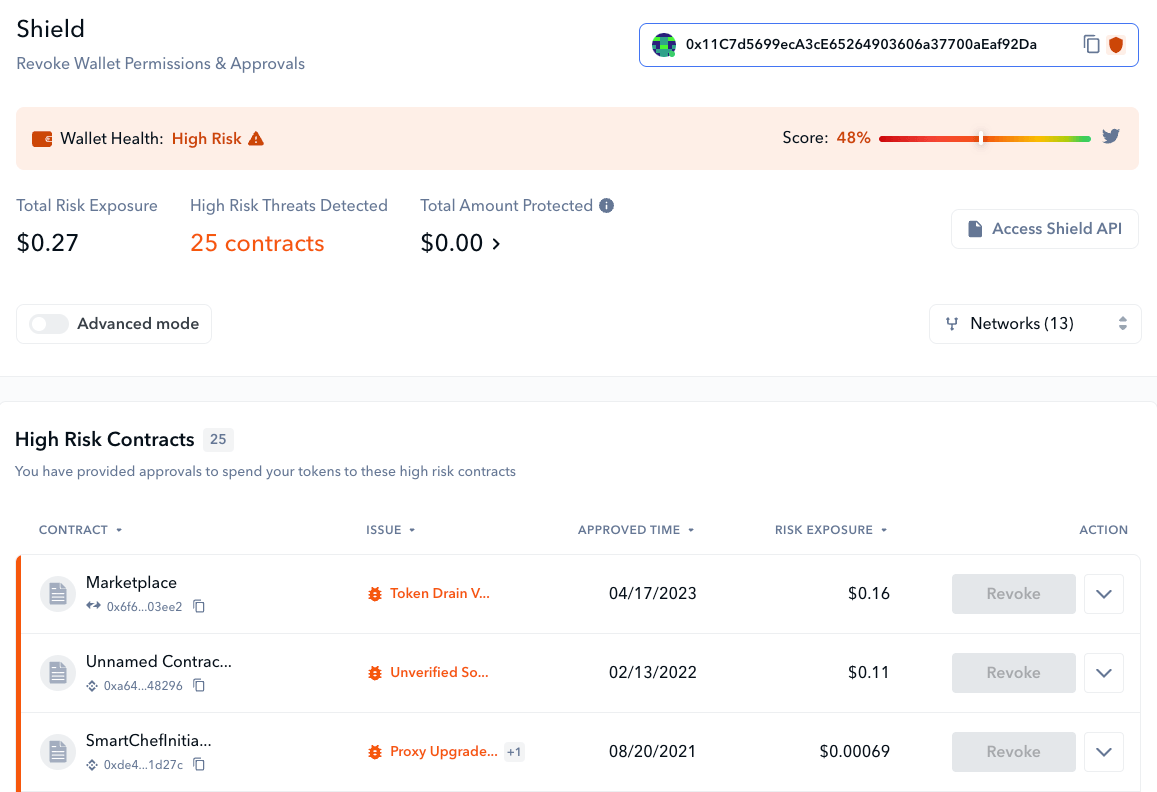
Shield’s interface lets you revoke permissions with a click
The De.Fi Shield is the best solution for scanning and revoking wallet token approvals. Shield scans all your approved contracts for over 80 security issues, highlighting potentially critical risks such as the possibility of a token balance drain via ERC-20 approval.
Even if you’ve used a contract that appears to not be malicious, if you are not going to interact with it regularly, it may be worth revoking related token approvals. Scammers can exploit any contract unexpectedly. Why risk your balance if you don’t have to?
If you’re into DeFi, you’ve probably come across a process that requires you to sign a message as a part of verifying access to dapps, DAO voting, placing sell/buy orders on DEXs or NFT marketplaces, etc. Cryptographic signatures are a perfect solution when transactions must be authenticated but when users and dapps would rather not trigger needing to spend gas.
What happens under the hood is that the user receives message data and, with their private keys, they confirm that they have received that data and authenticate it. In other words, signatures allow dapps to link the data of a message to a user’s public key with the guarantee that a message was signed by the public key’s corresponding private key.
