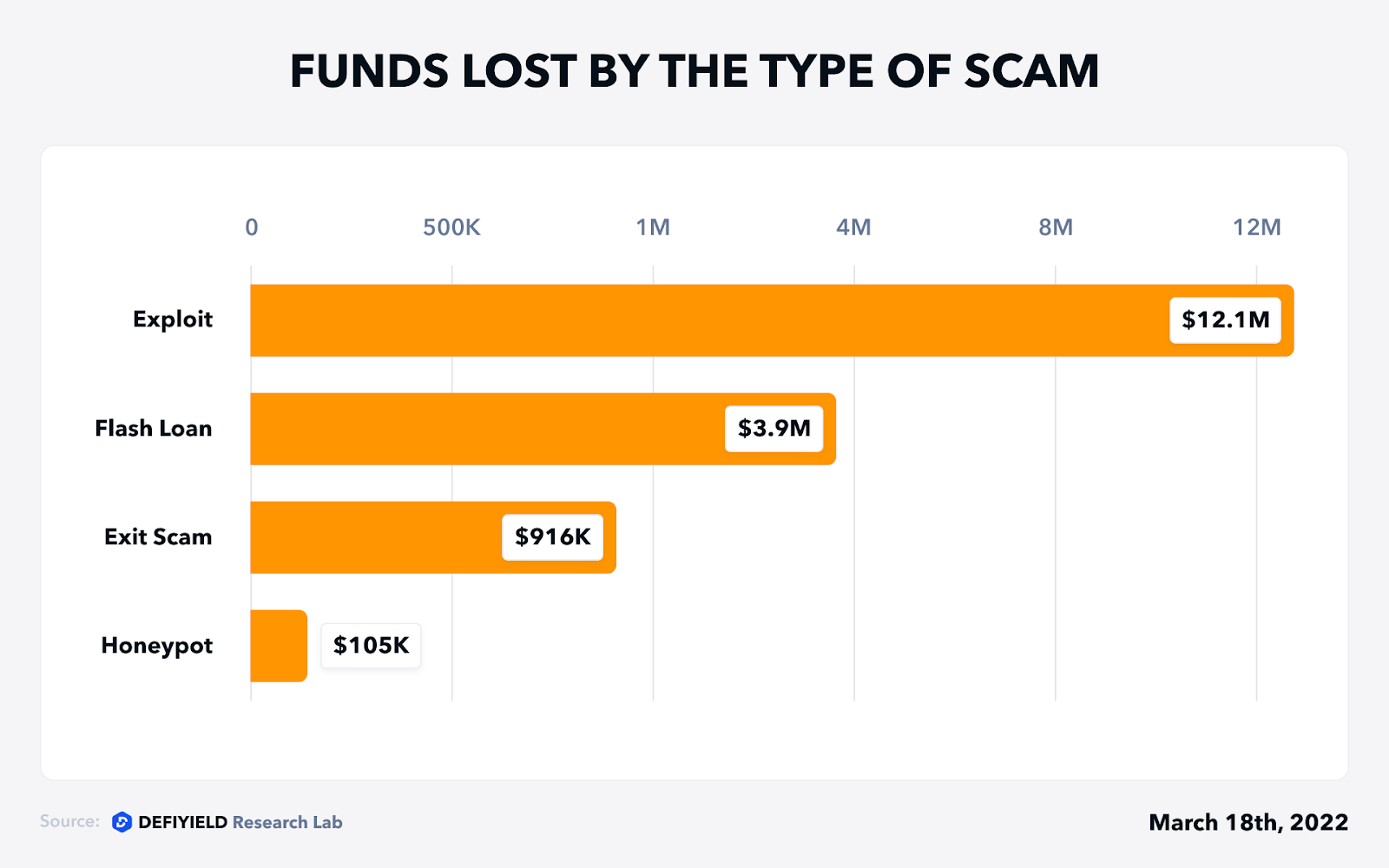
Starting from March 1st and until the half of the month, De.Fi Rekt Database has covered 13 Rekt cases with a total amount loss of more than $20 million. The security breaches were mainly around lending protocols, while rug pulls and scams had the root of fraud presales.
Let’s take a quick look at all of them and make a small recap of what has happened.
