DeFi Rekt Report October 2025: $38.6 Million Lost Across 9 Exploits
October 2025 saw a total of $38.63 million lost across nine distinct security incidents in both centralized and decentralized platforms.
The crypto market continues to trend toward a more onchain world, and many believe that the next bull run will primarily be focused on trading that happens within the confines of the DeFi universe.
This is exciting because many users will no longer need to worry about the trust issues of primarily trading on centralized exchanges. DeFi allows for the self-custody of crypto assets and benefits from the liquidity that flows freely amongst an open ecosystem of dapps and interconnected blockchain networks.
However, with this freedom comes an increase in the personal responsibilities of users. Trading onchain means there is a constant risk of interacting with smart contracts that may hide vulnerabilities or malicious code.
Since many traders lack the technical understanding regarding how to read smart contracts, this leaves them with a dilemma. Avoid DeFi wallet scams by passing up opportunities to invest in new and exciting tokens? Or capture the upside of trending new projects while accepting an increased risk of rug pulls and honeypots?
Luckily, there are now tools available that allow even the most tech-averse crypto trader to quickly analyze the potential risks of tokens. Today we’ll examine the role that token security detectors play within the DeFi ecosystem and show you specific case studies where the De.Fi Scanner token security detection tool could have been used to avoid risky investments. If you’re looking to stay safe without lowering your exposure to the most exciting new projects, this blog is for you!
A token security detector is a tool used to analyze specific token smart contracts. Standard DeFi tokens all have a corresponding contract address used to govern their specific token functions. Token security detectors analyze the rules within these contracts to find signs of exploit risks.
No two token security detectors are the same, but generally, they look for issues that have commonly led to onchain scams in the past. Here at De.Fi, we’re experts in the history of crypto hacks and scams. This led us to develop what we consider to be the most comprehensive token security detector available today: De.Fi Scanner
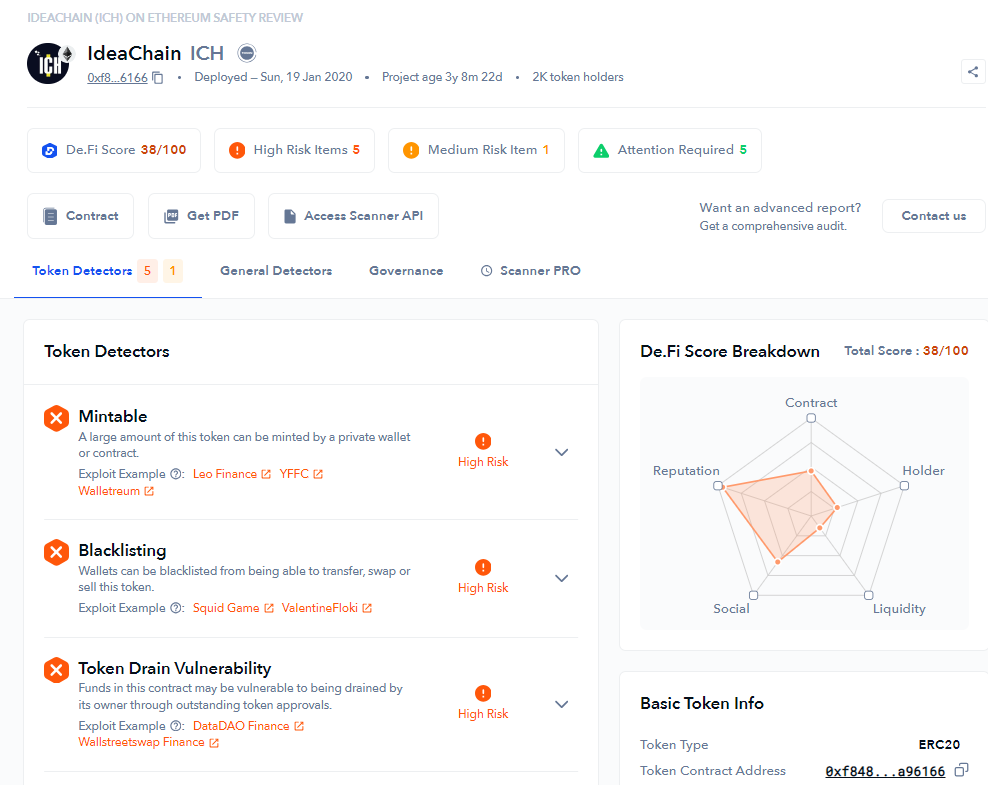
The De.Fi Scanner results page
Scanner is the result of the lessons we’ve learned via years of fighting onchain treacherousness. Its unique set of features include:
Want to see how a token security detector works in action? Check out the walkthrough video below from our YouTube channel:
Token security detection features are robust, which means first-time users can sometimes be intimidated by the amount of information they receive. To learn how De.Fi Scanner results should be interpreted, let’s walk through a few case studies of token rug pulls that users could have avoided by performing a quick smart contract scanner audit.
