The whole of February 2022 has captured a few unfortunate but interesting activities in fraud and money laundering in the DeFi space. At the end of this month, our specialists counted a whopping 22 Rekt cases with a total amount loss of more than $376,331,638.
Reminding, that the most dramatic one, was the Wormhole hack, and it takes 2nd place on De.Fi Rekt Database.
Now, let’s make a recap of the top 10 Rekt Stories by funds lost in February.
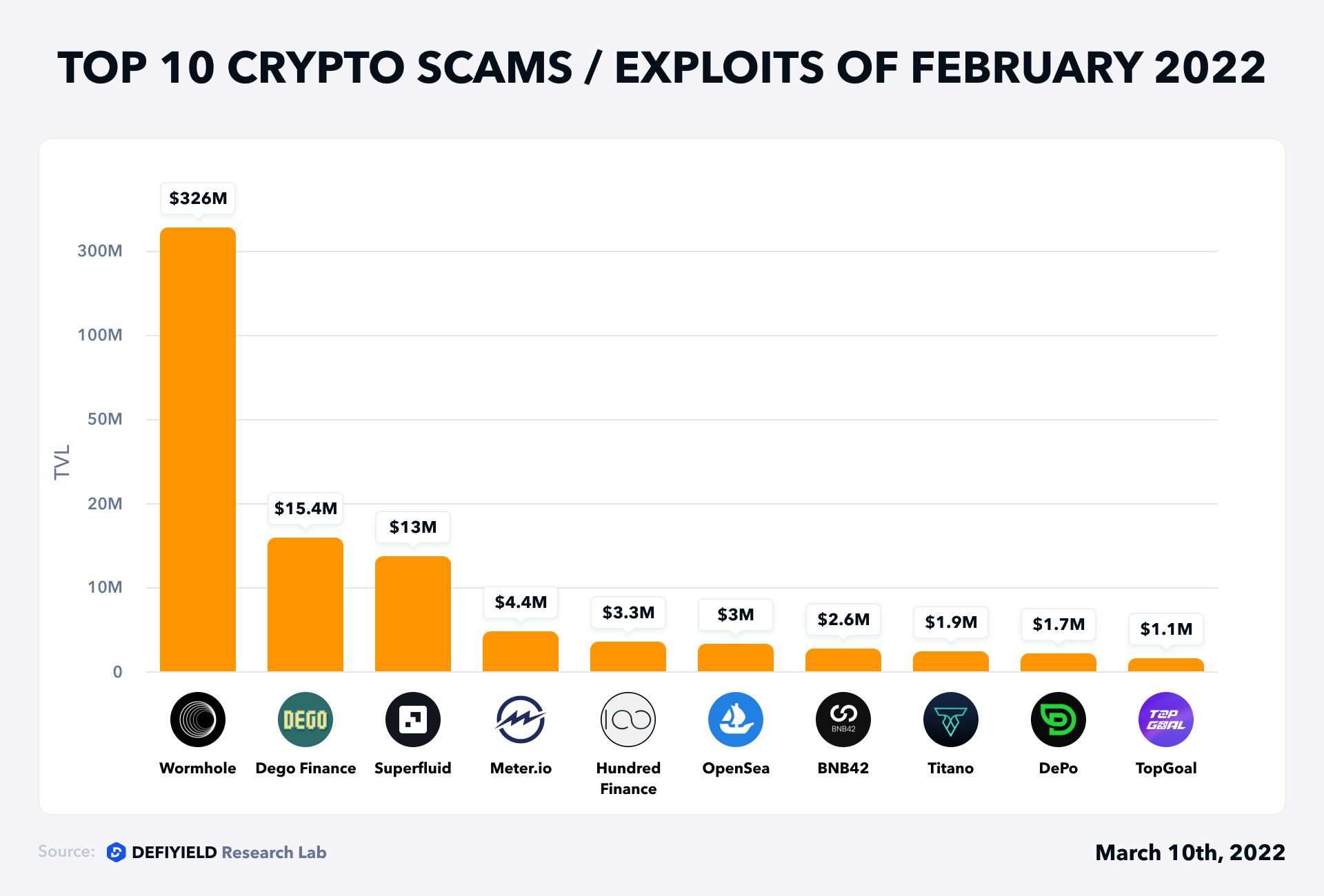
1. TopGoal — $1.1m Lost (Access Control, Feb 16)
The TopGoal team at their appeal stated that the operational wallet was attacked and compromised. All users’ assets, including NFTs and TMTs, remained safe. However, once the hacker received access to the wallet, he has transferred a total of 4,809,984 TMT from TopGoal operation hot wallet to address 0x7F0D082D08874A57110c73a8853967e7C19D1a6e. Then the hacker swapped all stolen TMTs into over 2600 BNB from PancakeSwap and used the Tornado Cash mixer to transfer BNB out of the address.