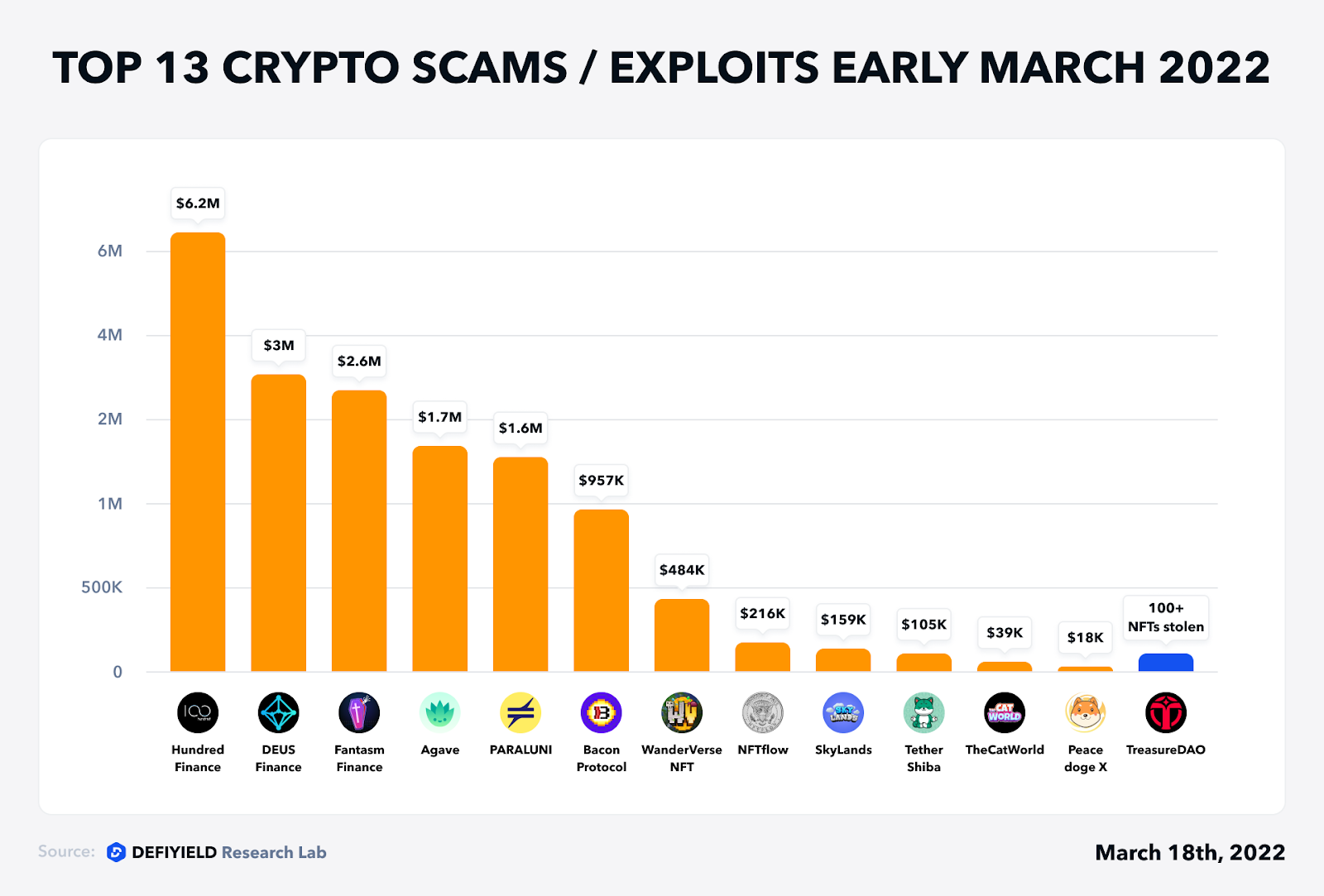
1. Hundred Finance — $6.2m Lost (Exploit, Mar 15)
The attacker’s address:
https://blockscout.com/xdai/mainnet/address/0xD041Ad9aaE5Cf96b21c3ffcB303a0Cb80779E358/transactions
Using flash loans as collateral, the attacker(s) layered multiple borrow functions within one another, increasing the amount borrowed before the protocol could update the debt balance. Repeating this approach resulted in borrowing assets that were significantly more valuable than the collateral provided.
Stolen funds were bridged to Ethereum and deposited into Tornado Cash mixer:
https://etherscan.io/txs?a=0xd041ad9aae5cf96b21c3ffcb303a0cb80779e358
This is the second case when Hundred Finance became a victim
More details on Rekt Database =>
2. Agave — $1.7m Lost (Exploit, Mar 15)
The attacker’s address is the same that attacked Hundred Finance:
https://blockscout.com/xdai/mainnet/address/0xD041Ad9aaE5Cf96b21c3ffcB303a0Cb80779E358/transactions
The attacks were made possible due to the xDAI token’s architecture, which includes the function callAfterTransfer(), which creates a reentrancy vulnerability. The same vector was used to attack Agave.