Note: The examples below were all originally published via our De.Fi Security X profile. Follow this account on X if you always want to stay up-to-date on the latest DeFi security incidents.
Gandalf The Grey was a rug pull project, resulting in a loss of 141 ETH for token holders, equating to ~$270,000 USD, through liquidity removal. The ERC-20 token, GAN, was trading on Uniswap when the token deployer removed liquidity from the pool. Stolen funds were then transferred through several EOA addresses. In addition, parts of the stolen funds were distributed via CoinTool, adding another layer of complexity to the scam.
Some of this tragic loss of funds could have been avoided by users utilizing token security detection features. This is De.Fi Scanner’s initial report regarding the project at 2 days old:
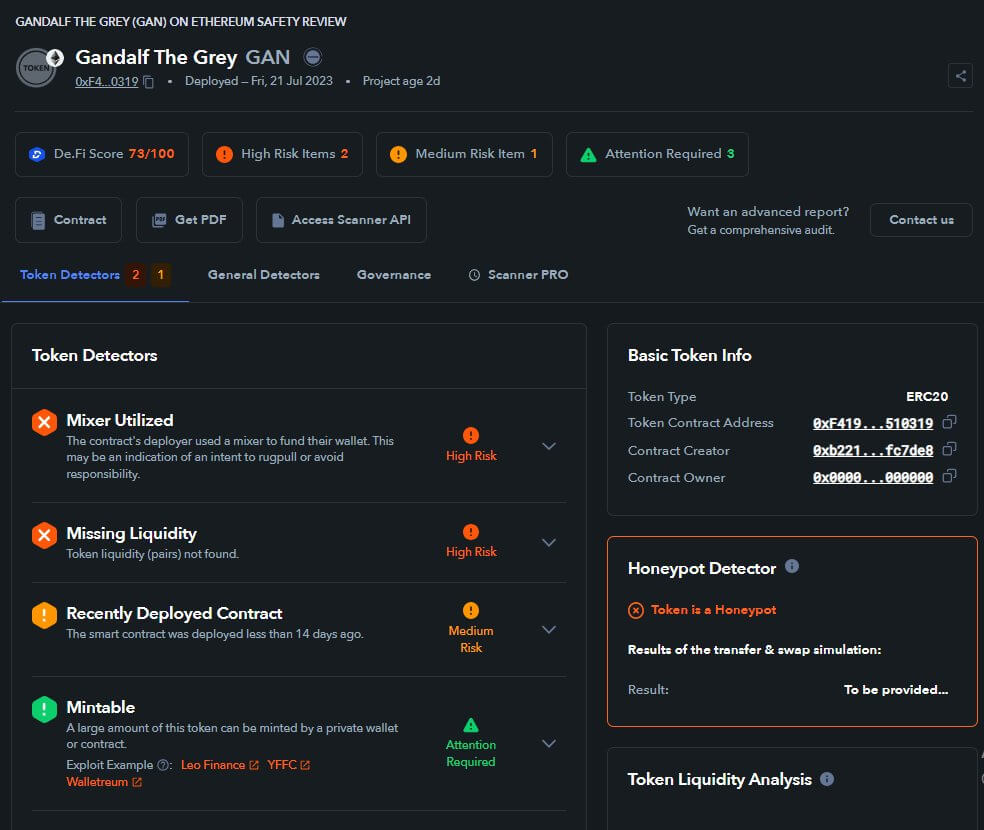
As we can see, there were numerous red flags. The first red flag was that the project was funded via Tornado Cash, an Ethereum mixing service that allows users to anonymously send transactions. This was identified via the “Mixer Utilized” warning. Scammers will sometimes use Tornado Cash when funding a scam token because it helps them cover their tracks once the exploit is completed.