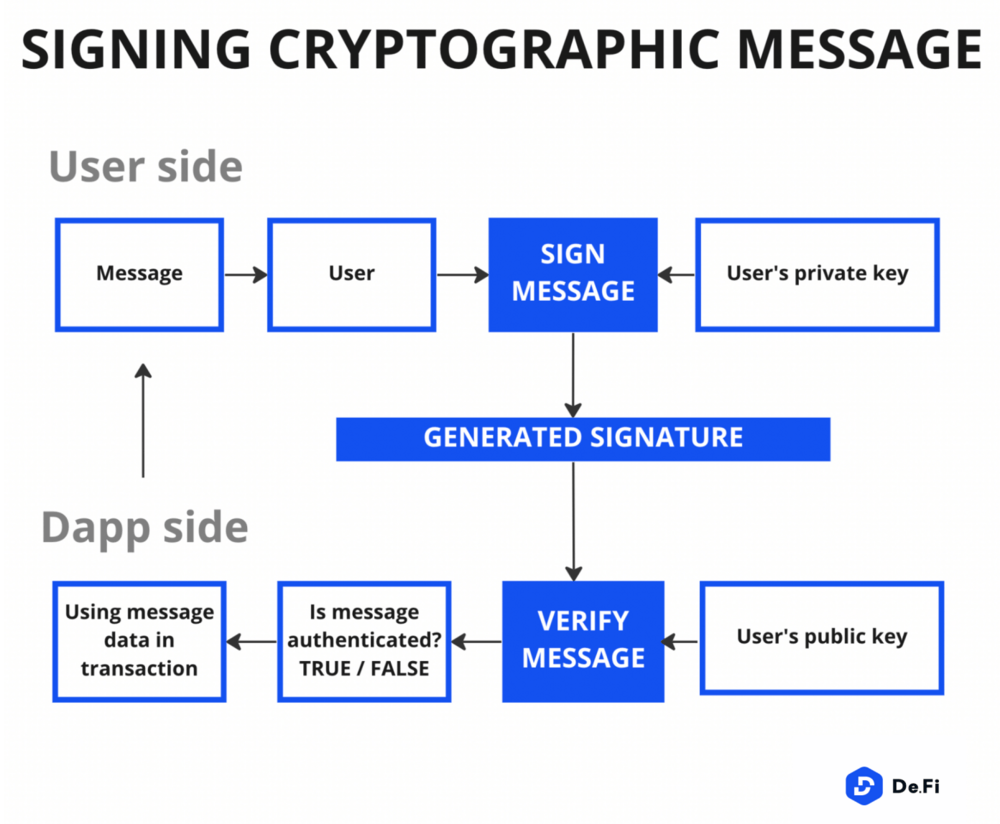
It is important to note that private keys cannot be derived from signatures. This means that it is a safe mechanism to use overall. However, that is entirely dependent on whether or not users understand what they are signing. If they don’t, there is a big chance that scammers will take advantage of their misplaced trust.
Some signature methods can be unreadable as they deliver data in a hashed format. Instead of readable text, users get a set of symbols like this:
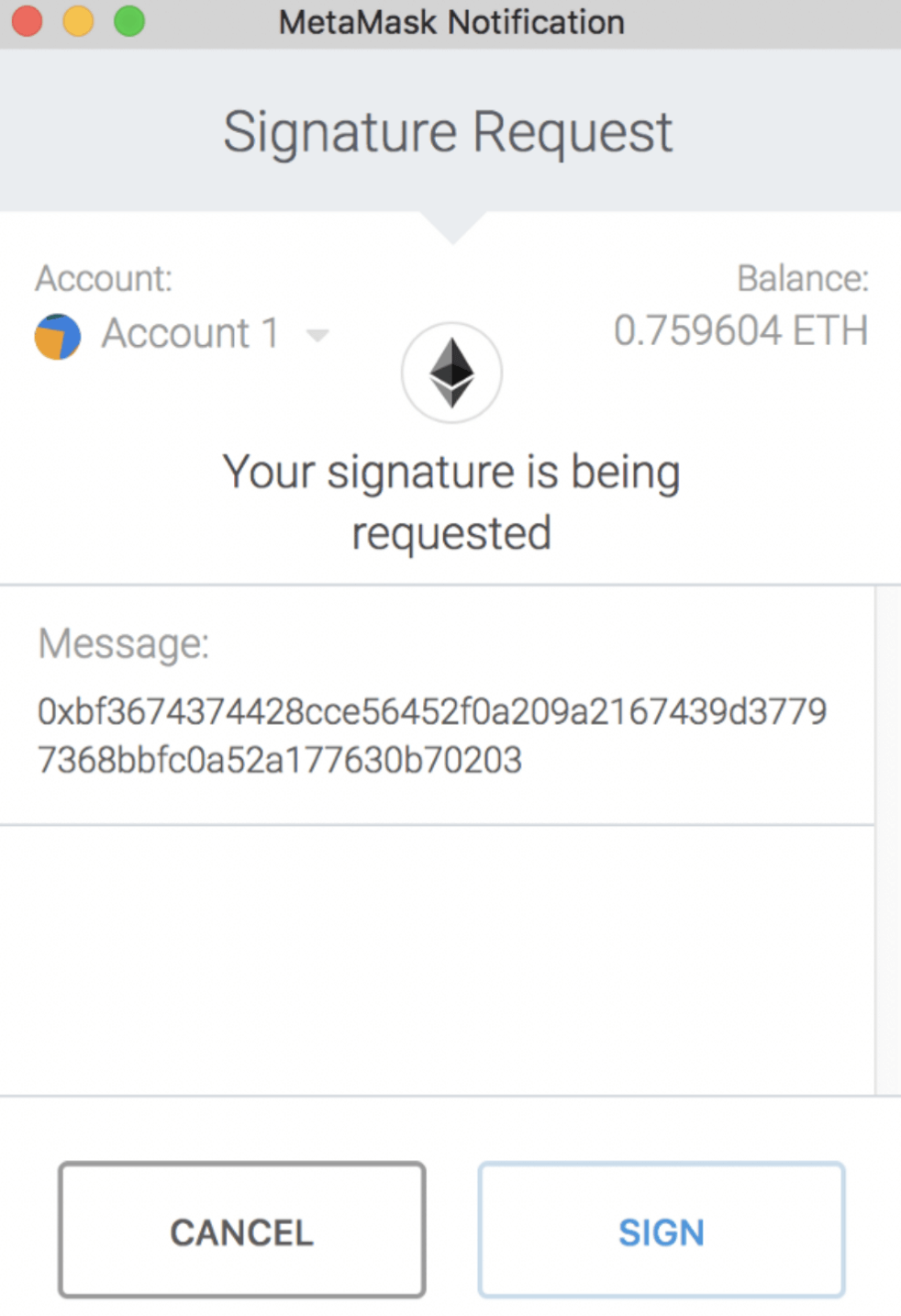
But even when dapps use signature methods providing comprehensible message info such as EIP-712, where data in the message is shown in a human-readable way, many users still might not understand what certain parameters mean and fall prey to scammers.