More details on Rekt Database =>
2. DePo — $1.7m Lost (Access Control, Feb 4)
CEO of DePo protocol at his appeal stated that a previous senior employee of DePo executed emergencyRewardWithdraw() function at several transactions, examples:
https://etherscan.io/tx/0xd47dfe0b9df5d7f7796d54ac7dd4e118a236074b3d512ef5fd05a27a4957a6b7
https://etherscan.io/tx/0x8ac9a06a8de7b5167cf94388d761797955b1081726bf3d612ed977ce1a4495a5
https://etherscan.io/tx/0x287a7c336ba148c5f562a5852e1dba0820a65e7a6074c085df2d02eeb8b4e29b
By doing this, he stole DEPO tokens from the staking rewards wallets, sold tokens on Uniswap, and deposited ETH into the Tornado Cash mixer
More details on Rekt Database =>
3. Titano — $1.9m Lost (Access Control, Feb 14)
The contract owner of MultipleWinners contract called _awardTickets() function to mint 32,000,000 TicketTitano at transaction:
https://bscscan.com/tx/0x848280d0e054b0f1a04356bdf29cff390d9a982a6f709ae5df45a6f32f5bce6c
The owner called StakePrizePool.withdrawInstantlyFrom() to burn TicketTitano tokens and withdraw Titano tokens.
The owner sold the withdrawn Titano tokens for 4,828 BNB in several transactions:
https://bscscan.com/address/0xad9217e427ed9df8a89e582601a8614fd4f74563#internaltx
Received BNB were distributed between several external wallet.
More details on Rekt Database =>
4. BNB42 — $2.6m Lost (Exit Scam, Feb 14)
The address, involved in the scam, deployed the unverified contract which contained withdraw() function that allows only the owner to withdraw the entire total BNB (eth.balance(this.address) wei) to the owner’s address.
The contract deployer invoked withdraw() to transfer 6,445.42 BNB onto own address at:
https://bscscan.com/tx/0x749215ebe457aa681194684401257fe8fb44daecb9f50a077b12c71e83cf9414
Stolen funds were distributed to a bunch of external addresses and deposited into the Tornado Cash mixer.
More details on Rekt Database =>
5. OpenSea — $3m Lost (Access Control, Feb 20)
Recently, OpenSea several times was under security breaches for different reasons. This time, the malicious actor sent emails to OpenSea users, which contained information about fake migration to the new contract. In total, 17 users became victims of email fishing.
The malicious actor’s address:
https://etherscan.io/address/0x3E0DeFb880cd8e163baD68ABe66437f99A7A8A74
Stolen NFTs list:
https://docs.google.com/spreadsheets/d/1XQNIXuAl2E1XO_cP8pm_vbzskI_Pka4E5sizfcrLITM/edit#gid=0
Stolen NFTs were sold out on LooksRare marketplace, the example transactions:
https://etherscan.io/tx/0xd910c67a55618e0db6fdbcd9647b7eedebed0bbb098bdffc2a3276856f989221
https://etherscan.io/tx/0x9a9bb48a9a9b6c3bbd98f4786b85ec15e4fe78acf946c8ff09201c1a8371e8ee
https://etherscan.io/tx/0x70c8622cea709c551de8135b71ce9ec0cb15a3cb835957d42937edf44ee360f9
More details on Rekt Database =>
Search Our REKT Datatbase for Rug Pulls, Scams and Attacks: Learn How Here 👇
6. Hundred Finance — $3.3m Lost (Exploit, Feb 6)
Hundred Finance lending protocol was affected due to the Meter bridge exploit:
https://twitter.com/HundredFinance/status/1490394875459682309
The exploiter of Meter.io dumped BNB.bsc assets several times at:
https://moonriver.moonscan.io/tx/0x14dc9ed2bd8f2e6e2aef00d82001eccdc07037373adb6de7f14e5e45469be504
https://moonriver.moonscan.io/tx/0x4afa30ee32b139918b02aa0932b89ca3d27d71e08bcb243cd508c48848ab63bf
https://moonriver.moonscan.io/tx/0x5a87c24d0665c8f67958099d1ad22e39a03aa08d47d00b7276b8d42294ee0591
https://moonriver.moonscan.io/tx/0x9d6623969cf711a8327c7e966568870b583c0b9b900173e5f6a5746196cf966d
https://moonriver.moonscan.io/tx/0x4e2a54f3b3035573ffdafecdf7cd7837b6672d498bf3a560a4f8dd57322a2156
https://moonriver.moonscan.io/tx/0xbe0610f89e1b1a705d2524016f3b577293f51911d08a56a0149a37fb57f601ad
That resulted in the local depreciation in the price of BNB.bsc. Different external addresses were able to purchase BNB.bsc at a reduced price and use these tokens as collateral at the global Chainlink price to borrow uncompromised assets on Hundred Finance. As a result, MIM and FRAX tokens were impacted.