The second red flag was that Scanner clearly labeled the token as a honeypot. Scammers design honeypot smart contracts in such a way that your funds are essentially trapped. Selling or trading these tokens is impossible due to their design which leaves your investment stuck indefinitely.
The third red flag was that the contract was recently deployed. Many new users don’t know to check this item, but it can be a vital warning sign to avoid risky contracts. In general, the newer the token contract is, the higher the likelihood that a token could be a scam since most nefarious actors are trying to make quick cash and won’t put in the time and effort to run a project long-term.
People’s Bitcoin was a token that quickly gained steam and then plummeted in value twice as fast. The coin’s now-defunct X profile described it as “A community experiment in true decentralization. A second chance for many, a first chance for most”.
The X profile was almost completely used for sharing memes, and the coin had a profile picture in the style of the popular HarryPotterObamaSonic10Inu which also happens to share the ticker $BITCOIN. This was likely a ploy to associate People’s BITCOIN with the more trusted HPOS10Inu brand and it is a common tactic used by scammers. They will use traits of coins that people know and trust to lure them into a shady investment.
Beyond questionable marketing, the De.Fi Scanner also provided clear warning signs for anyone researching the coin:
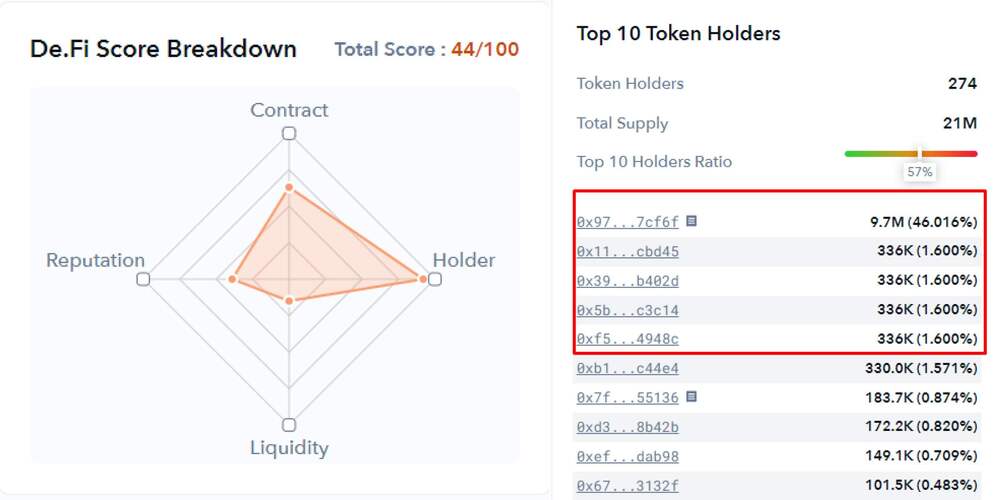
This report focused on the Top 10 Token Holders data. We include this data because a concentration of a large number of tokens within a small group of wallets is generally a leading indicator of high dumping risks. The analysis of People’s BITCOIN showed four wallets all having the same amount of tokens (336K), which meant there was most likely one owner trying to obfuscate the true size of their portfolio.
Other red flags were issues around low liquidity (which can lead to high volatility or loss of swap functionality), transfer fees (the contract tax can be modified and increased up to 100%), and the fact that the contract had been recently deployed.