OpenSea has been using the EIP-712 message method since the protocol migrated to Wyvern V2 and the currently valid Seaport contract. Why are we mentioning OpenSea now? One of the biggest phishing scams ever happened to OpenSea and was performed exactly by prompting victims to sign cryptographic messages.
The malicious actor sent emails to OpenSea users, which contained information about a fake migration to a new contract. As a result of this phishing scam, 17 users lost NFTs valued at around $1.7M USD.
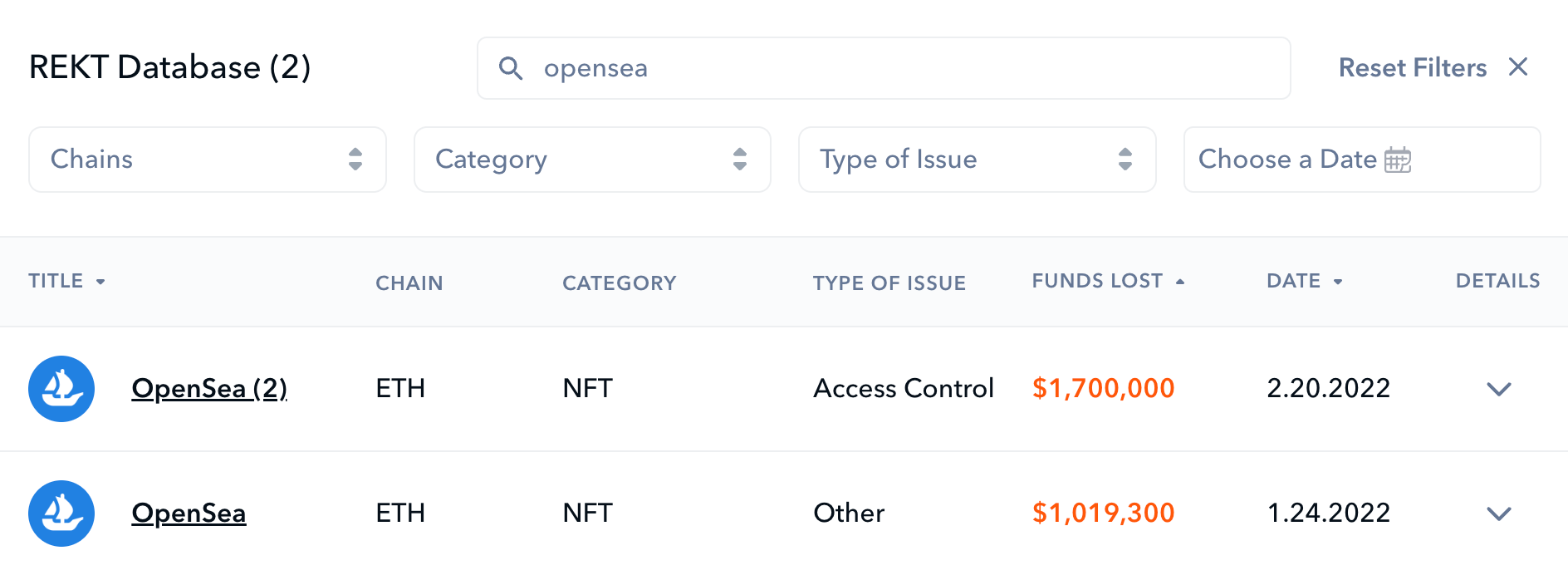
You can research background info on all OpenSea exploits via the REKT Database
Let’s analyze how it happened so that you understand the importance of signing messages and avoid similar scam patterns.