More details on Rekt Database =>
7. Meter.io — $4.4m Lost (Exploit, Feb 6)
The attacker minted a substantial amount of BNB and WETH tokens, draining the bridge reserve of its BNB and wETH before all bridge transactions could be halted by Meter. This case also impacted the Hundred Finance on Moonriver.
Meter_io Passport is a fork of ChainSafe’s ChainBridge, but with one change introduced to the deposit method of the ERC20 Handler.
The extended code had a wrong trust assumption which allowed the hacker to call the underlying ERC20 deposit function to fake a BNB or ETH transfer.
Stolen funds were deposited into Tornado Cash mixer on Ethereum:
https://bloxy.info/txs/transfers_from/0x8d3d13cac607b7297ff61a5e1e71072758af4d01?currency_id=1
More details on Rekt Database =>
8. Superfluid — $13m Lost (Exploit, Feb 8)
The attacker’s wallet:
https://polygonscan.com/address/0x1574f7f4c9d3aca2ebce918e5d19d18ae853c090
The transaction behind the exploit:
https://polygonscan.com/tx/0xf9b4a3a64861e9feb27e21f3fc9c85e6d2851b8a097c71910585e3d7f374d8d8
The attacker exploited Superfluid’s host contract by passing in faulty calldata, which allowed them to create distribution indexes spoofing several different accounts that held Super-tokens. This vulnerability enabled the attacker to move funds from Superfluid user wallets to exchanges on Polygon and swap to ETH. The funds currently sit in the attacker’s wallet.
In total, 11,008 MATIC, 1,507,931 MOCA, 28 ETH, 39,357 sdam3CRV, 19,387,874 QI, 44,581 SDT, 23,653 STACK and 562,834 USDC were stolen by the attacker. At the time of writing, over 2,700 ETH is sitting in the attacker’s wallet, as well as 500,000 MOCA.
More details on Rekt Database =>
9. Dego Finance — $15.4m Lost (Access Control, Feb 9)
The address which provided liquidity both on Uniswap and PancakeSwap was attacked and compromised. As a result, the hacker withdrew and transferred all funds on his external wallet and removed liquidity.
The hacker’s address:
https://bscscan.com/address/0x118203b0f2a3ef9e749d871c8fef5e5e55ef5c91
Tornado deposits:
https://etherscan.io/tx/0x152f91e24332bc47dcd1e50a034664a040e10b6055b35f86b430b51e62fa5a2f
https://etherscan.io/tx/0x0c84d2c6c4fdfc61ca08f1c49f89fc982362f6a41a981986abadac3568a771dd
https://etherscan.io/tx/0x59dc8303669025a4918bc55f46acd7d9eaea6ea9a9fb115c54ffff8fedbc8e3a
https://etherscan.io/tx/0x59871d498700923d6a7df582b4d3d0402e50c13fd9ccfa9f668c726dc453fb73
DEGO team tries to contact the hacker with the message:
“Hi I’m from Dego team, let’s have a chat?”
https://bscscan.com/tx/0x065fa8782312e9786a458fc2345f4c7ef49267630c7f90a900999ce45ae4ced5
More details on Rekt Database =>
10. Wormhole — $326m Lost (Exploit, Feb 2)
Wormhole case places 2nd by the funds lost according to the Rekt Database. The best final of this huge security breach ended well for users: the Wormhole team officially stated that they added their own funds to recover all losses
https://twitter.com/wormholecrypto/status/1489232008521859079
We have dedicated a separate article to this case, follow the link and check it out
https://blog.de.fi/wormhole-exploit-the-second-largest-defi-hack-ever-237ed5c81670
As always, stay safe and DYOR!
For more De.Fi updates you can visit us at:
🌐 Website | 📱 Telegram | 🐦Twitter
Check our guides:
Tezos Ultimate Yield Farming Guide [Infographics]
Solana Network Ultimate Yield Farming Guide [Infographics]
Fantom Network Ultimate Yield Farming Guide [Infographics]
Huobi ECO Chain Ultimate Guide for Yield Farming
Polygon Network Ultimate Guide for Yield Farming
Binance Chain Ultimate Guide for Yield Farming
EOS Ultimate Yield Farming Guide
Arbitrum Ultimate Guide [Infographics]
The Ultimate Yield Farming Guide For Terra Blockchain (Luna) [Infographics]
The Ultimate Guide to Avalanche Network
Ultimate Guide to Yield Farming on Harmony (with infographics)
Ultimate Guide to Tron Network [Infographics]
The Ultimate Yield Farming Guide For Moonriver Network
The Ultimate Yield Farming Guide For Celo
The Ultimate Yield Farming Guide For KuCoin Community Chain
The Ultimate Yield Farming Guide For NEAR Protocol
And join us on twitter and telegram!
Good luck in farming!