The individuals behind People’s BITCOIN used fake volume to get the token trending on popular DEX analytics apps, then waited for real users to begin accumulating the token. Once buys started coming in, the owner started selling their tokens through alt wallets. The result was a massive -99% drop in price over the next 24 hours:
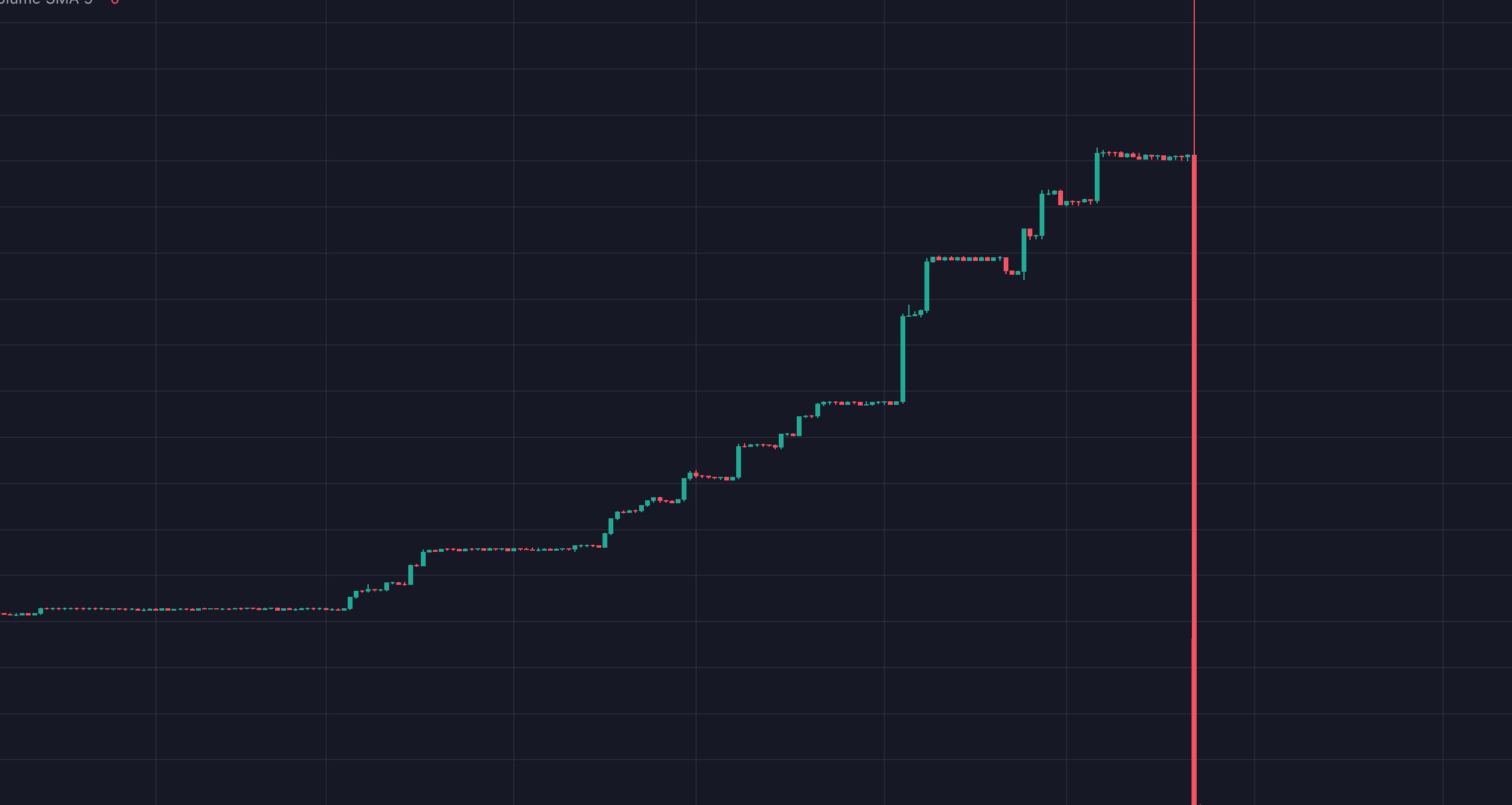
Google GPT AI ($GAI) was a token launched on Coinbase’s BASE chain. As the network is relatively new, many users are searching for freshly launched tokens that have high long-term potential. This leads to a lucrative environment for scammers. GAI was able to attract $2m+ in volume, but the price was down -100% just hours later. Even worse, some buyers of this token also lost other assets in their wallets. Let’s investigate what happened.