The fact that message data is linked to a public key is decoded via a target contract function. On OpenSea, this decoding happens when an order gets executed. When a seller creates a sell order, they have to go through two steps:
For buy orders, the flow is similar. The buyer has to approve WETH to OpenSea so that the marketplace can transfer the purchase amount from the buyer’s balance to the seller’s wallet once the order match happens.
This may be surprising to some but, yes, OpenSea orders are essentially created offchain. Otherwise, it would be overly expensive to create, change, and cancel them due to gas costs. The order execution itself, of course, must be paid by the transaction finalizer – a user accepting a buy or a sell order. But until the order is executed, it can be canceled for free.
The signature generated from the seller proves that their public key is linked to the order and the order parameters are accepted from them. And this is where the scammers phishing on OpenSea snuck in.
The scammers exploited the fact that orders can be created outside of the OpenSea platform and can still be read by the original OpenSea exchange contract. Using phishing emails, they navigated users to requests to sign an order message, in which the malicious price parameter was embedded.
Not realizing what was happening, the victims confirmed the messages with their private keys that they were ready to sell their NFTs for 0 ETH. These orders with the 0 ETH price were successfully processed by the OpenSea exchange contract, passing all underlying assets from the deceived users directly to the scammer.
Now you know the possible consequences of signing messages you don’t understand and don’t double-check. The same fake message pattern can be applied by scammers for limit orders on DEX platforms as well. They can trick users into selling their ERC-20 tokens for little to nothing. Always beware of what you are signing!
Oftentimes, phishing goes hand in hand with fake airdrops. Because everyone loves the prospect of receiving a lucrative crypto airdrop, many users will let their guard down when one appears to be available.
If you suddenly detect new tokens in your wallet, don’t jump for joy or rush to swap them for some other token. What many don’t understand is that this “sudden gift” can be a fake airdrop. This is a scam technique where fake tokens imitating legit, trusted tokens, are sent to unsuspecting users.
When executing fake airdrops, scammers want you to interact with their malicious contracts. This will allow them to eventually take control of your funds.
To understand how dangerous it can be, let’s examine a fake UNI airdrop that happened in July 2022. Scammers sent fake Uniswap LP tokens to 73,399 Uniswap users and promised they could be redeemed for the actual UNI token.
When sending their malicious LPs, the scammer also utilized the event pollution technique: event data of the attack transaction was set in such a way that block explorers identified the “from” parameter as the real “Uniswap V3: Positions NFT” contract.