More details on Rekt Database =>
3. DEUS Finance — $3m Lost (Flash Loan, Mar 15)
The attacker’s address:
https://ftmscan.com/address/0x1ed5112b32486840071b7cdd2584ded2c66198dd
The transaction behind the attack:
https://ftmscan.com/tx/0xe374495036fac18aa5b1a497a17e70f256c4d3d416dd1408c026f3f5c70a3a9c
The hack is made possible due to the flash loan-assisted manipulation of the price oracle that takes the price from the pair of StableV1 AMM — USDC/DEI. The attacker’s steps:
- Flash loaned 9,739342 DEI via SPIRIT-LP_USDC_DEI.
- Flash loaded 24,772,798 DEI out of the sAMM-USDC/DEI pair (used as price oracle to calculate the collateral value).
- Liquidated users.
- Repaid the borrowed 24,772,798 DEI to the sAMM-USDC/DEI pair.
- Burnt the liquidated LP token to get 5,218,173 USDC + 5,246,603 DEI.
- Swapped 5,218,173 USDC to 5,170,594 DEI.
- Repaid the flash loan with 3,001,552 DEI as hack profit.
More details on Rekt Database =>
4. Fantasm Finance — $2.6m Lost (Exploit, Mar 9)
The exploiter’s address:
https://ftmscan.com/address/0x47091e015b294b935babda2d28ad44e3ab07ae8d
The exploiter’s steps:
- Deployed contract to trigger the exploit
- Minted XFTM by input only FSM token without entering any FTM
- Collected XFTM token
- Sold XFTM token to FTM
- Bought more FSM and repeated the first step to get a larger amount of FTM
- Sold all his FTM for ETH and bridged these ETH to Ethereum via Celer Bridge
- Deposited stolen funds into Tornado Cash mixer:
That contract exploited the error in Fantasm’s Pool contract where the developer missed the condition checking for the minimum amount of input FTM when minting XFTM.
More details on Rekt Database =>
5. PARALUNI — $1.6m Lost (Exploit, Mar 13)
The exploiter:
https://bscscan.com/address/0x94bc1d555e63eea23fe7fdbf937ef3f9ac5fcf8f
The example transaction behind the exploit:
https://bscscan.com/tx/0x70f367b9420ac2654a5223cc311c7f9c361736a39fd4e7dff9ed1b85bab7ad54
The hack is made possible due to a reentrancy bug (introduced by the use of a crafted token contract) in the depositByAddLiquidity() function, which somehow doubles the credits the hacker is able to claim. The result gains were swapped via PancakeSwap.
More details on Rekt Database =>
6. Bacon Protocol — $957k Lost but restored (Flash Loan, Mar 5)
The exploiter’s address:
https://etherscan.io/address/0x7c42f2a7d9ad01294ecef9be1e38272c84607593
The transaction behind the exploit:
https://etherscan.io/tx/0x7d2296bcb936aa5e2397ddf8ccba59f54a178c3901666b49291d880369dbcf31
The hack is made possible due to a reentrancy bug in the lend() routine so that the exploiter can get more lending credits via re-entering the lend() routine.
The contract exploit led to sending 957,166 USDC out of the protocol. A second exploit was prevented by a white hat group who returned the 34,232 USDC they received. These changes caused the price of bHOME to temporarily unpeg and decrease to $0.86.
As of March 6th, the BaconCoin team has deposited 991,441 USDC into the BaconCoin multi-sig that will be used to recapitalize the protocol:
https://etherscan.io/tx/0xf13823eccb9debdfc41cbd4a36430fa727271e74fca27caadadb967fd5bdcdc7
https://etherscan.io/tx/0x23ccdd965c1c376d229c121cc1ffe113a6dac1ecc6a6b16ae4af92d8428dc668
7. WanderVerse NFT — $484k Lost (Exit Scam, Mar 8)
The project was holding an NFT minting event.
The contract deployer withdrew all deposited ETH after the NFT mint:
https://etherscan.io/tx/0x5b75f9bdc8a480c35976b1098dd9afddd51bc061a1b3c7f5ea0b257c6adfad79
https://etherscan.io/tx/0x7cdb35a1bf723c6bb395b5bffd27a60fa965b3ada33a3d3ed7a76ec755440414
More details on Rekt Database =>
8. NFTflow — $216k Lost (Exit Scam, Mar 14)
The project was holding an NFT presale event.