With an initial inspection, potential buyers would have seen numerous red flags via Scanner:
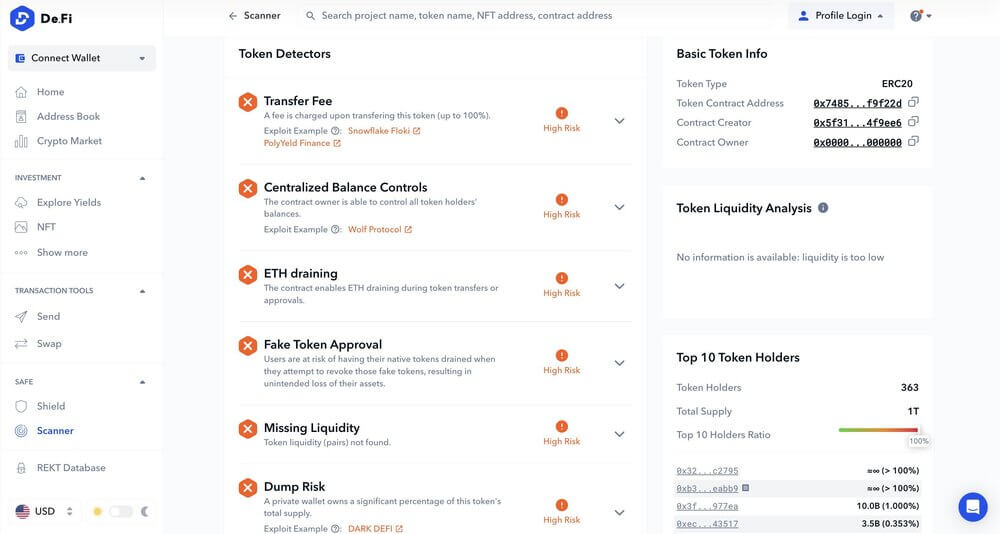
The results went beyond even basic risk markers and also included malicious ERC-20 allowances that other security detectors sometimes miss. Here’s the entire report of what we found:
The token holder report was also critically important for GAI analysis:
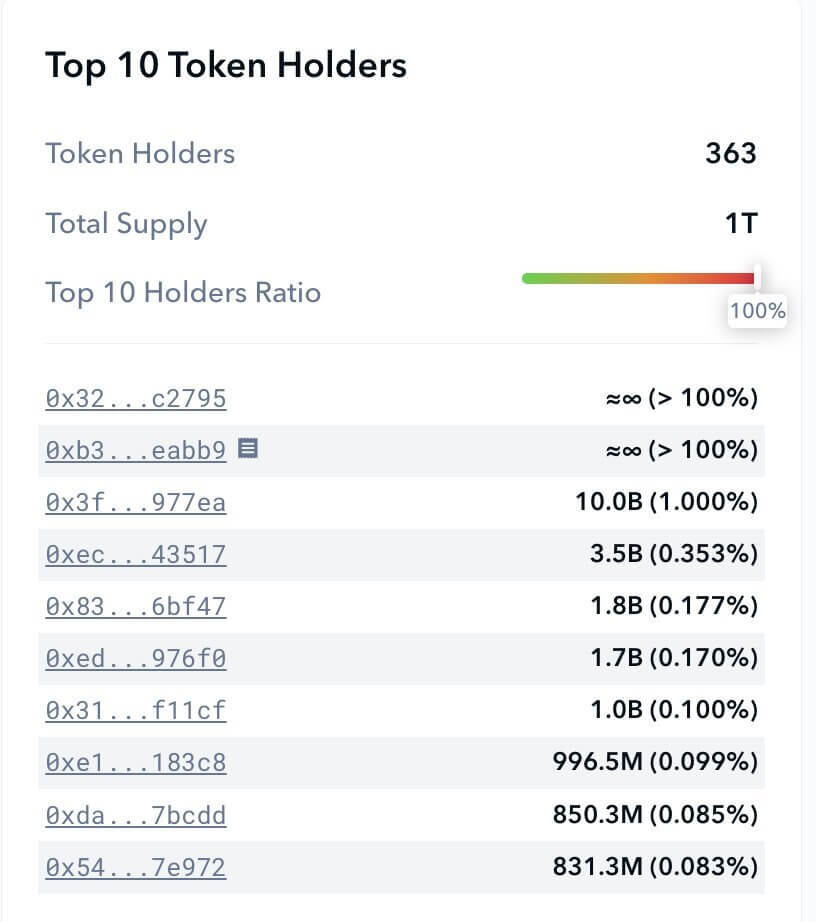
You could see from the token holder distribution that the top 4 wallets accounted for roughly 90%+ of the total supply. Put together, analyzing in advance would have illustrated the huge rug pull risk.
The above cases are only a small illustration of the numerous risks crypto traders deal with daily. This is why we are so passionate about our De.Fi Antivirus suite and the free tools it puts in the hands of all web3 users.