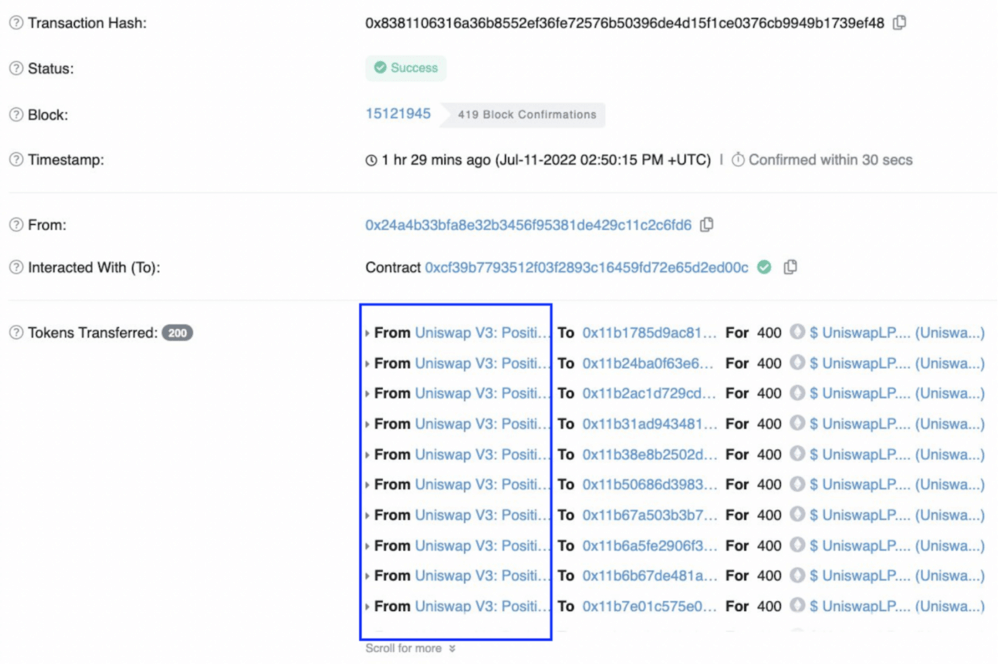
Unfortunately, a large number of users believed the airdrop was legitimate and clicked on the “UniswapLP” token received. The token name had a link redirecting to a domain called “uniswaplp.com” imitating the real Uniswap website. Users could see a claim button once they visited:
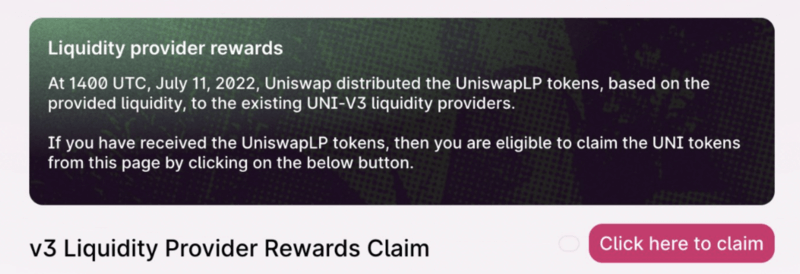
Upon clicking it, the phishing site asked users to confirm an approval transaction that gave the scammer access to all of their real Uniswap V3 LPs. These LPs are the tokens used to withdraw assets provided as liquidity for yield farming.
The attacker was able to drain these Uniswap LPs from any users who signed the phishing transaction. Then they laundered all stolen funds via the privacy mixer Tornado Cash.
Similar schemes were used for fake airdrops performed on Bored Ape Yacht Club NFTs, ThorChain’s RUNE, Optimism’s OP, and many other famous tokens.
Want to avoid the REKT Database’s next crypto hack and scam entry? Remember the notes below based on what we’ve discussed in this blog:
Finally, we highly recommend following the De.Fi Security Twitter account. While we can’t keep this blog up-to-date with every new phishing technique, emerging trends are always shared via the Twitter account first to keep our loyal followers informed:
🚨 Scam Alert 🚨
— De.Fi 🛡️ Web3 Antivirus (@DeDotFiSecurity) August 23, 2023
⚡️ A NEW Type of URL spoofing Scam on Google!
Scammers are purchasing ads for crypto websites with valid URLs.
When users click, they’re redirected through an ad, which then diverts them to a scam site.
Stay Vigilant, and never visit sponsored crypto… pic.twitter.com/bc0QuN94jF
While crypto phishing scams can be dangerous, don’t let them scare you away from getting the most out of DeFi. With the right tools by your side and a little common sense, you’ll be able to seamlessly avoid attackers while navigating this exciting new industry.
October 2025 saw a total of $38.63 million lost across nine distinct security incidents in both centralized and decentralized platforms.
The third quarter of 2025 marked yet another turbulent period for the DeFi and wider crypto ecosystem, with $434,124,000 lost to exploits, scams, and security failures across both centralized and decentralized platforms.
June 2025 witnessed another alarming month for Web3 security, with a total of $114,768,000 lost during 11 separate attacks
May 2025 saw both DeFi and CeFi security once again under attack, with $275,953,000 lost across just 8 recorded incidents
April 2025 witnessed a large escalation in exploit volume and value, with a massive $5,919,684,000 being stolen in 10 confirmed events.
Q1 2025 marked one of the worst quarters in blockchain exploit history, with total recorded losses topping $2,052,584,700 across 37 incidents
© De.Fi. All rights reserved.