The contract deployer withdrew all deposited ETH at:
https://etherscan.io/address/0x5cad06e17452179abe3ee7f99ce649d16d059616#internaltx
More details on Rekt Database =>
9. SkyLands — $159k Lost (Exit Scam, Mar 7)
Here begins a series of scams that carried out sales on the PinkSale platform:
https://www.pinksale.finance/#/launchpad/0x5a626dD78FFba94237B00Fd354Ff328EB1c9aD82?chain=BSC
All gathered funds 417.31 BNB were withdrawn by the contract deployer:
https://bscscan.com/address/0xad8970026ea0f76ffdf758c61c5af6d383341392#internaltx
More details on Rekt Database =>
10. TetherShiba — $105k Lost (Honeypot, Mar 7)
The project token identifies as honeypot:
https://honeypot.is/?address=0xB463D04DA3CCb35093CCe292212638a16A1Cd934
The contract deployer enabled the blacklist for users that prevents selling the token:
https://bscscan.com/tx/0x46b8d20fe5bb08dc29bd9472330c00c744eb3f222a0e11b7a73cf0644b1e30d6
Tokens were sold by the contract deployer in multiple transactions:
https://bscscan.com/address/0x1dc2607e547e99d4de192c589a178c0c353f6b89#tokentxns
More details on Rekt Database =>
11. TheCatWorld — $39k Lost (Exit Scam, Mar 3)
The project was holding presale on the PinkSale platform:
https://www.pinksale.finance/#/launchpad/0xC2A65ef69Ae72BD2c66A4158516A61E3f1EF3cfd?chain=BSC
The contract deployer withdrew liquidity from the sale contract:
https://bscscan.com/tx/0xbe7eb82b44b5356d094fea2764f976cd550a6e72e1c14818b25d248a30c7e3d4
More details on Rekt Database =>
12. Peace doge X — $18k Lost (Exit Scam, Mar 6)
The project was holding a presale on PinkSale:
https://www.pinksale.finance/#/launchpad/0x1b3206aF7834c7A4cB1301CAC1CEB2834543992f?chain=BSC
The contract deployer withdrew liquidity at:
https://bscscan.com/tx/0x0ccef5b68196bfb74f73363a1a91c3bb720ad1278bcbe431ac115a536f3fc140
Stolen funds were transferred out to the external address and deposited into Tornado Cash mixer:
https://bscscan.com/tx/0xef589ed5aef92e4e20c22be683d1e07d6badf9048517c583207144fa11f45d8d
More details on Rekt Database =>
13. TreasureDAO — Exploit, Mar 3
The exploiter’s address:
https://arbiscan.io/address/0x9b1acd4336ebf7656f49224d14a892566fd48e68
The example of the transaction:
https://arbiscan.io/tx/0x37222d3ad371dff2d3f3ae1c788d1cc4ad69e9f1839776830726485119a89269
The protocol was exploited in several transactions, leading to more than 100 NFTs being stolen from different collections of Treasure Marketplace.
The exploiter’s steps:
- Called buyItem() with valid NFT token and NFT ID, but with the invalid 0 quantity
- Treasure Marketplace sells the NFT but charges 0 MAGIC (due to 0 quantity)
The hack is made possible due to a bug in distinguishing ERC721 and ERC1155 in buyItem(), which miscalculates the price of ERC721 as ERC1155 with the given 0 quantity.
As always, stay safe and DYOR!
For more De.Fi updates you can visit us at:
🌐 Website | 📱 Telegram | 🐦Twitter
Check our guides:
Tezos Ultimate Yield Farming Guide [Infographics]
Solana Network Ultimate Yield Farming Guide [Infographics]
Fantom Network Ultimate Yield Farming Guide [Infographics]
Huobi ECO Chain Ultimate Guide for Yield Farming
Polygon Network Ultimate Guide for Yield Farming
Binance Chain Ultimate Guide for Yield Farming
EOS Ultimate Yield Farming Guide
Arbitrum Ultimate Guide [Infographics]
The Ultimate Yield Farming Guide For Terra Blockchain (Luna) [Infographics]
The Ultimate Guide to Avalanche Network
Ultimate Guide to Yield Farming on Harmony (with infographics)
Ultimate Guide to Tron Network [Infographics]
The Ultimate Yield Farming Guide For Moonriver Network
The Ultimate Yield Farming Guide For Celo
The Ultimate Yield Farming Guide For KuCoin Community Chain
The Ultimate Yield Farming Guide For NEAR Protocol
The Ultimate Yield Farming Guide For Algorand
The Ultimate Guide For Elrond
The Ultimate Guide For Polkadot
The Ultimate Yield Farming Guide For Cosmos
And join us on twitter and telegram!
Good luck in farming!