Beyond Scanner, we also offer De.Fi Shield, an easy-to-use wallet permissions tracker + removal tool. Shield automatically runs security detectors for each contract, token, and NFT approval that the user has in their DeFi wallet. High-risk tokens and smart contracts are identified with detailed descriptions of the potential risk. The whole process happens in only a few seconds!
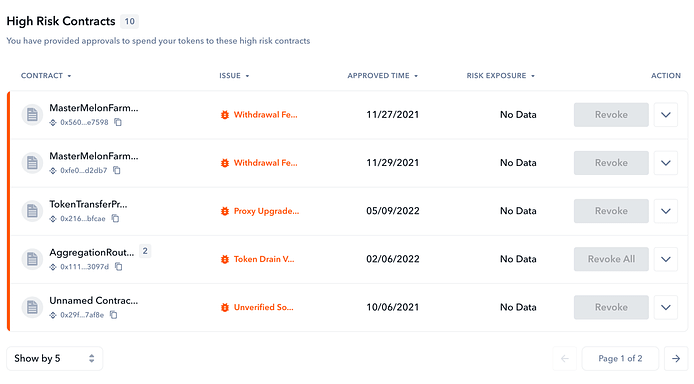
After analyzing your wallet, you can quickly revoke all allowances or selectively choose based on your personal risk preference. Together, Scanner and Shield allow you to cover your bases both before and after you interact with a smart contract.
For users who want to see security analysis for a large number of tokens at a glance, we’ve also recently released our Market Security tool. Now you can view safety data for tokens at a glance in the same way you can with market cap and volume data:
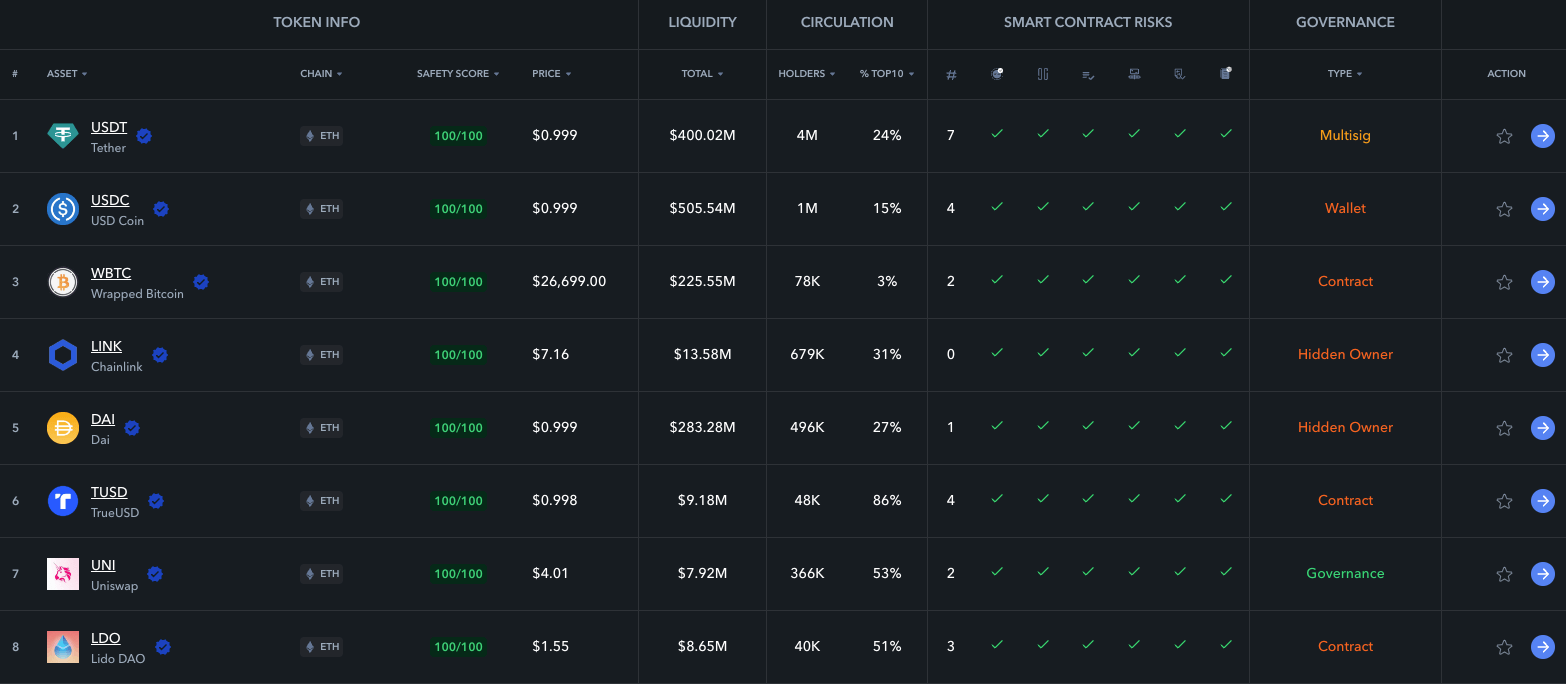
This collaboration brings together De.Fi’s revolutionary security solutions and a large variety of crypto assets (over 5,000+) to provide an enhanced layer of protection for anyone interacting with the world of DeFi. It uses data from over 1 million smart contracts and more than 12 million different issue categories.
With this in mind, it’s clear that De.Fi is your best choice for a web3 SuperApp that covers both DeFi portfolio tracking as well as onchain security. Create your De.Fi profile today and join the crypto revolution!
October 2025 saw a total of $38.63 million lost across nine distinct security incidents in both centralized and decentralized platforms.
The third quarter of 2025 marked yet another turbulent period for the DeFi and wider crypto ecosystem, with $434,124,000 lost to exploits, scams, and security failures across both centralized and decentralized platforms.
June 2025 witnessed another alarming month for Web3 security, with a total of $114,768,000 lost during 11 separate attacks
May 2025 saw both DeFi and CeFi security once again under attack, with $275,953,000 lost across just 8 recorded incidents
April 2025 witnessed a large escalation in exploit volume and value, with a massive $5,919,684,000 being stolen in 10 confirmed events.
Q1 2025 marked one of the worst quarters in blockchain exploit history, with total recorded losses topping $2,052,584,700 across 37 incidents
© De.Fi. All rights reserved.